🛡️ Managing Azure Storage Accounts: Secure, Scalable, and Resilient Data Solutions with Blob Storage & Azure Files

In today’s cloud-first world, businesses need storage solutions that are not just scalable—but secure, highly available, and resilient to failure. Azure Storage Accounts offer exactly that: a unified platform for storing diverse data types—blobs (Binary Large Object), files, queues, tables, and disks—accessible globally over HTTP/HTTPS with a unique namespace.
Whether you’re backing up a public website, managing internal documents, or enabling shared access across departments, Azure’s storage services provide the flexibility and control needed to meet enterprise demands. With built-in redundancy options like LRS, ZRS, GRS, RA-GRS and GZRS, your data is protected against local failures and regional outages. And with encryption at rest, network isolation, and identity-based access, security is baked into every layer.
This hands-on guide walks through five real-world scenarios, each mapped to a specific Azure storage configuration:
🧪 Provisioning Storage for IT Team Training & Development
This solution requires a low-cost, flexible storage solution for large files like software test builds and training videos. Using Azure Blob Storage with Locally Redundant Storage (LRS) fits the bill perfectly. This setup is ideal because it’s a cost-effective option that’s designed for data that doesn’t need a backup. Plus, all data transfers are kept secure using TLS 1.2 encryption
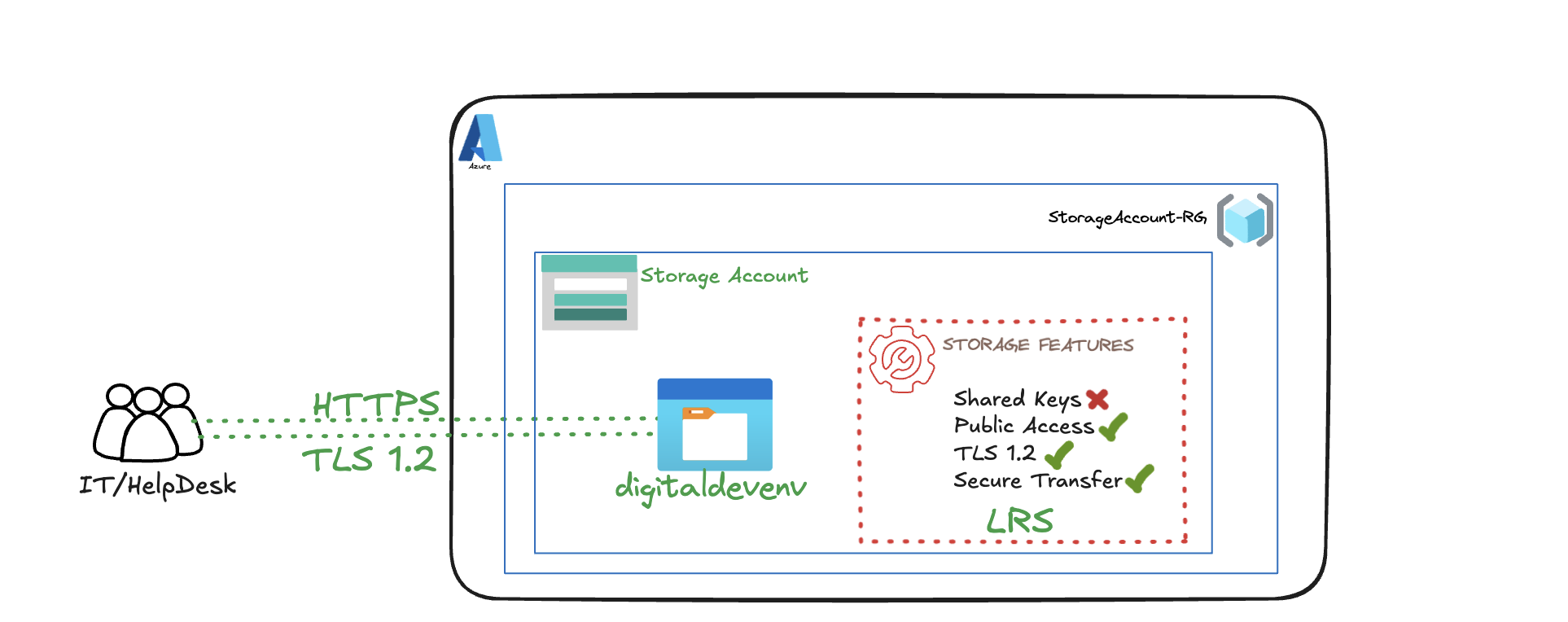
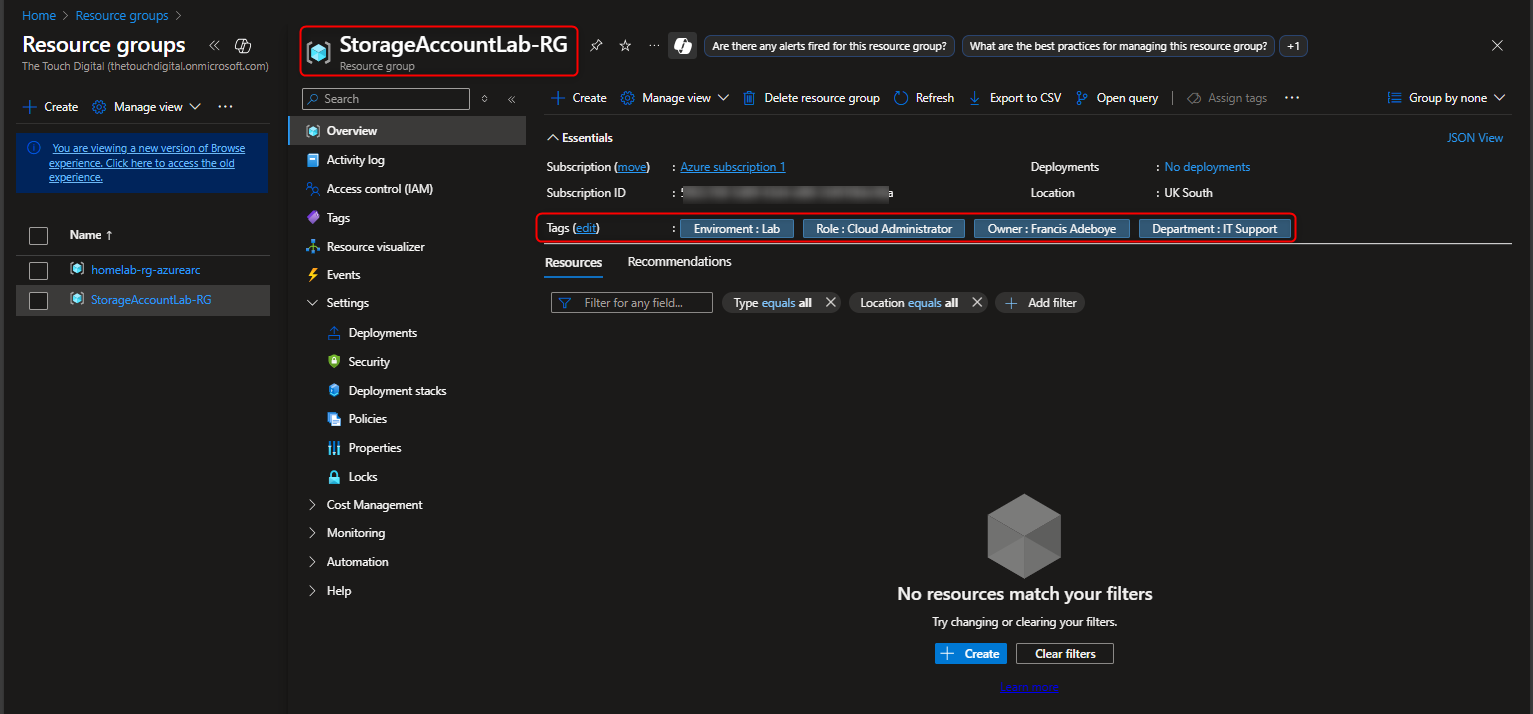
- Create a Resource Group Container for this project: StorageAccountLab-RG
I’ll be using my existing Resource Group for the Demonstration
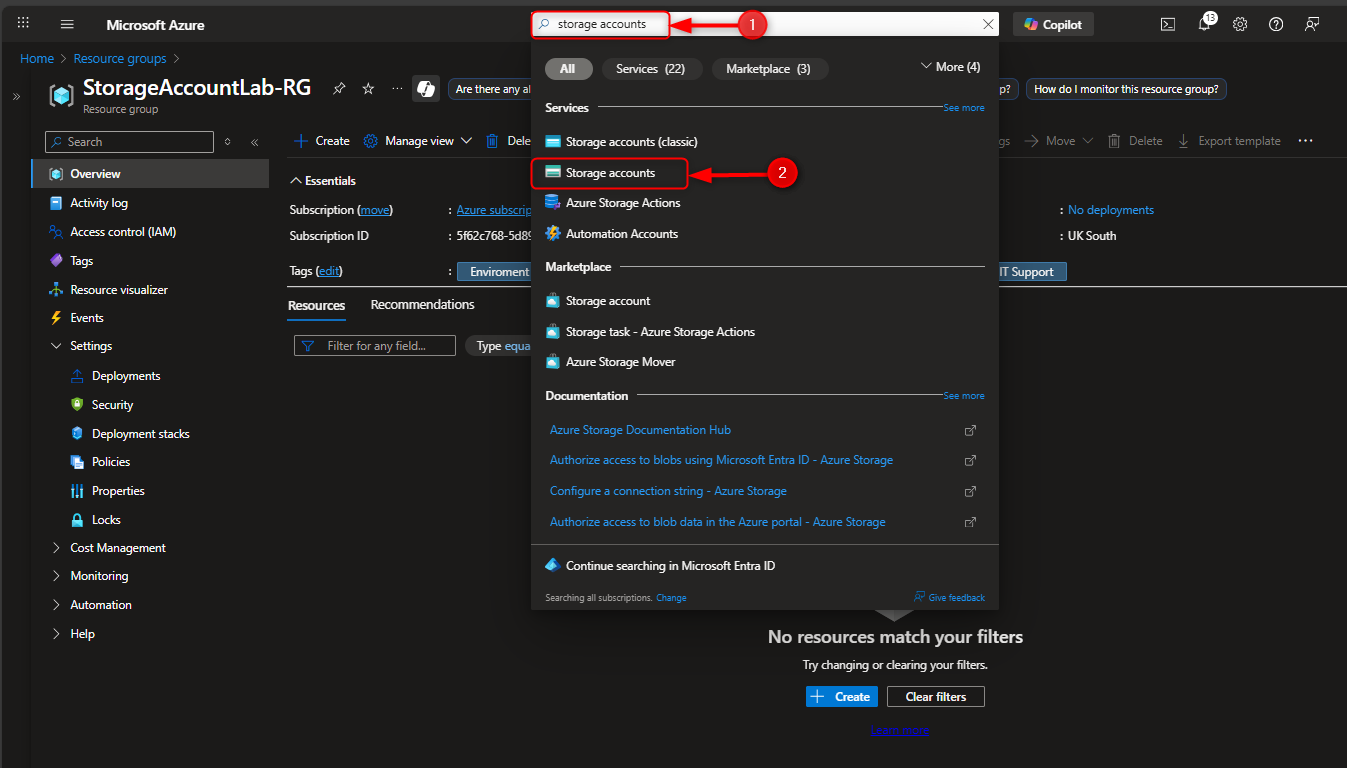
- Deploy a Storage Account to support testing and training for the IT Team.
Use the search Bar: Storage Accounts -> Create
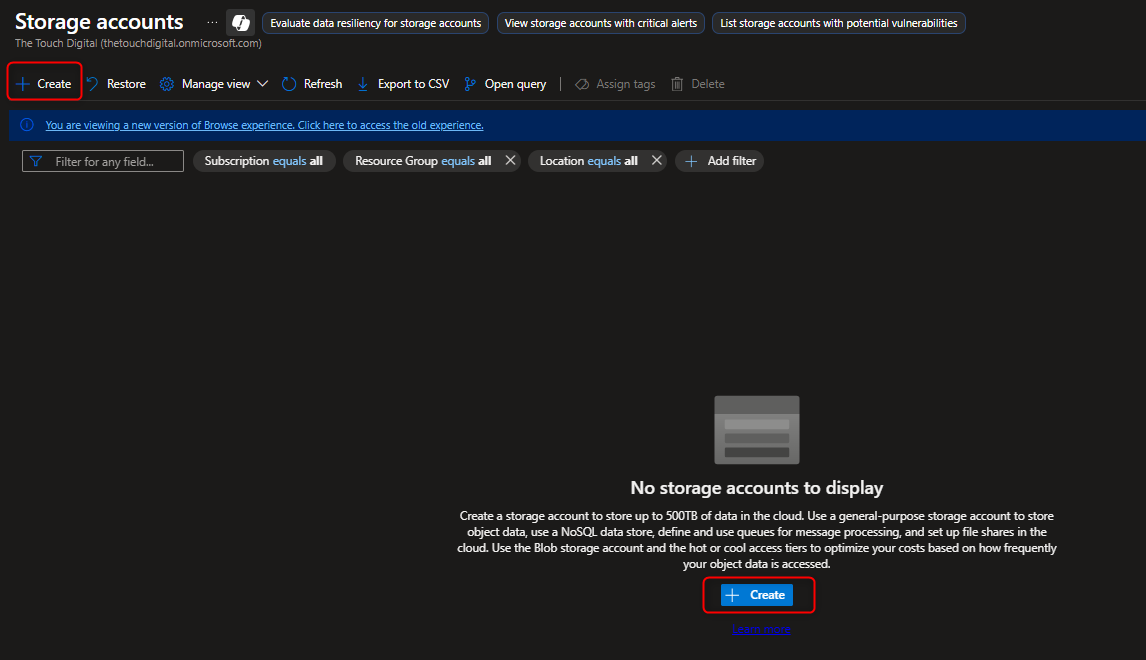
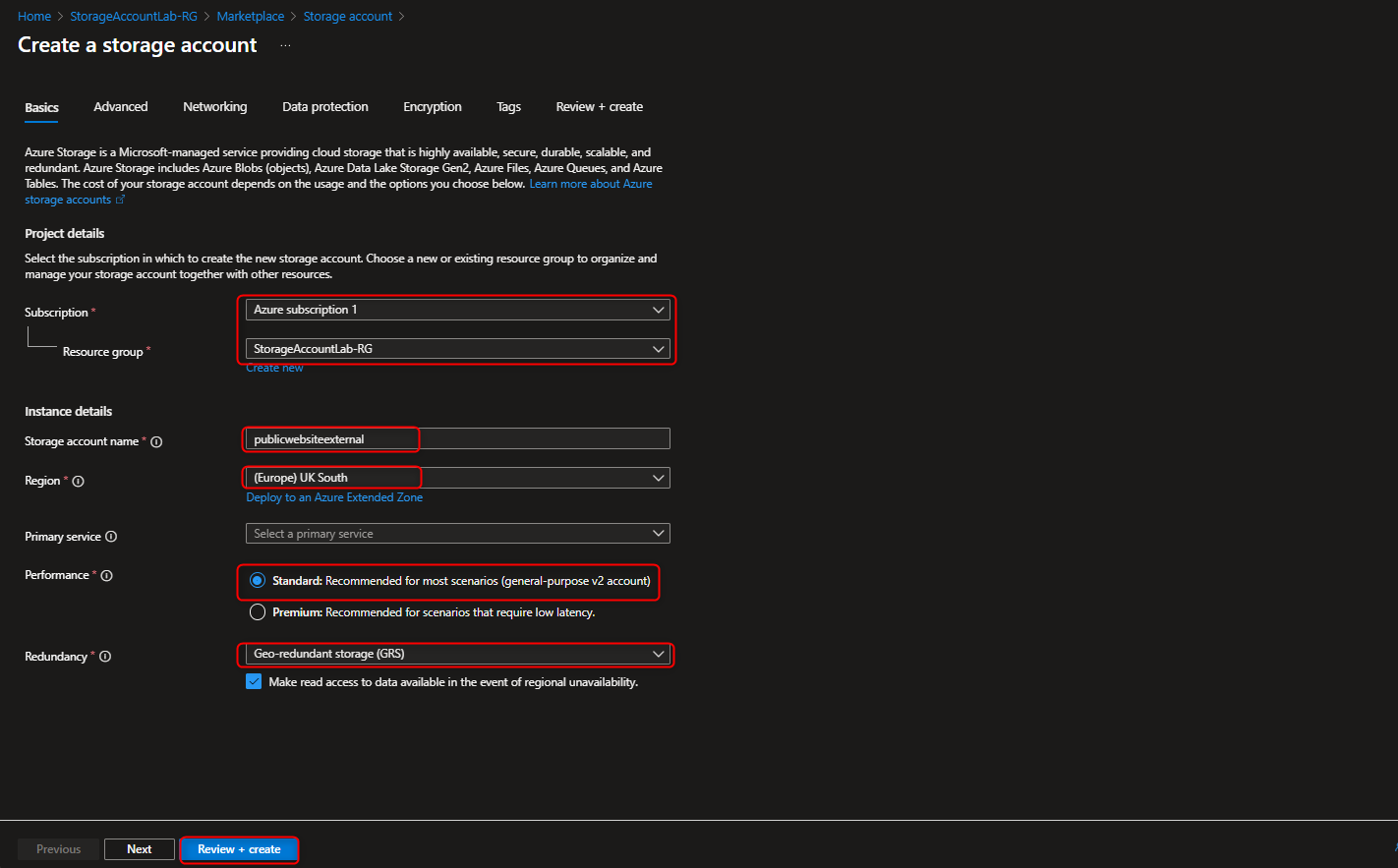
Select Subscription -> Resource Group -> Storage Account Name ( Globally Unique) -> Standard -> Locally Redundant Storage ( LRS ) -> Review+Create -> Go to Resources
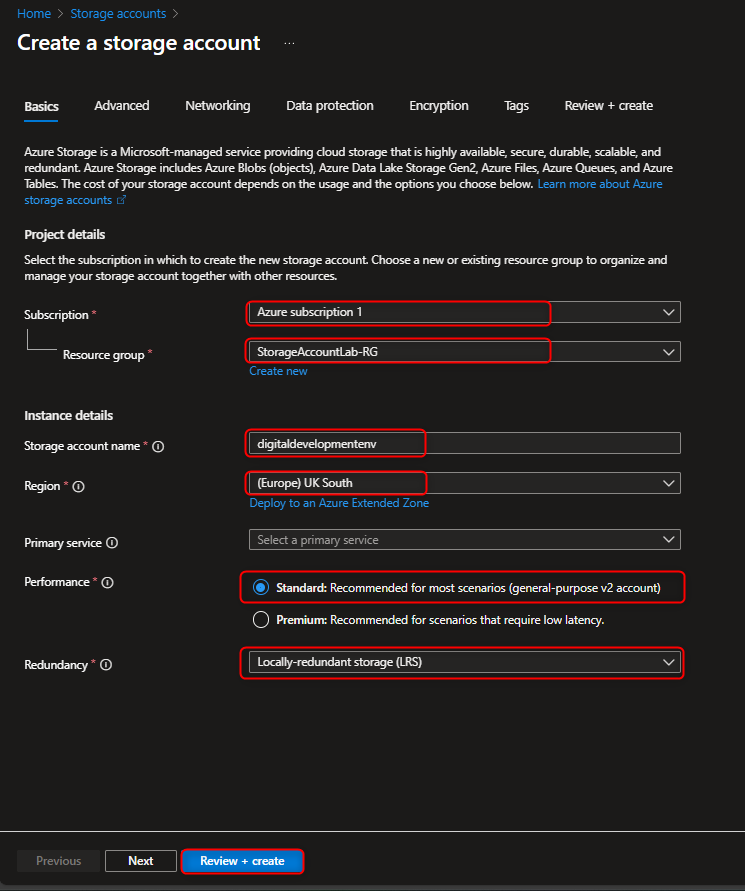
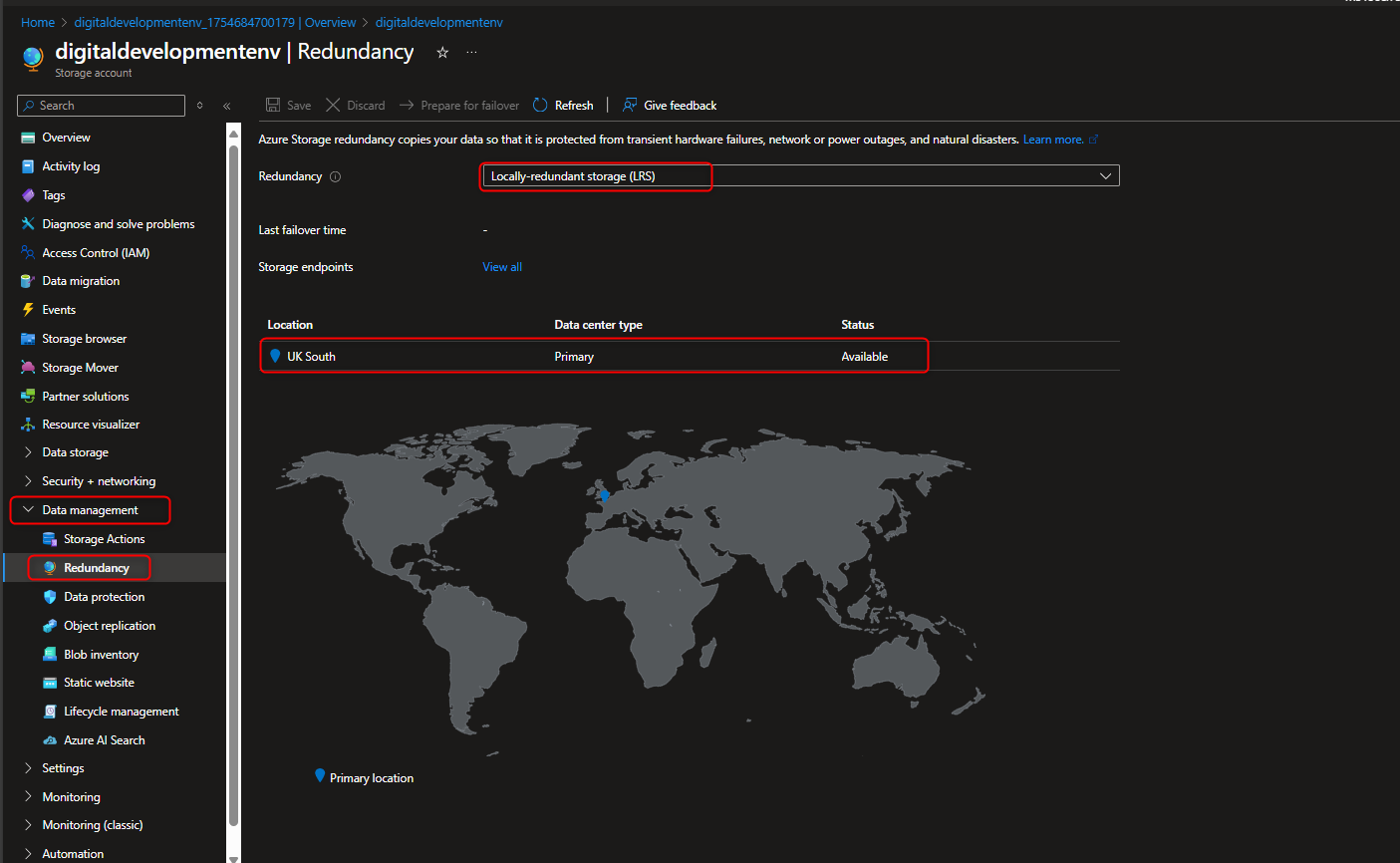
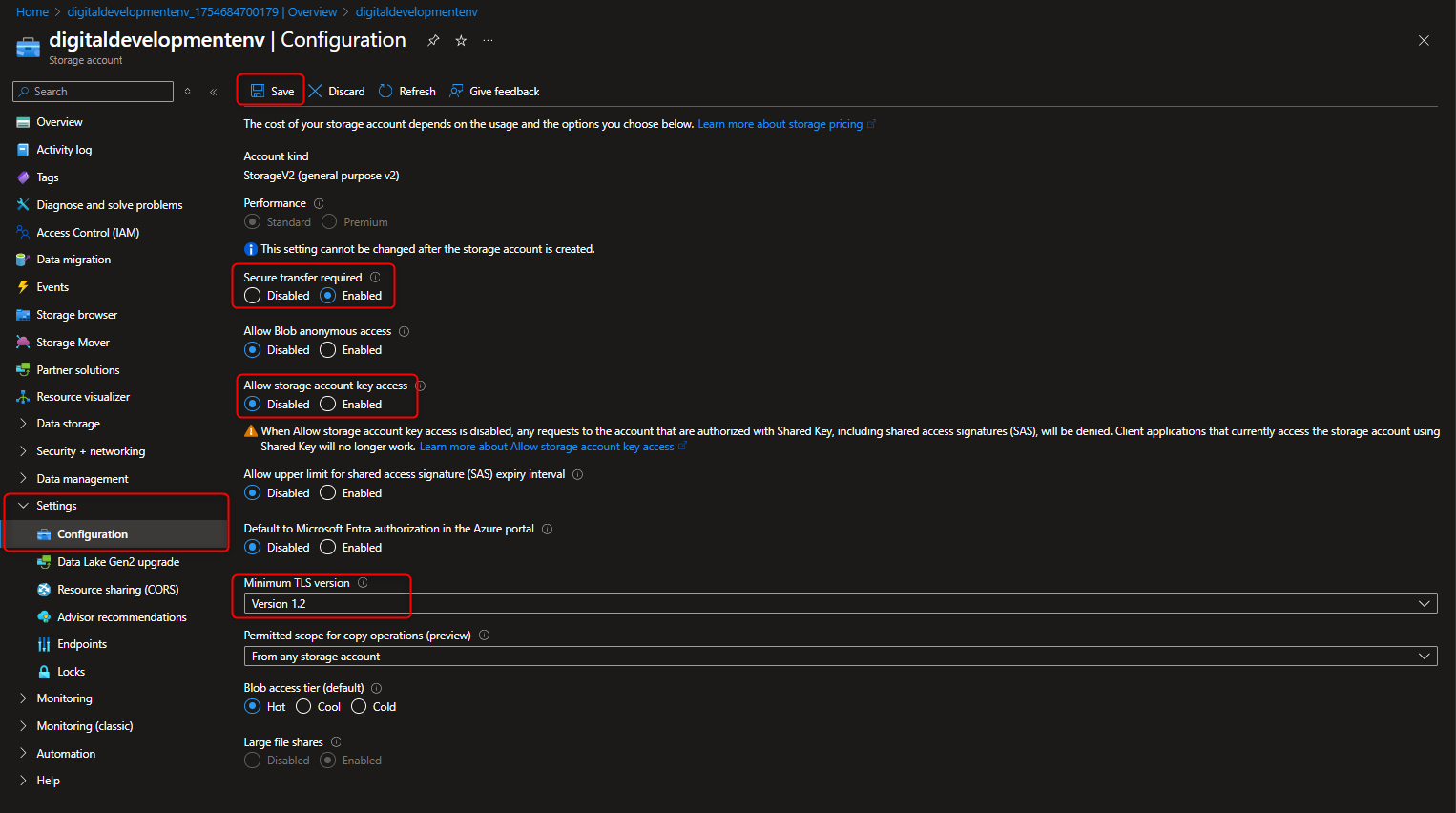
- Configure simple settings for Data Redundancy , Secure Transfer , Transport Layer Security (TLS) v1.2 , Shared Keys & Public Access.
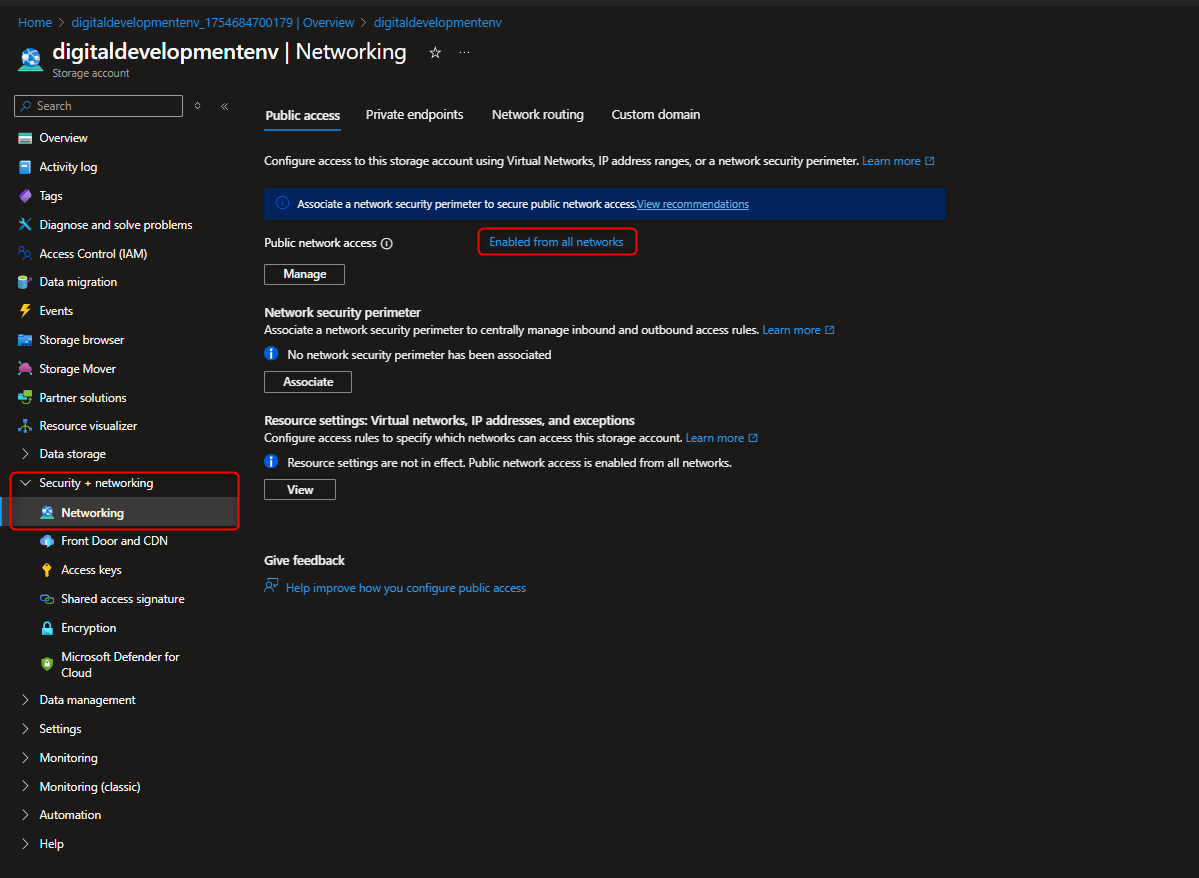
🌐 Public Web Storage for Product Delivery to Global Customers
This task sets up Azure Blob Storage to host a public company website container with the intent to deliver product images and content to global users. We’ll create a highly available storage account with RA-GRS redundancy, configure anonymous access for fast public delivery, and enable features like soft delete and versioning to protect and manage content. The goal is to ensure quick load times, easy access, and resilience—without requiring users to log in.
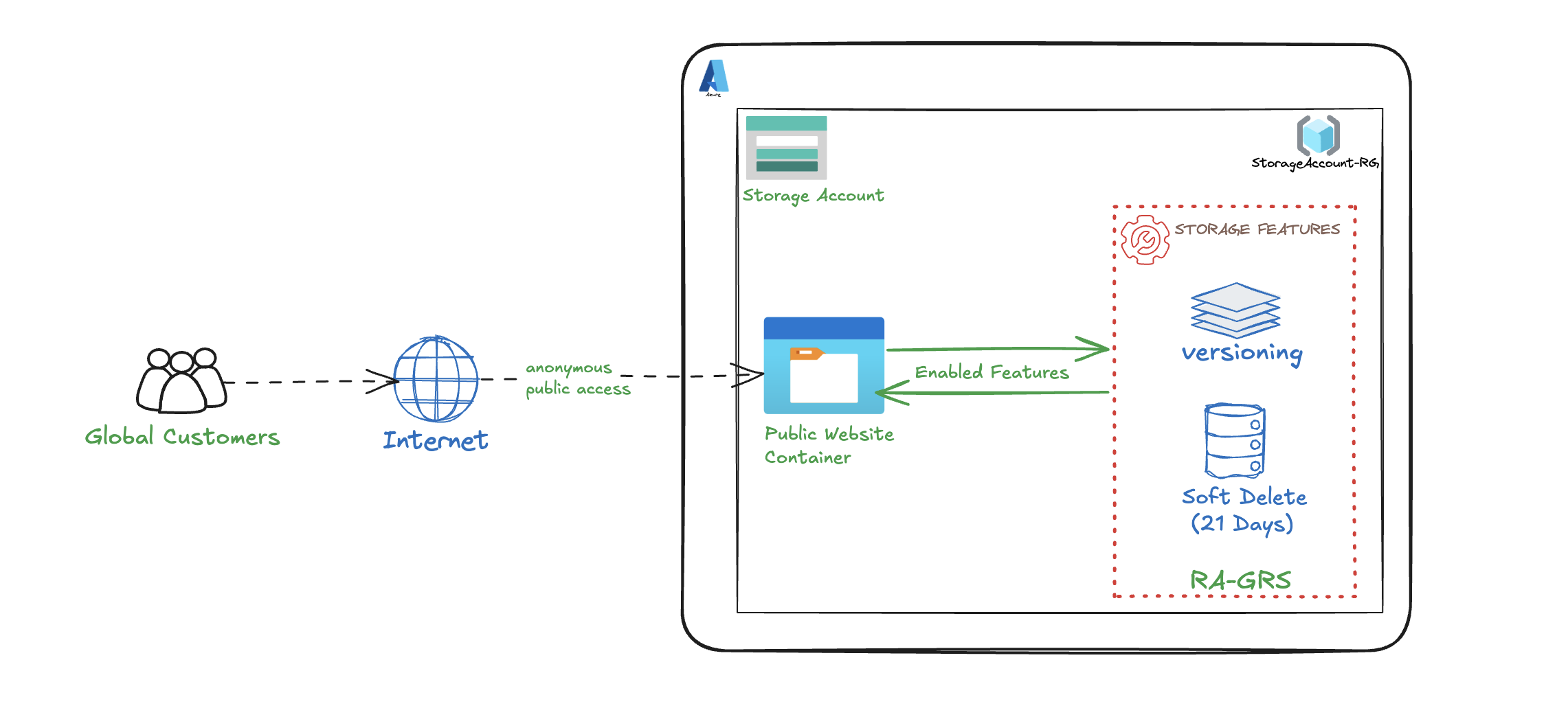
- Create a Storage account to support public website using default settings
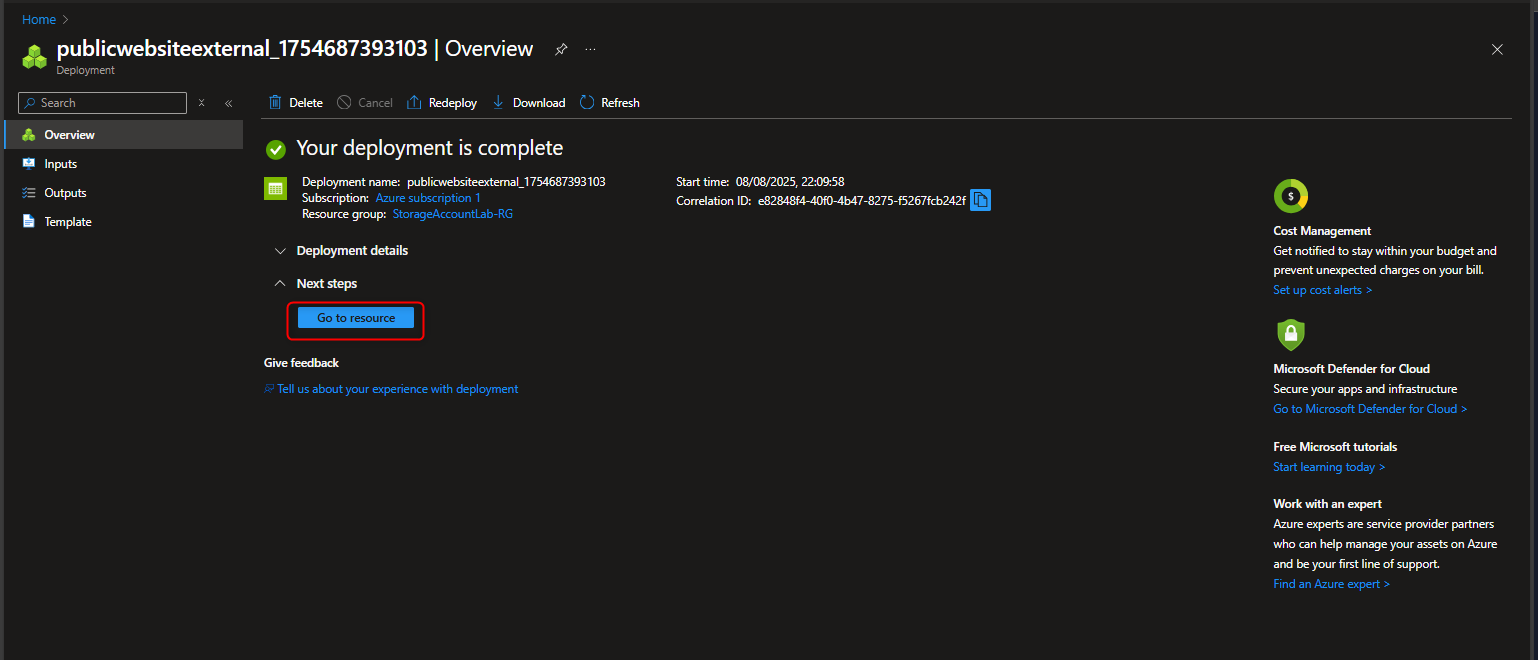
- Configure High Availability that allows Read access in a Secondary Region if there is Regional Failure
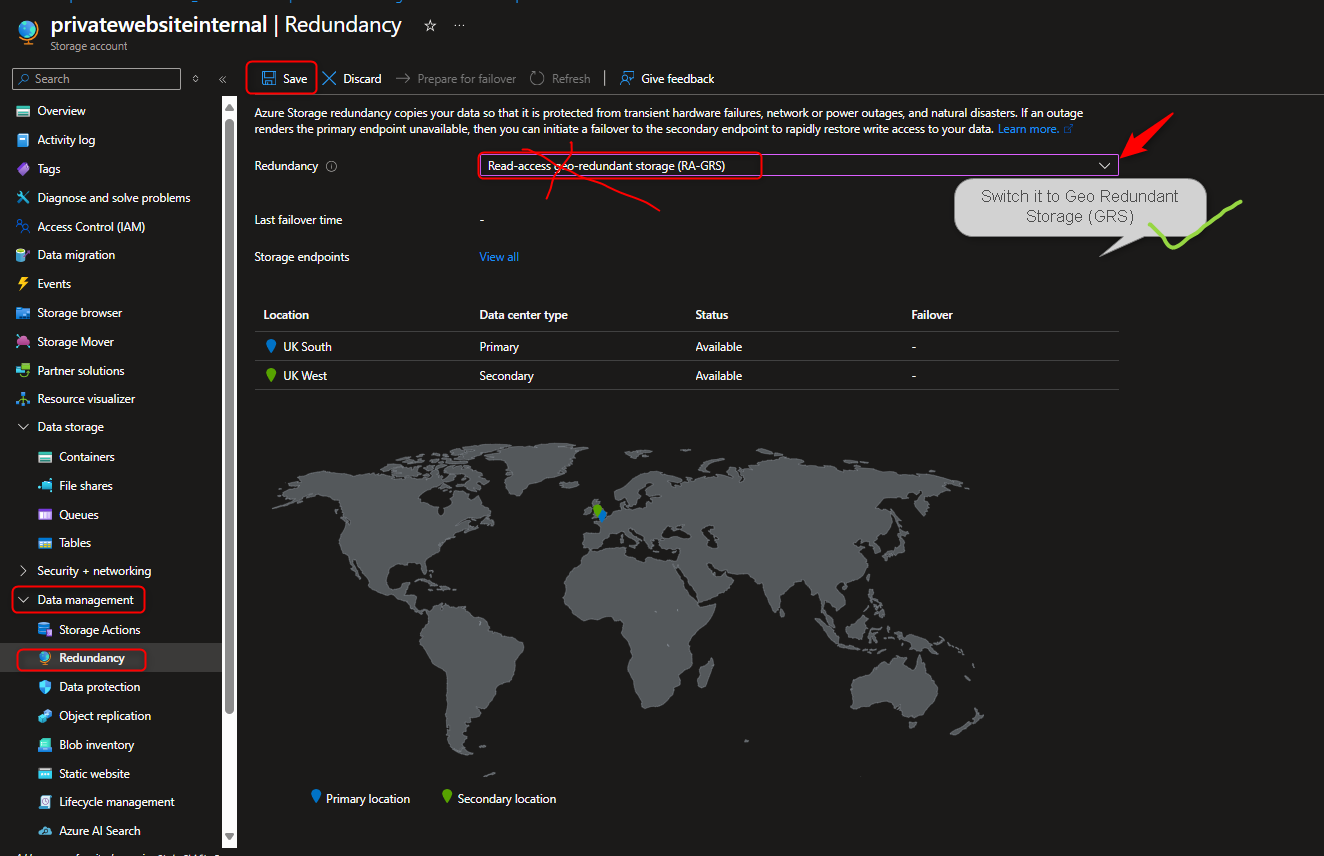
Navigate to the Data Management section -> Select Redundancy -> Select Read-access Geo Redundant storage -> Review the Primary & Secondary Location
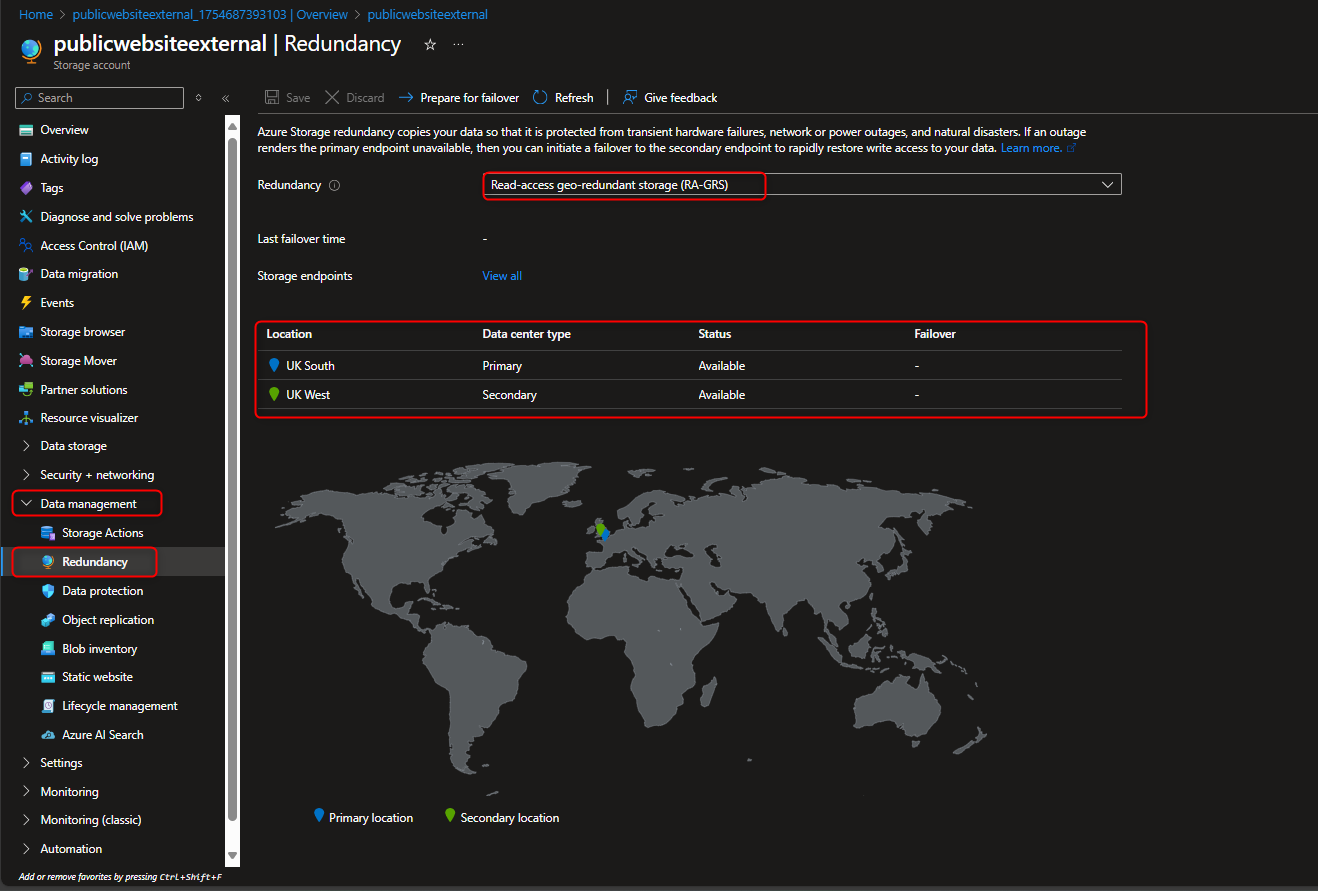
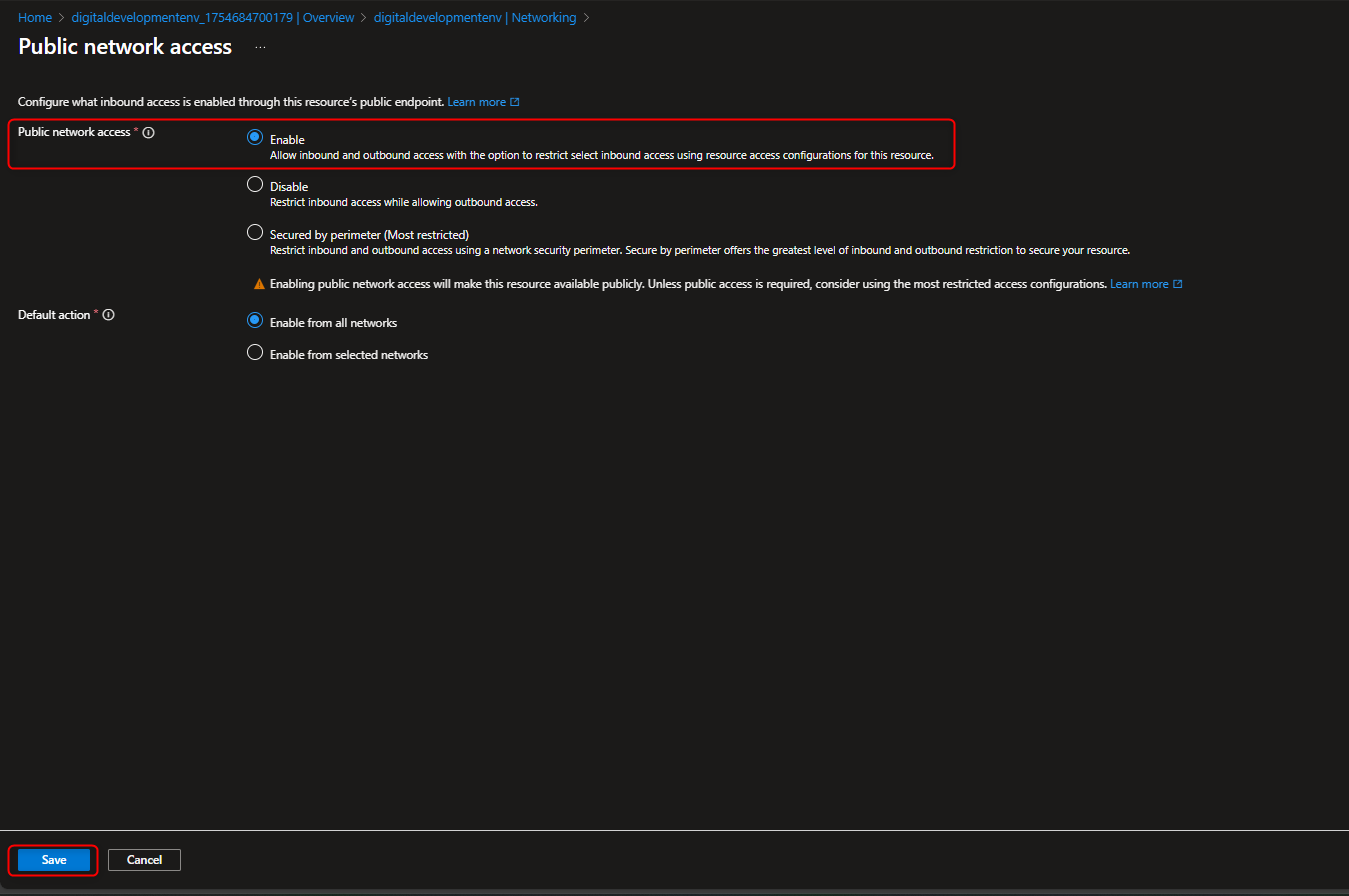
- Enable Accessibility to public website without customer login requirement
Settings -> Configuration -> Enable Allow Blob anonymous access -> Save
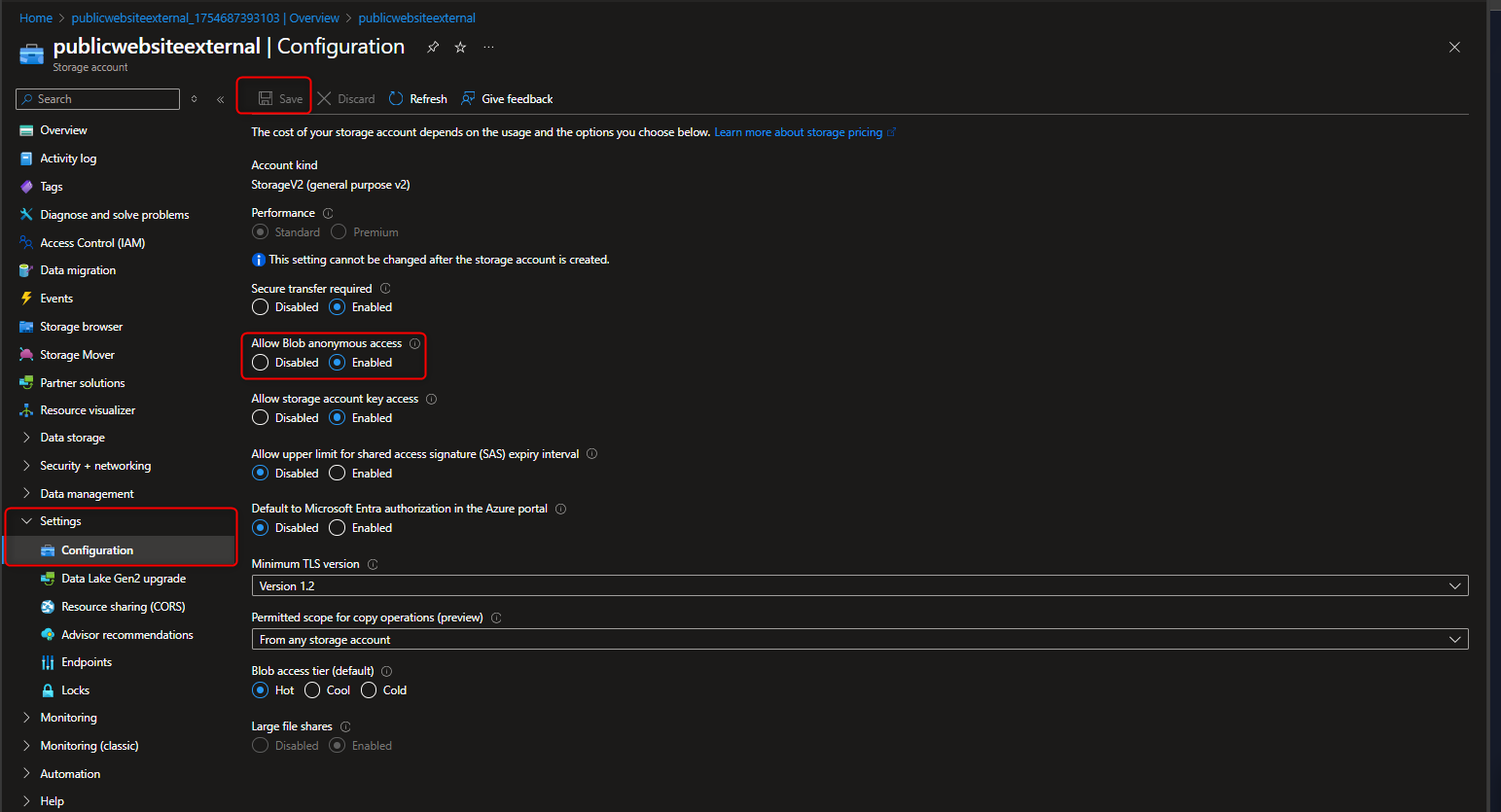
- Create Blob Container where images & product catalogues will be uploaded
Data Storage section -> Select Container -> Name publicwebsite -> Create
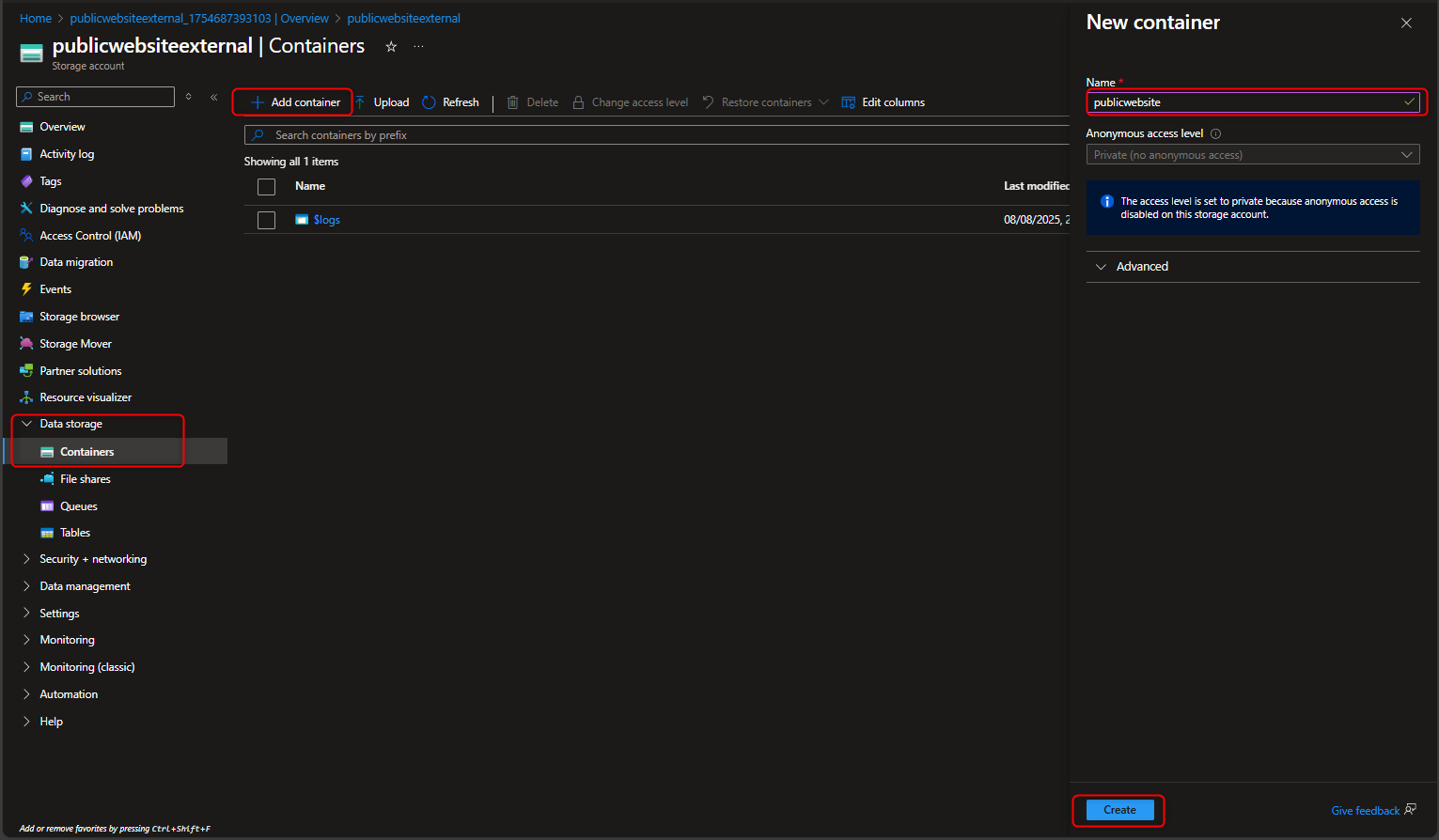
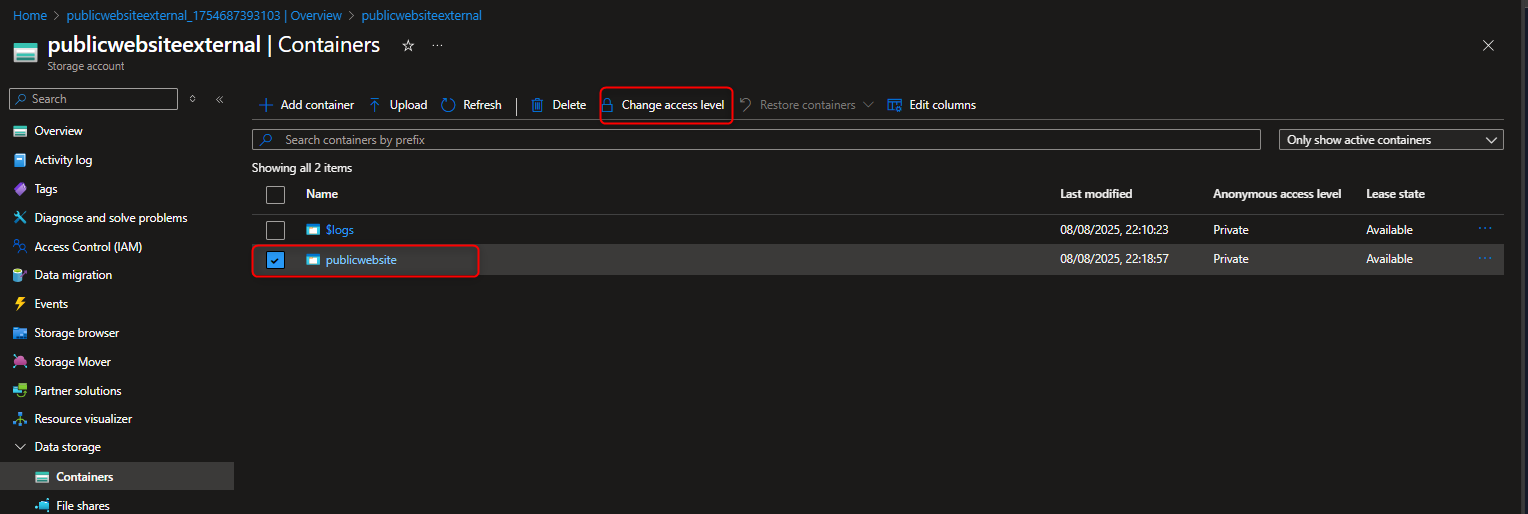
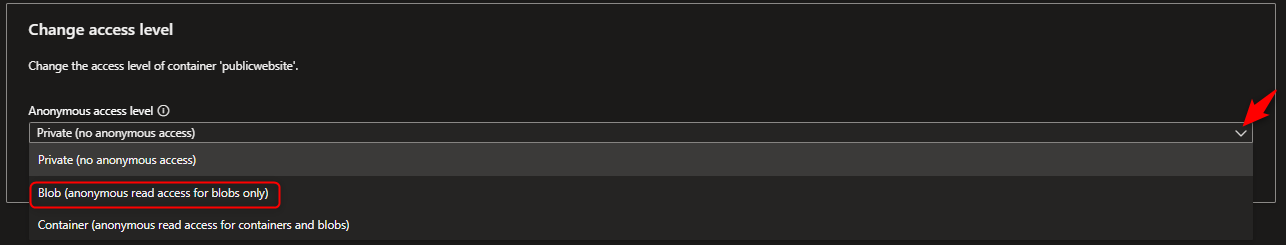
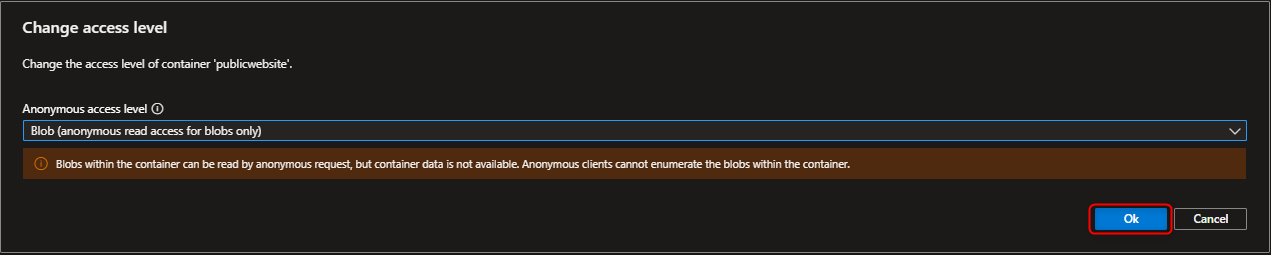
- Configure anonymous read access for the public container blobs that allows global customers to view contents without authentication.
Select the Public website container -> Change access level -> Select Anonymous read access for blobs only -> OK
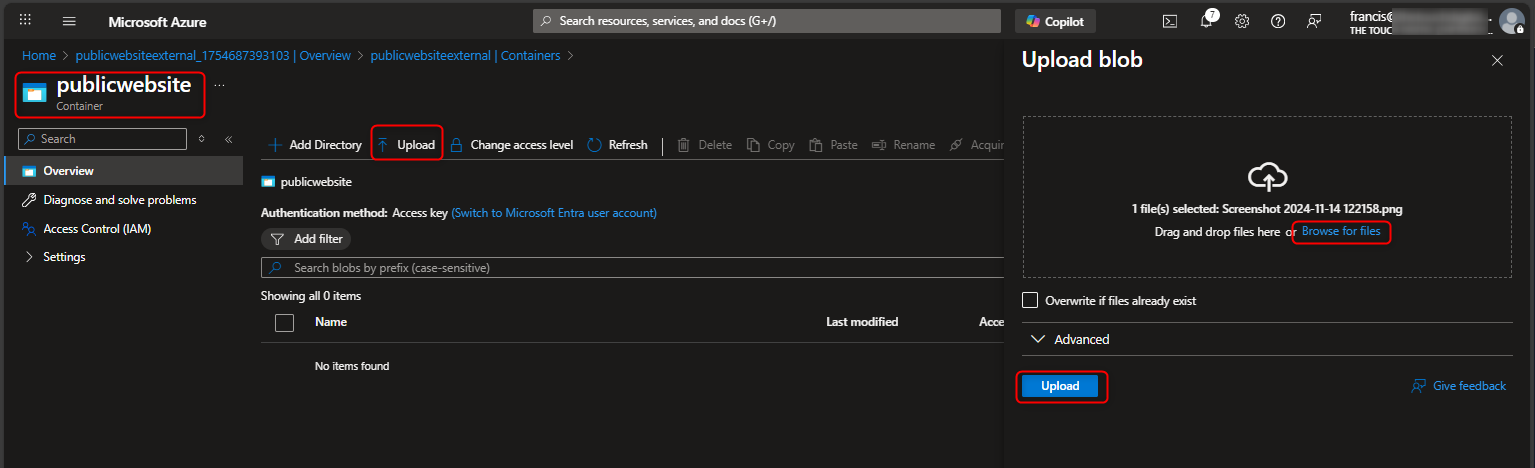
- Upload files to the public website container to test access
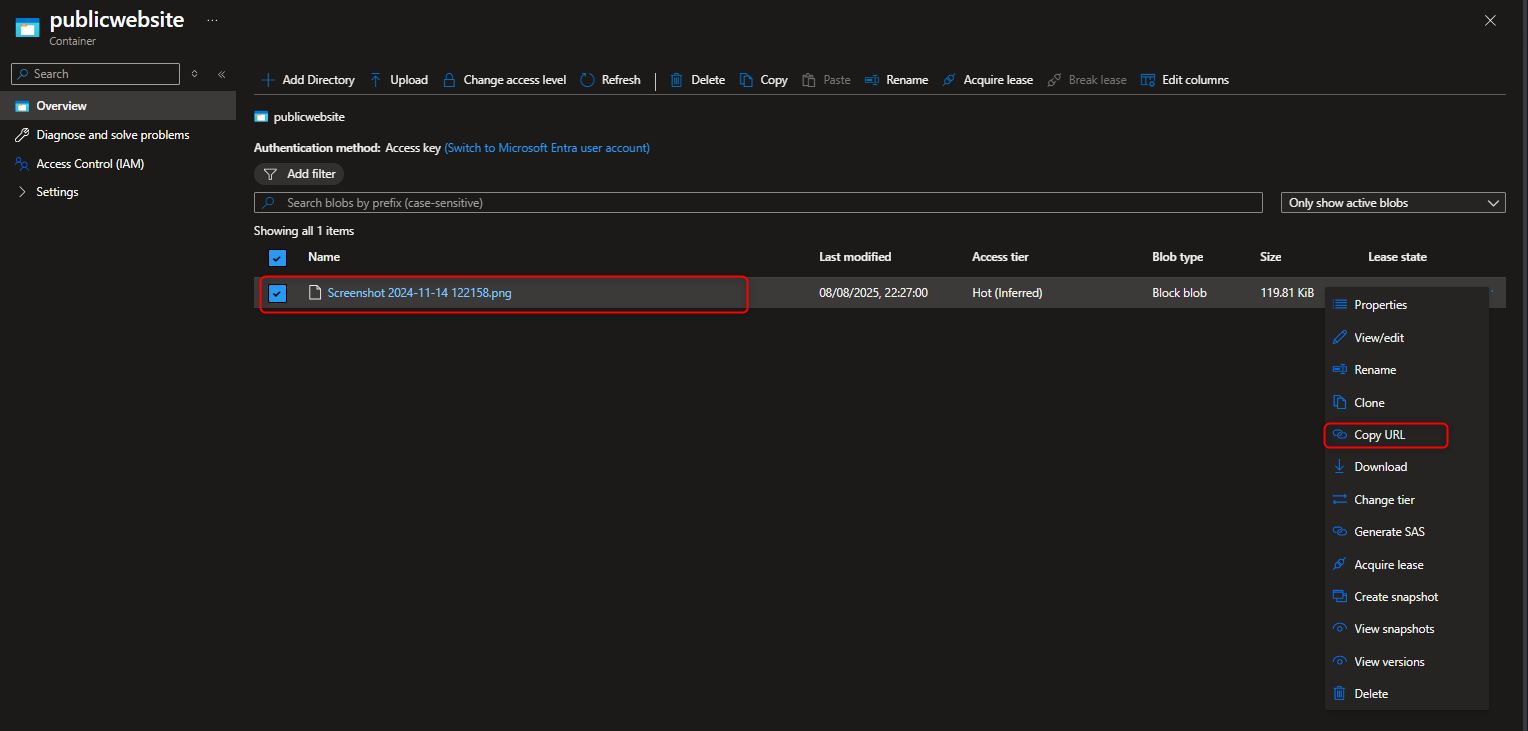
- Configure Soft Delete feature to protect website contents from accidental deletion
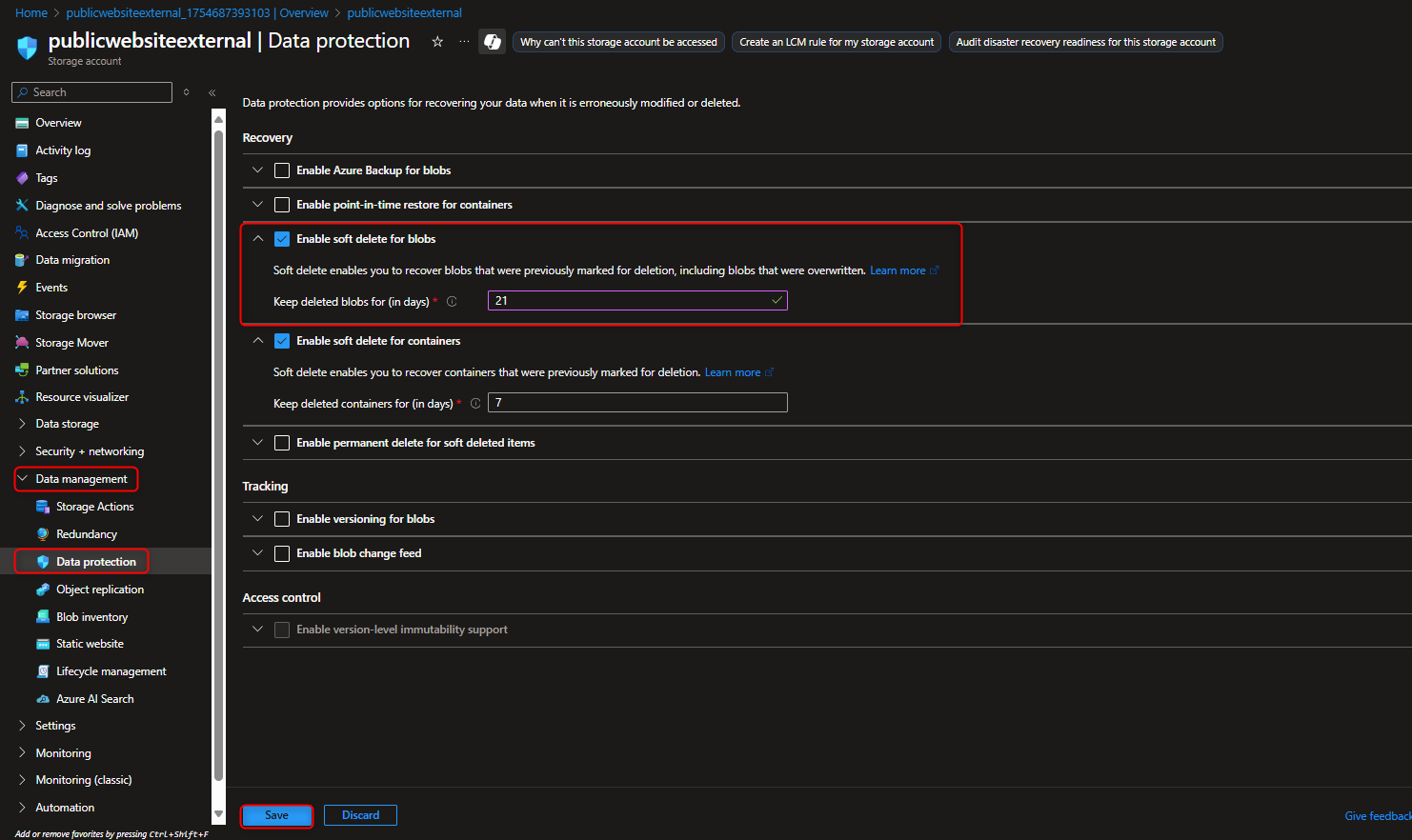
Navigate to Data Management -> Enable Soft Delete for blobs -> Set retention period for 21 days -> Save
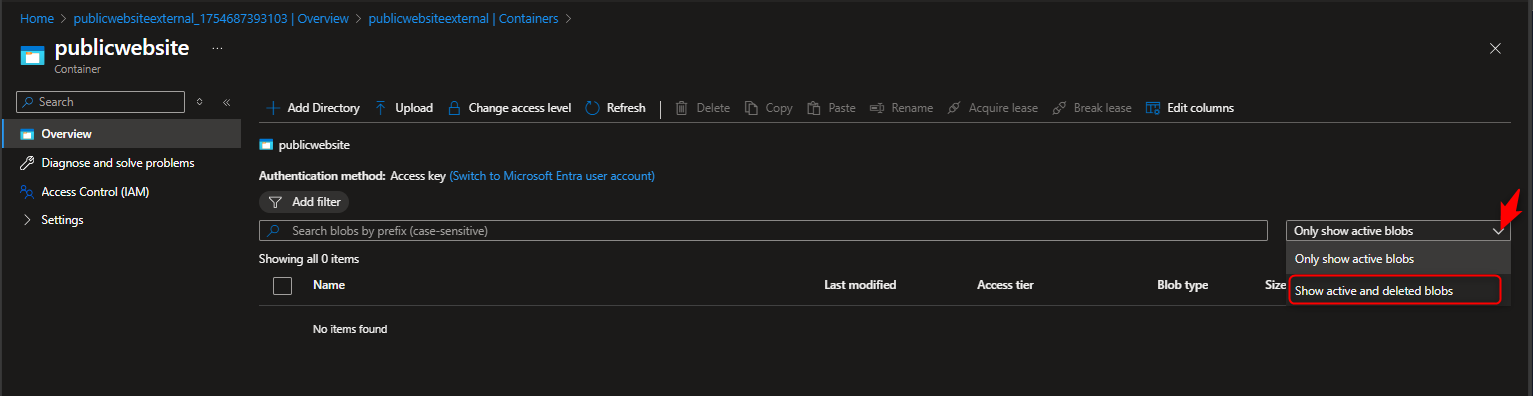
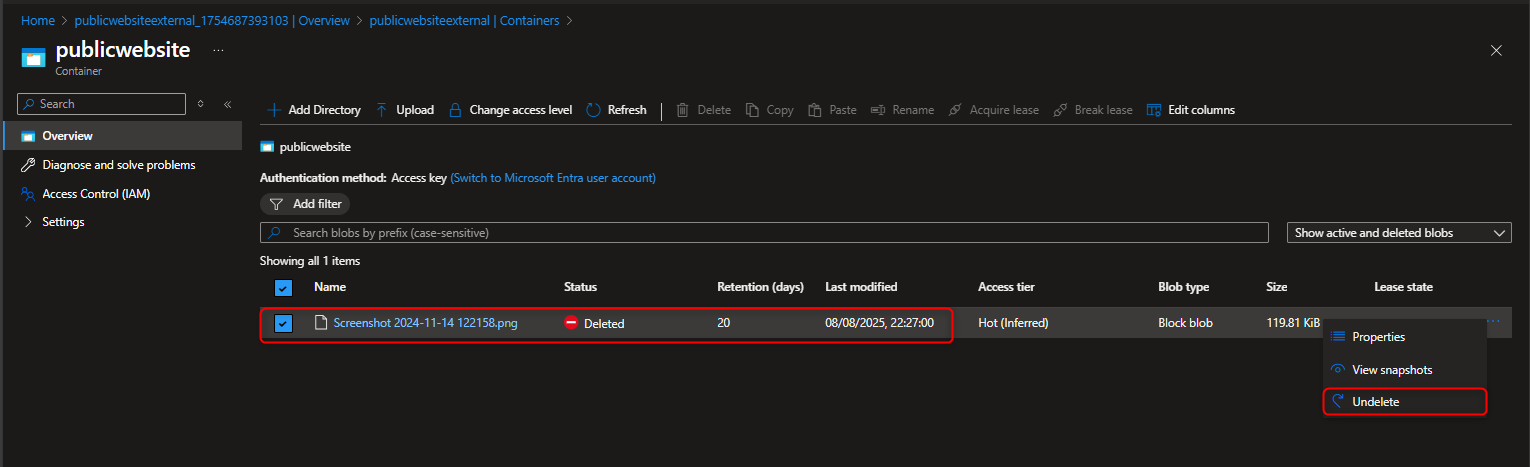
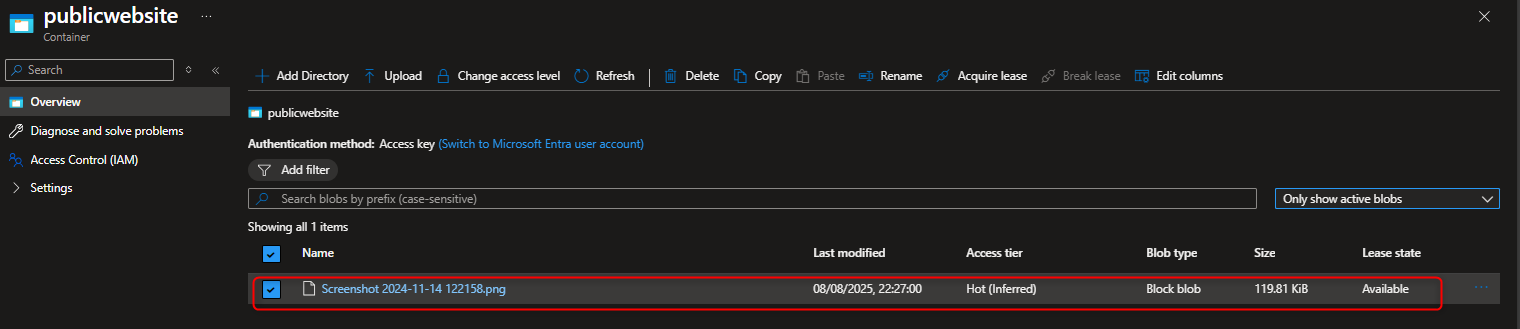
Delete Uploaded files -> Select show active and deleted blobs to display files that has been deleted from the container -> select Undelete to restore file -> Select Only show active blob once file has been undeleted/restored
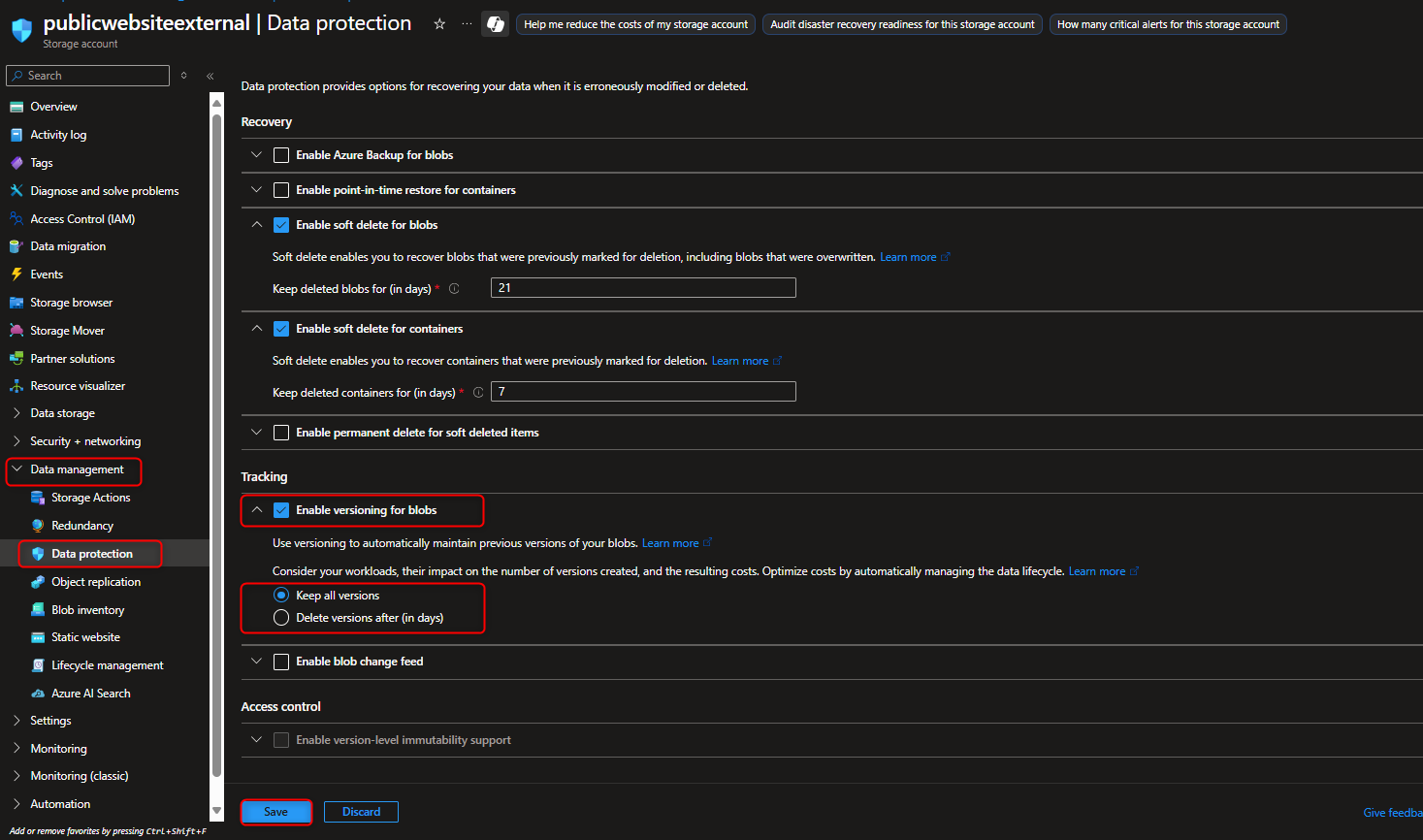
- Enable versioning to keep track of changes in product documents
Data Management -> Data Protection -> Select Enable versioning for blobs -> Keep all version -> Save
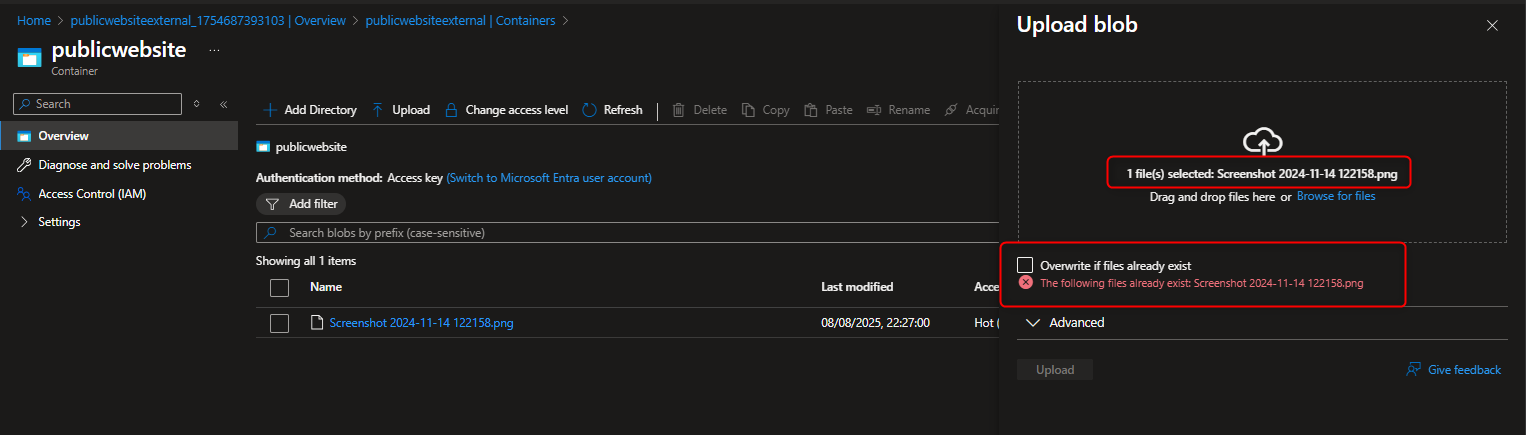
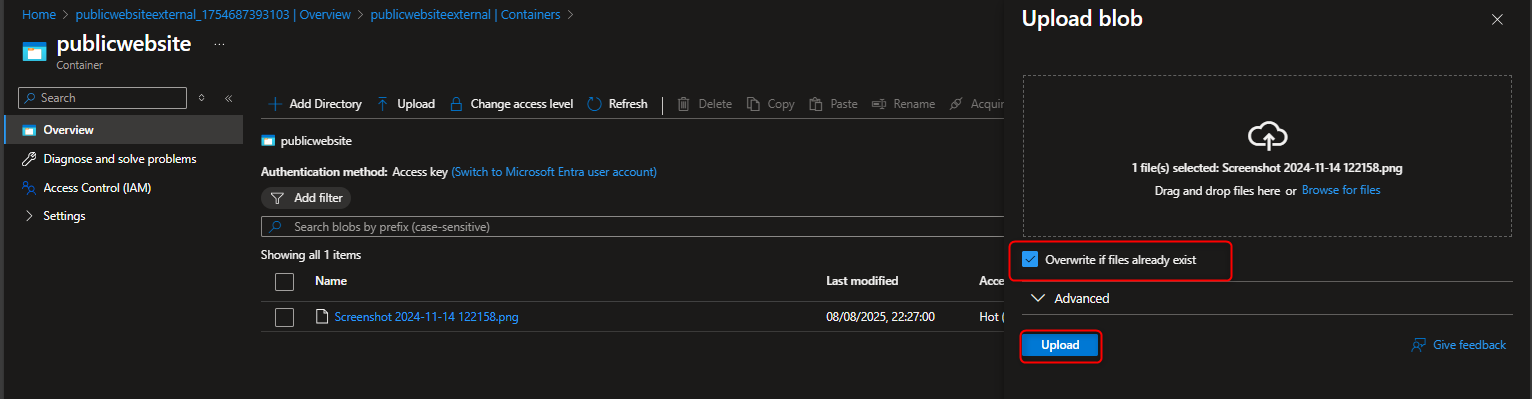
- To understand version control, upload a new version of a file with a small change. This will create a new version of the document, allowing you to easily revert to the original if needed
When you attempt to upload the same file after small changes has been made, You will notice the file already exist, select overwrite if file exists

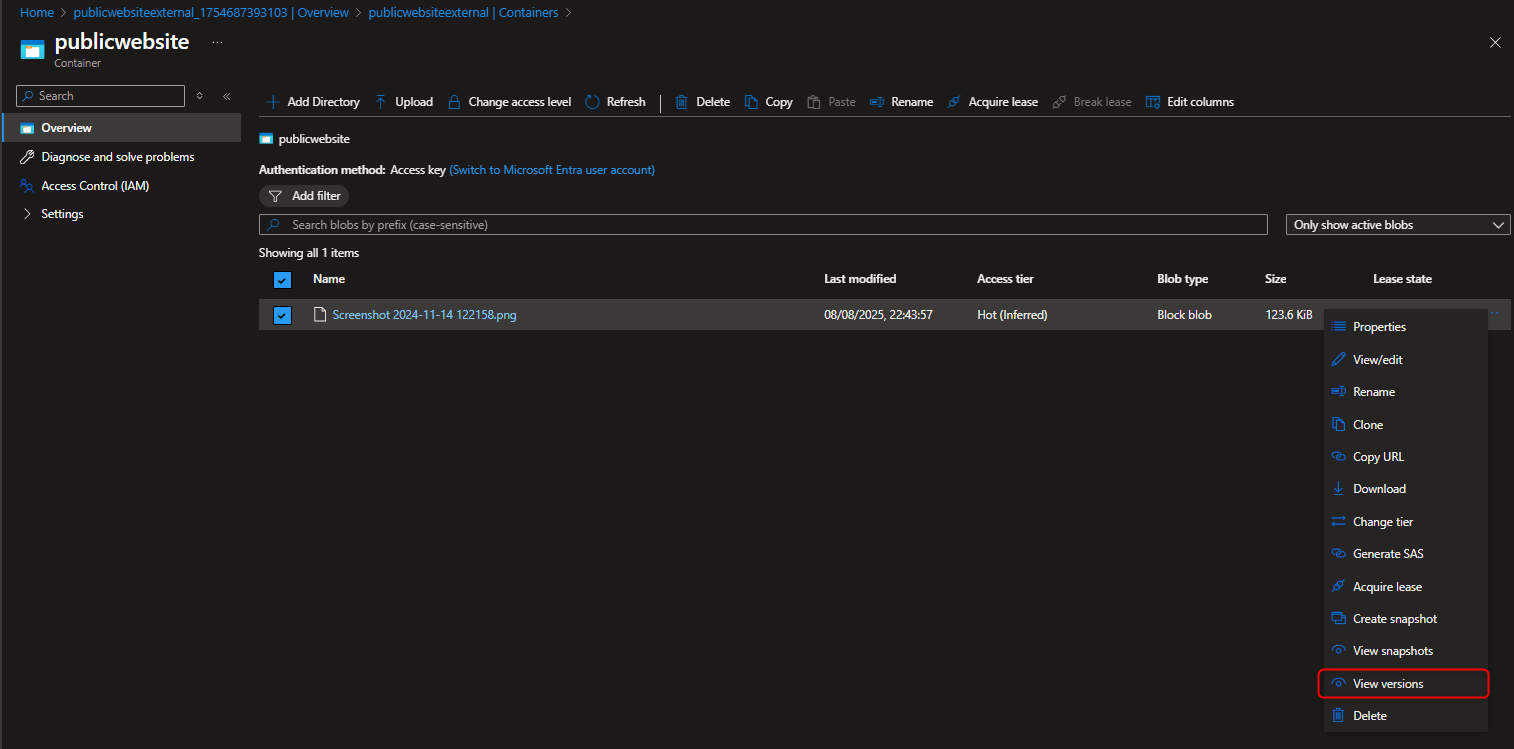
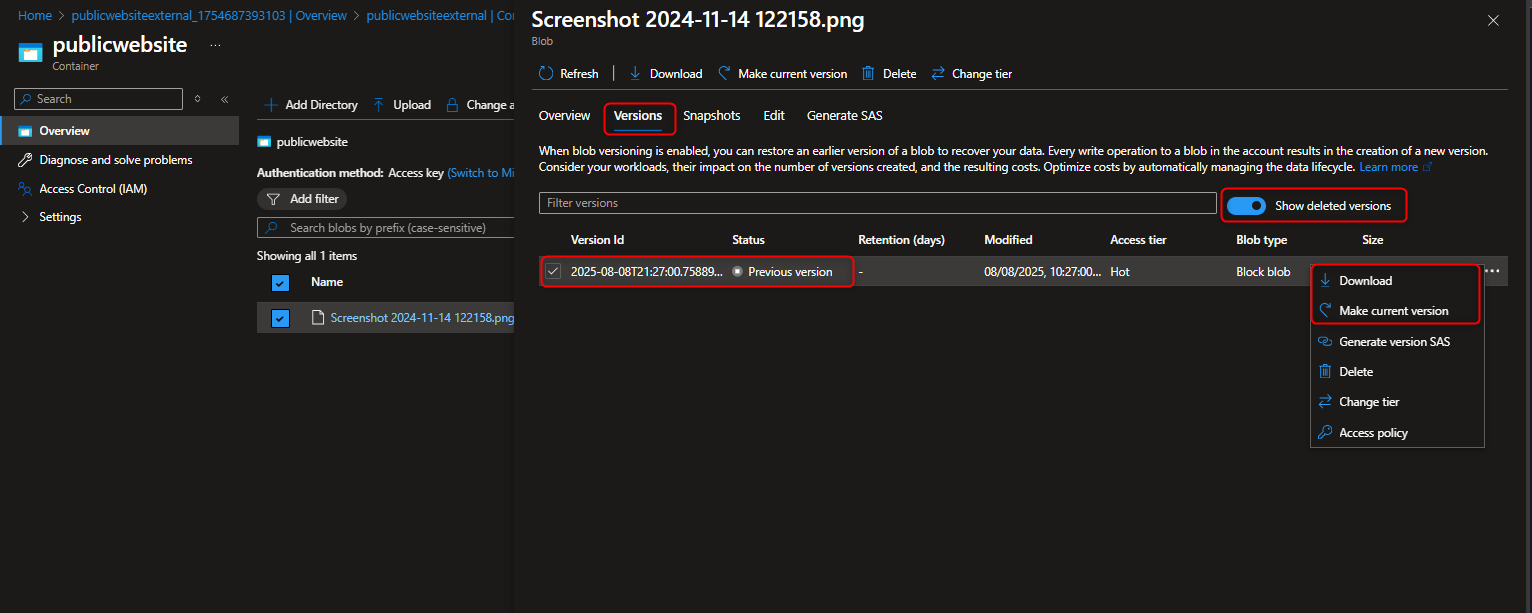
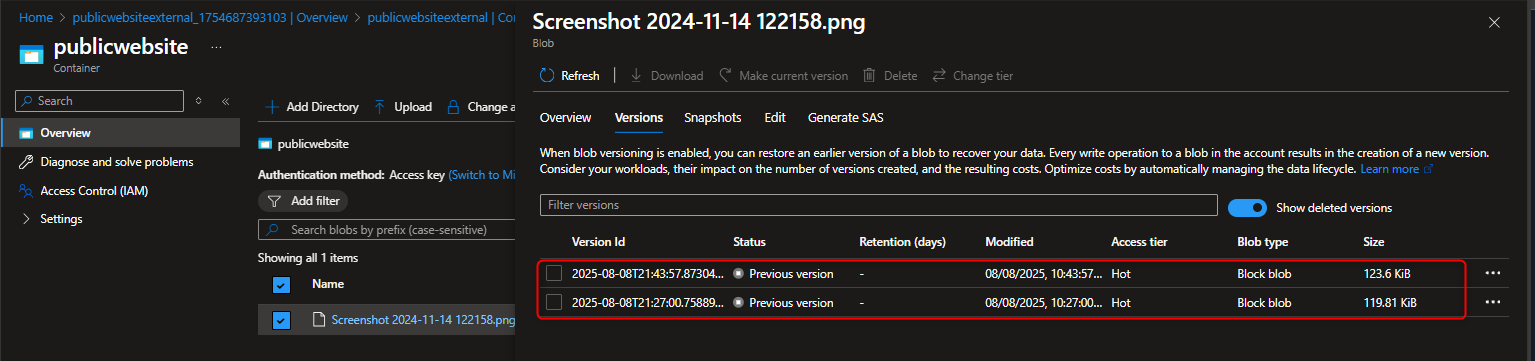
View versions -> Show deleted version
🔐 Private Internal Storage for Corporate Documents - Secure, Redundant, Cost Effective & Controlled Access
In this task, we’re provisioning a secure Azure Blob Storage solution for internal corporate documents, designed to meet enterprise-grade requirements for availability, privacy, and operational efficiency. The storage account is configured with Geo-Redundant Storage (GRS) to ensure high availability in the event of regional outages. Sensitive files are housed in a private container with no anonymous access, maintaining strict internal confidentiality. We’ll handle secure file uploads and generate SAS tokens to enable scoped, time-bound access for external partners. To optimize costs, lifecycle management will automatically transition blobs to the cool tier after 30 days. Finally, we’ll replicate objects from a public container into this private one, ensuring internal backup continuity and data resilience.
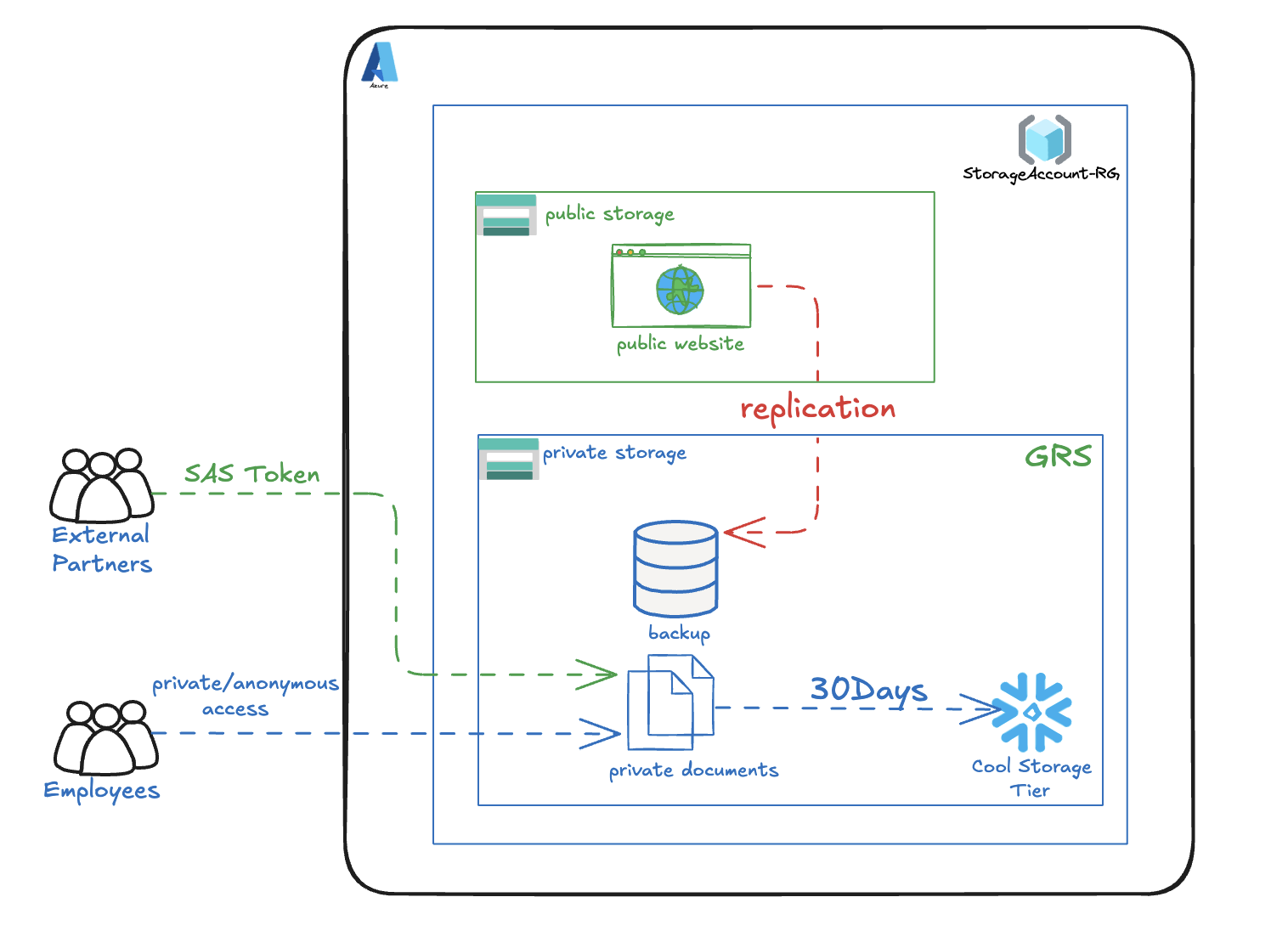
- Create a storage account for internal private corporate documents with High Availability (GRS)
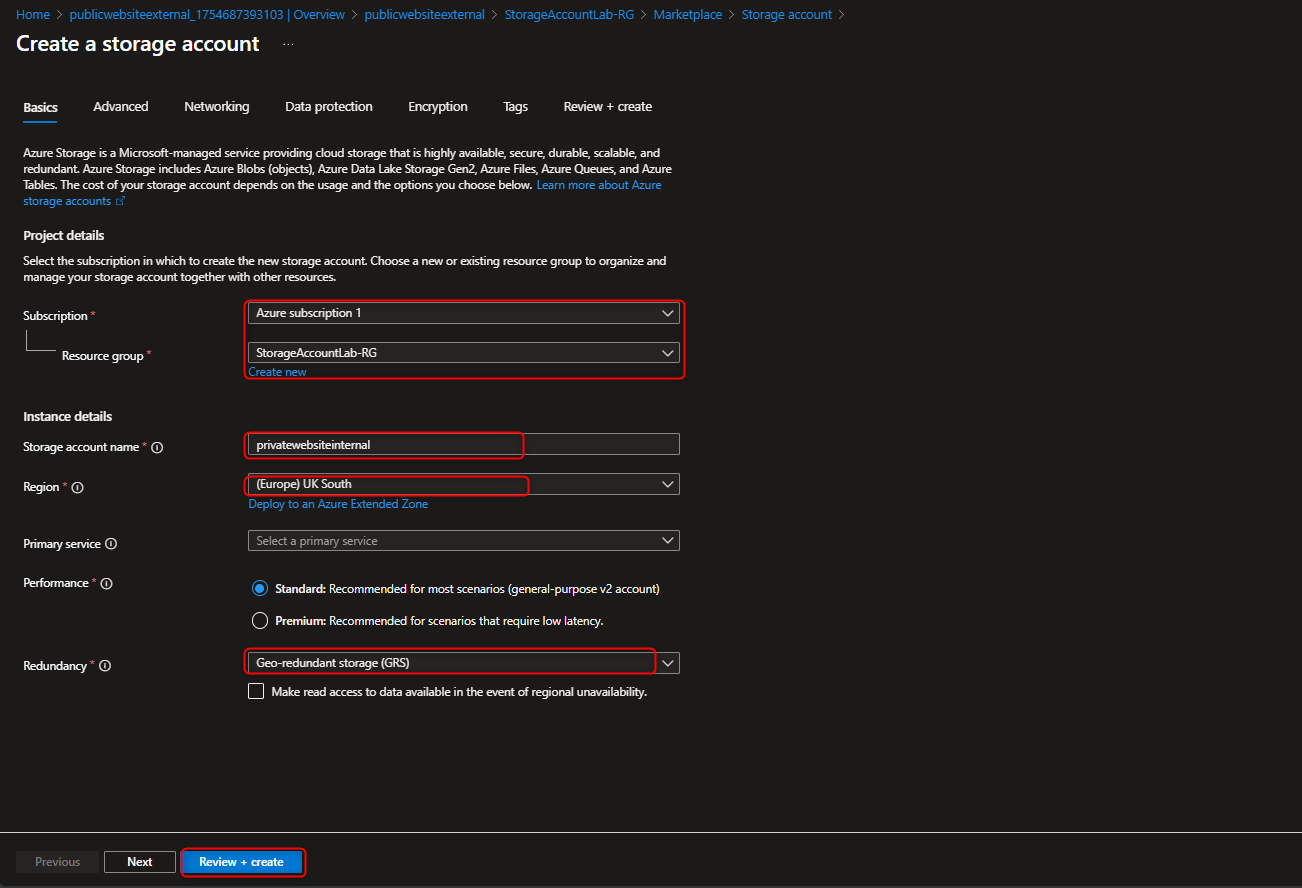
Ensure to check Data Management section that Redundancy is set to GRS as Read access is not required in the Secondary Region, Apologies for the error :)
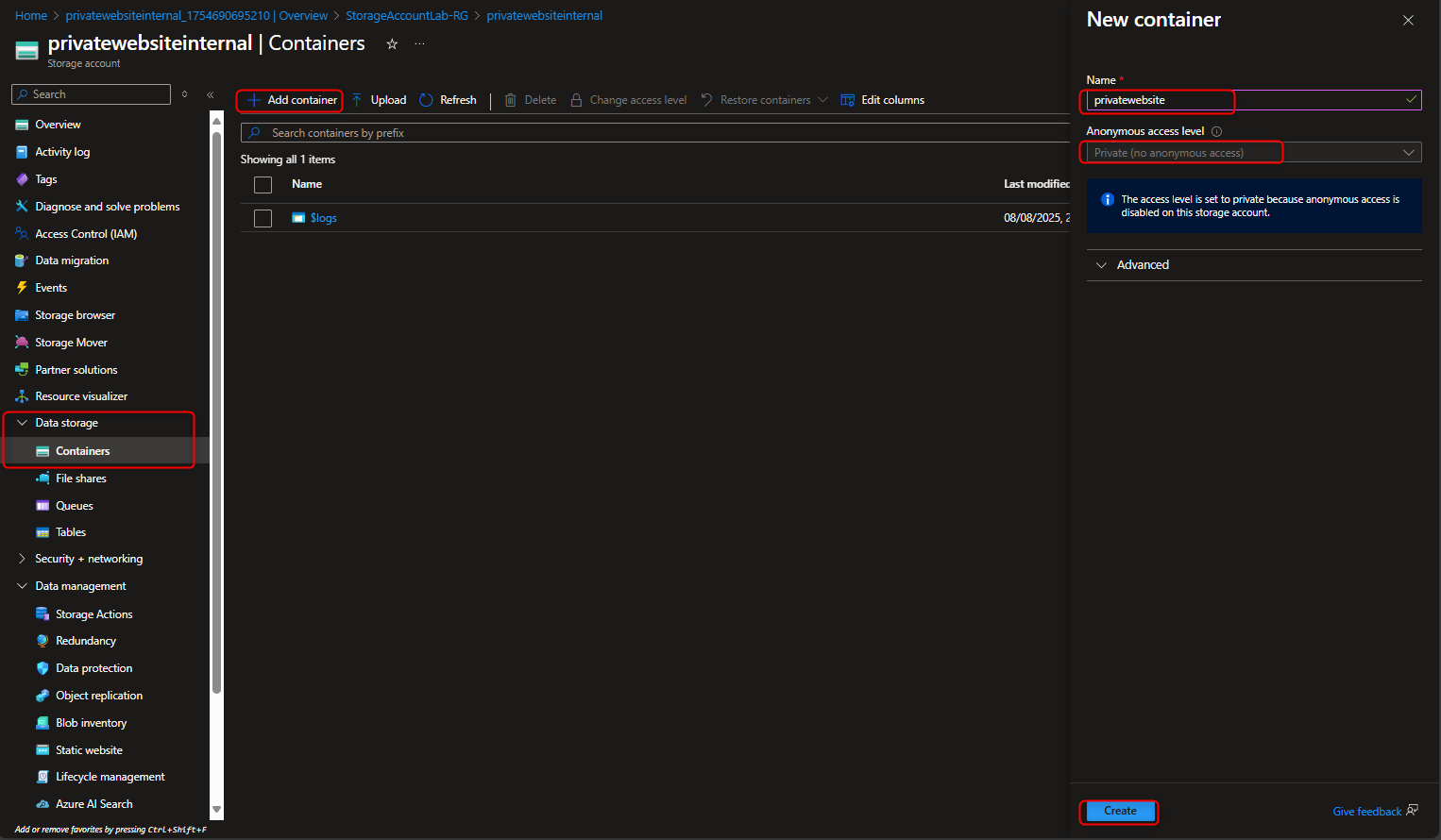
- Create private storage container to store corporate document
- Upload a file to the private container and test its not publicly accessible.
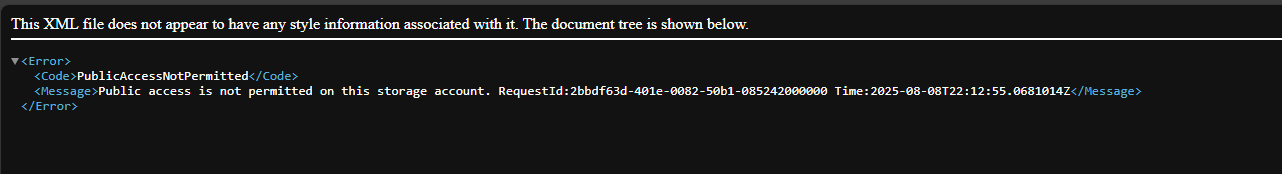
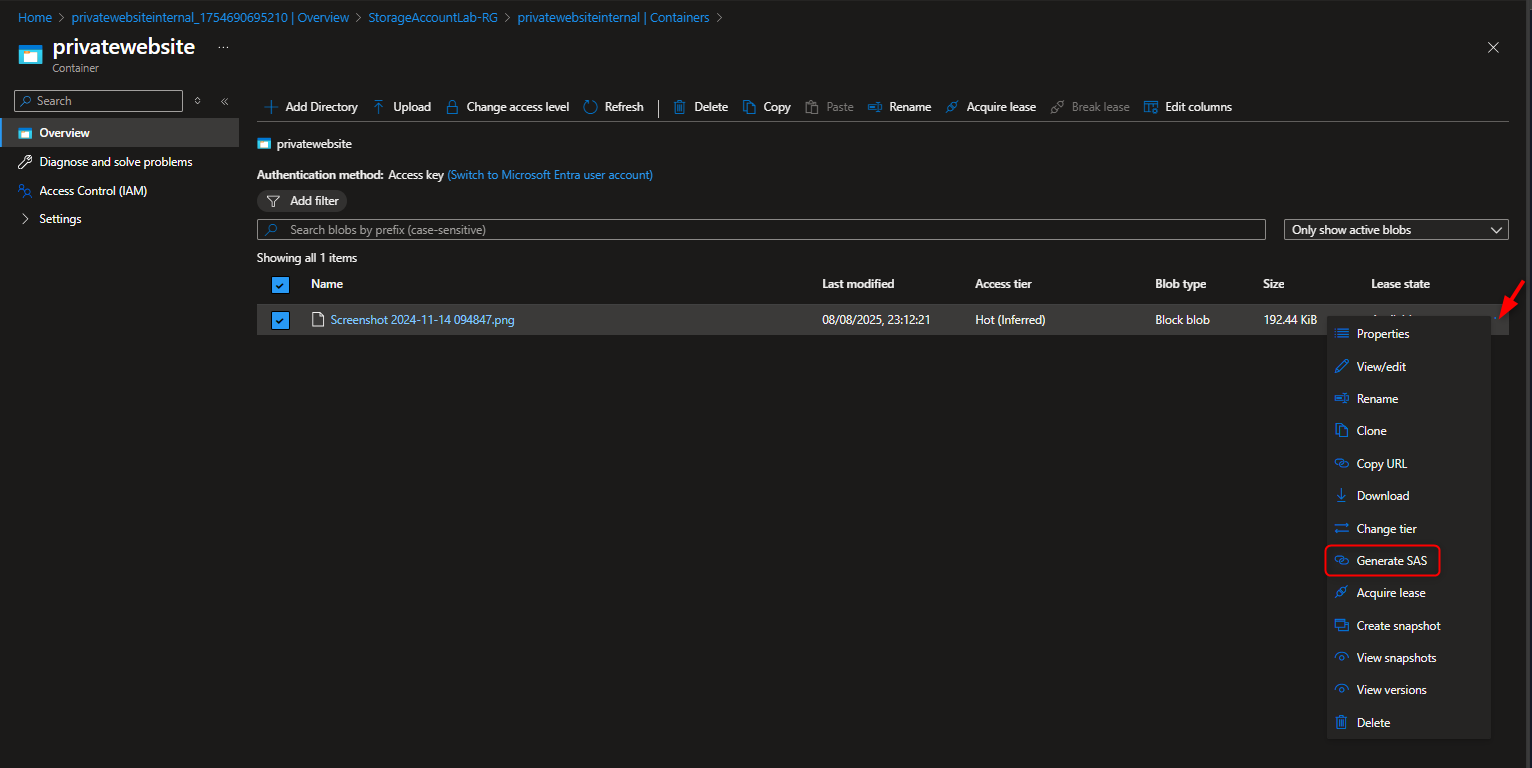
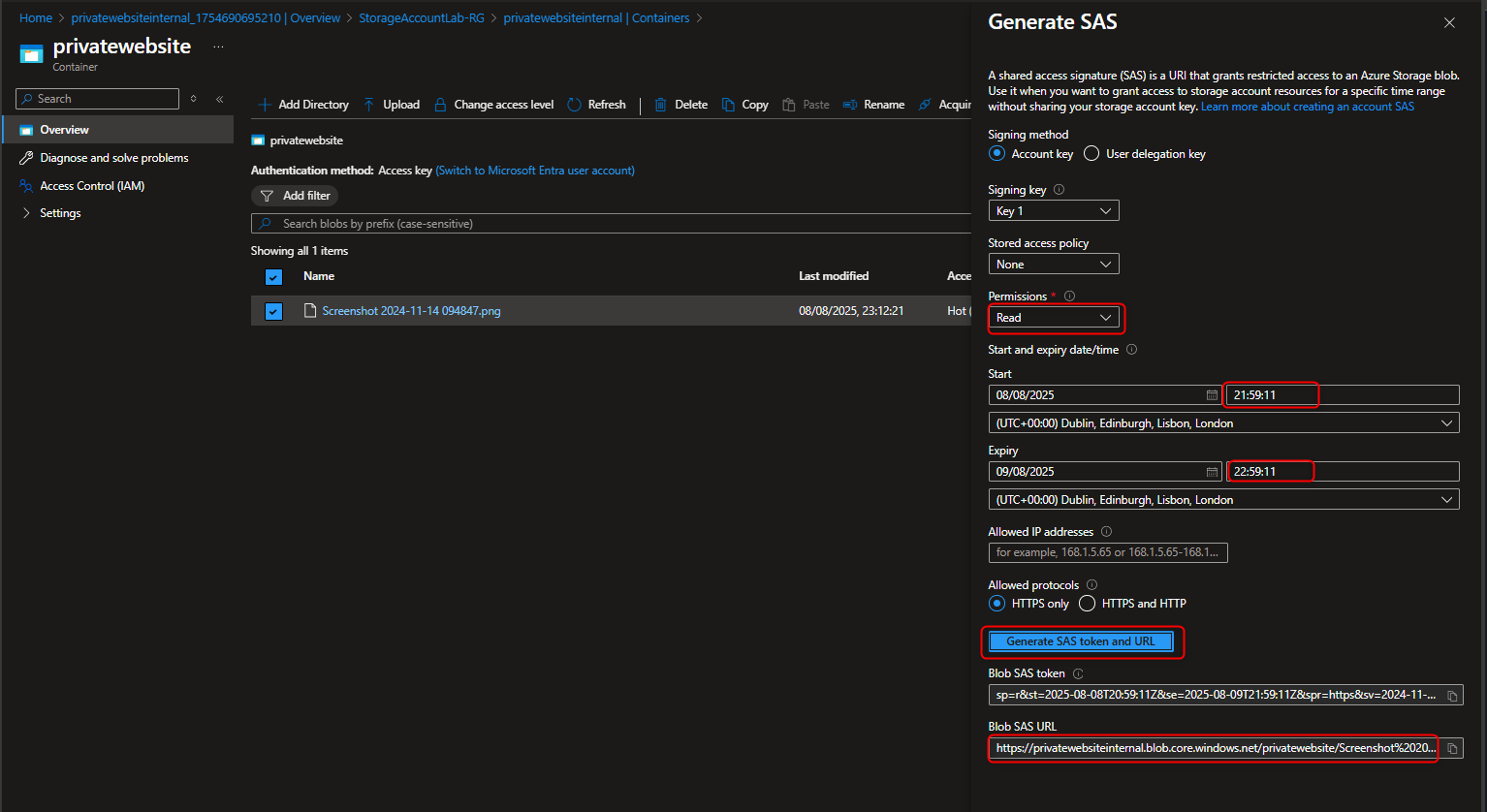
- Generate a Shared Access Signature (SAS) Token/URL that with will be used by Third Party partners for Read/Write permissions
Select uploaded file -> click on the 3 dots -> Select Generate SAS Set permission to Read -> Set Start and Expiry to 24hrs -> Https -> Generate Token and URL -> Copy URL to browser to view file
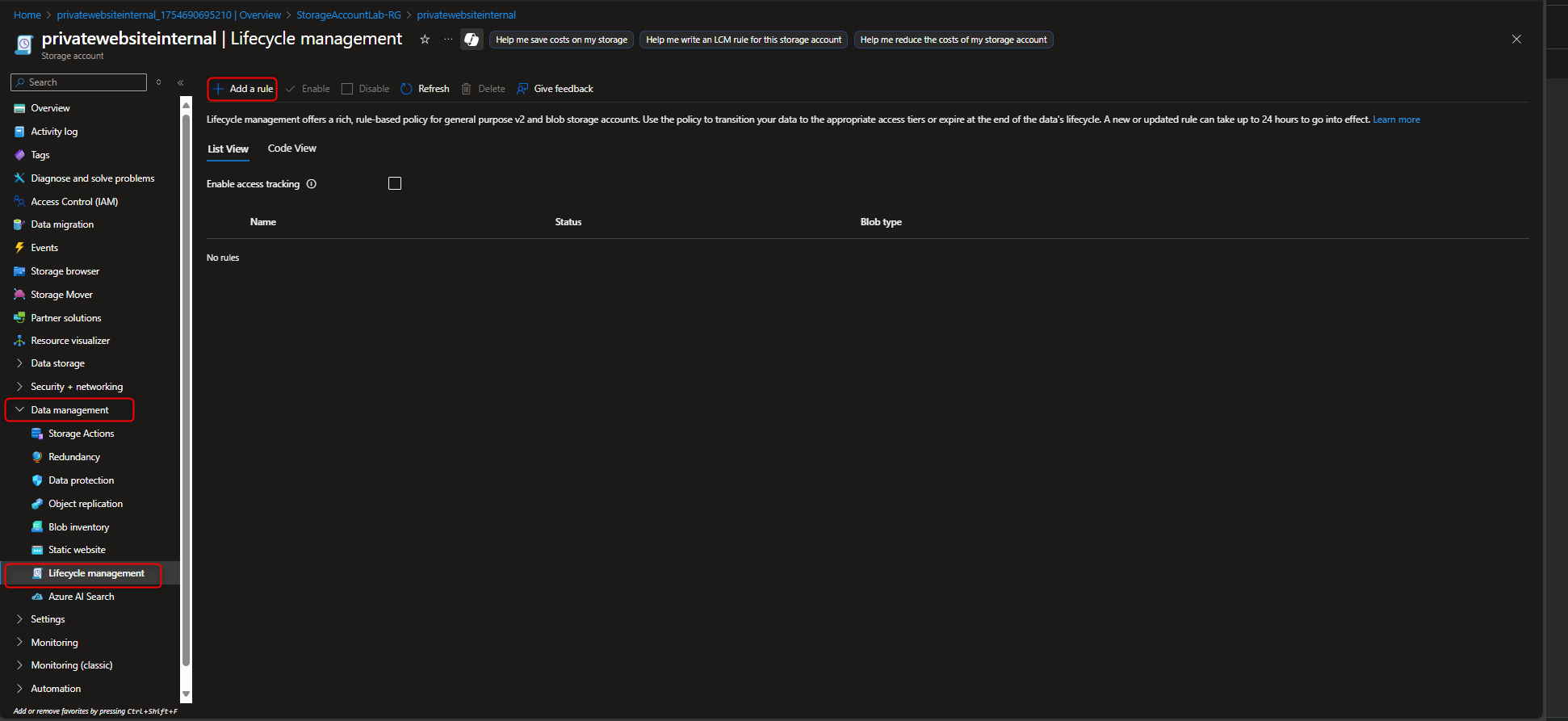
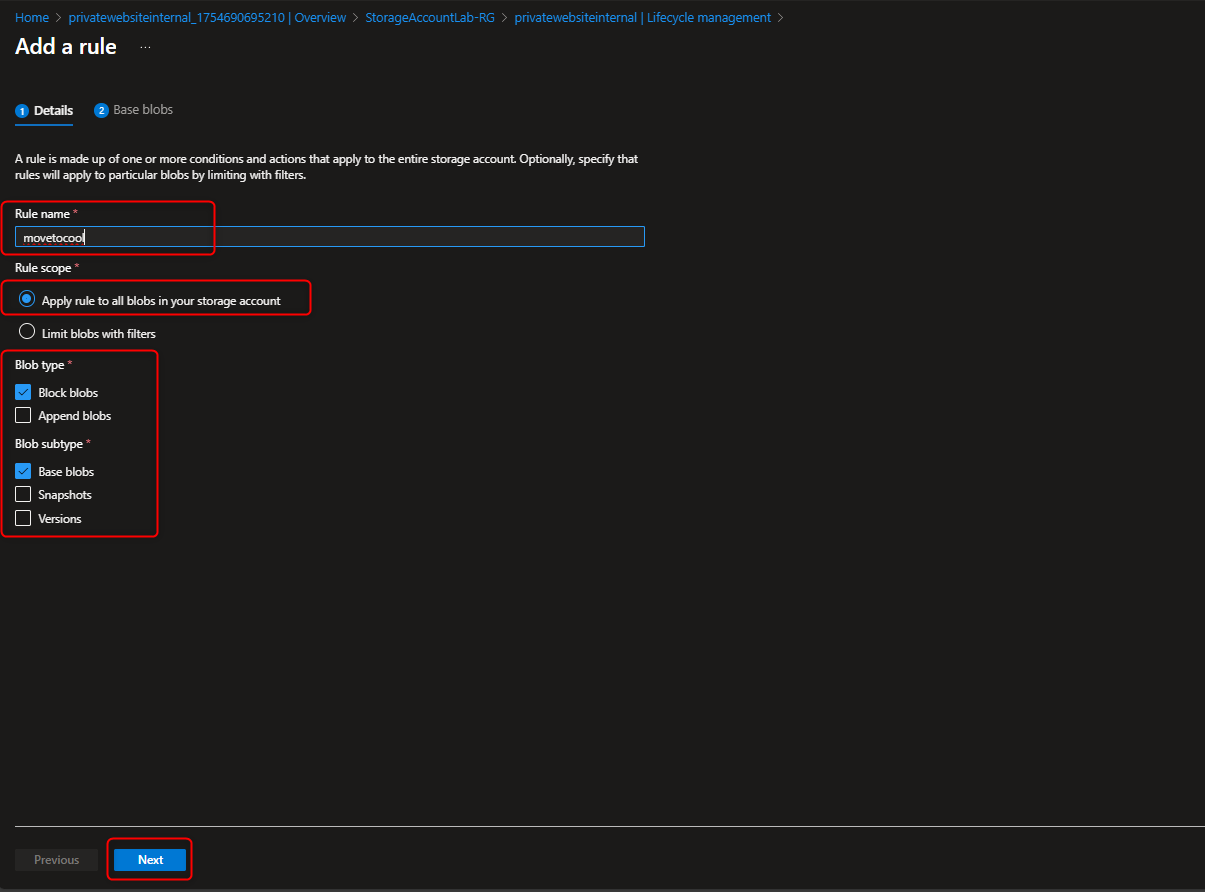
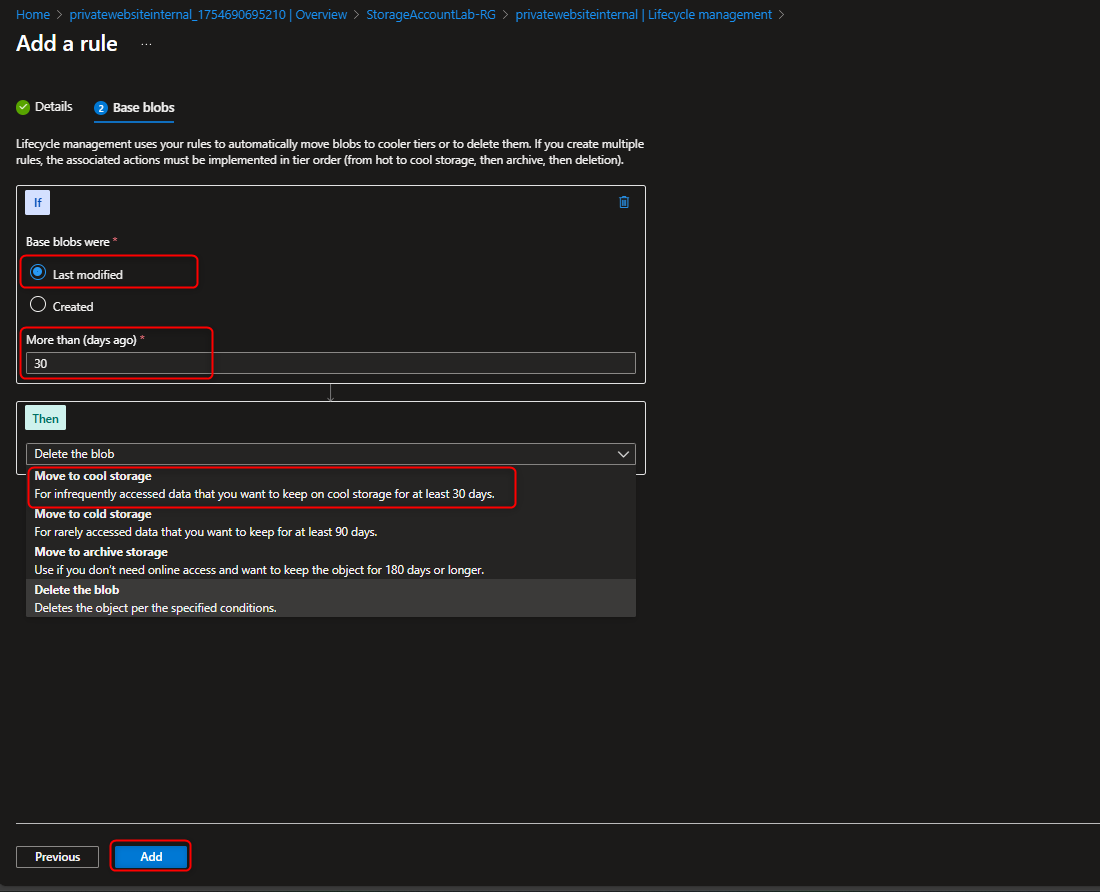
- Configure a Lifecycle rule in Data Management section that move blobs from Hot to Cool Tier
Data Management -> Lifecycle management -> Add rule
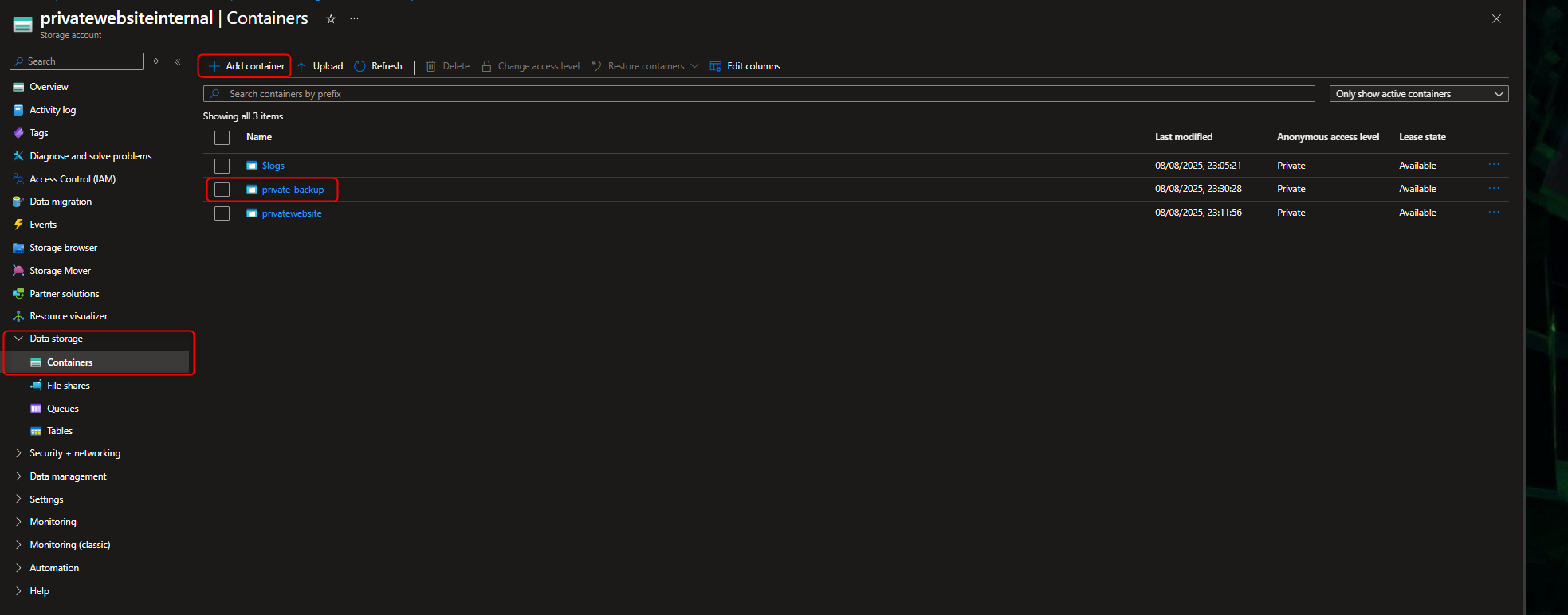
- Set up Backup container in the private storage account for object replication from the public website to the private back up container.
Data Storage -> Add Container -> enter parameters for backup and default setting -> Create
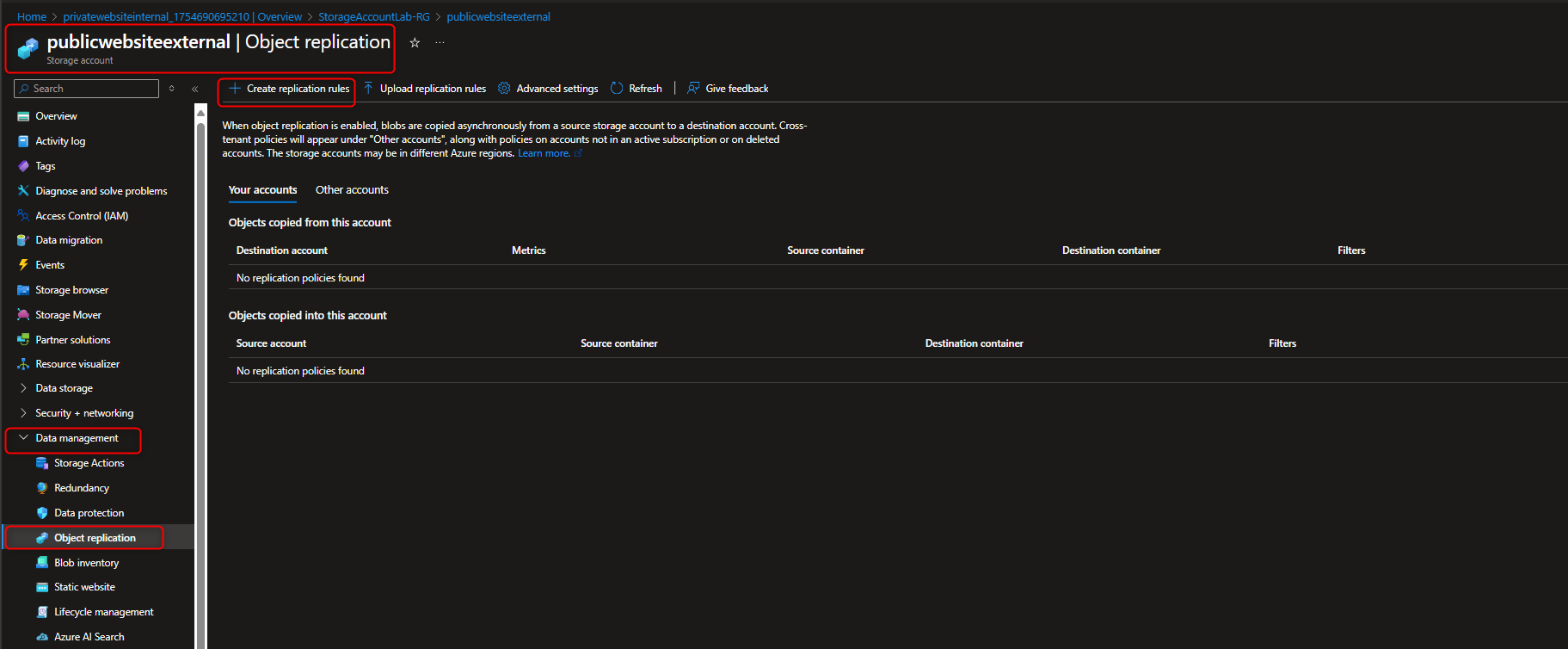
- Navigate back to the public website storage account to set up replication rule
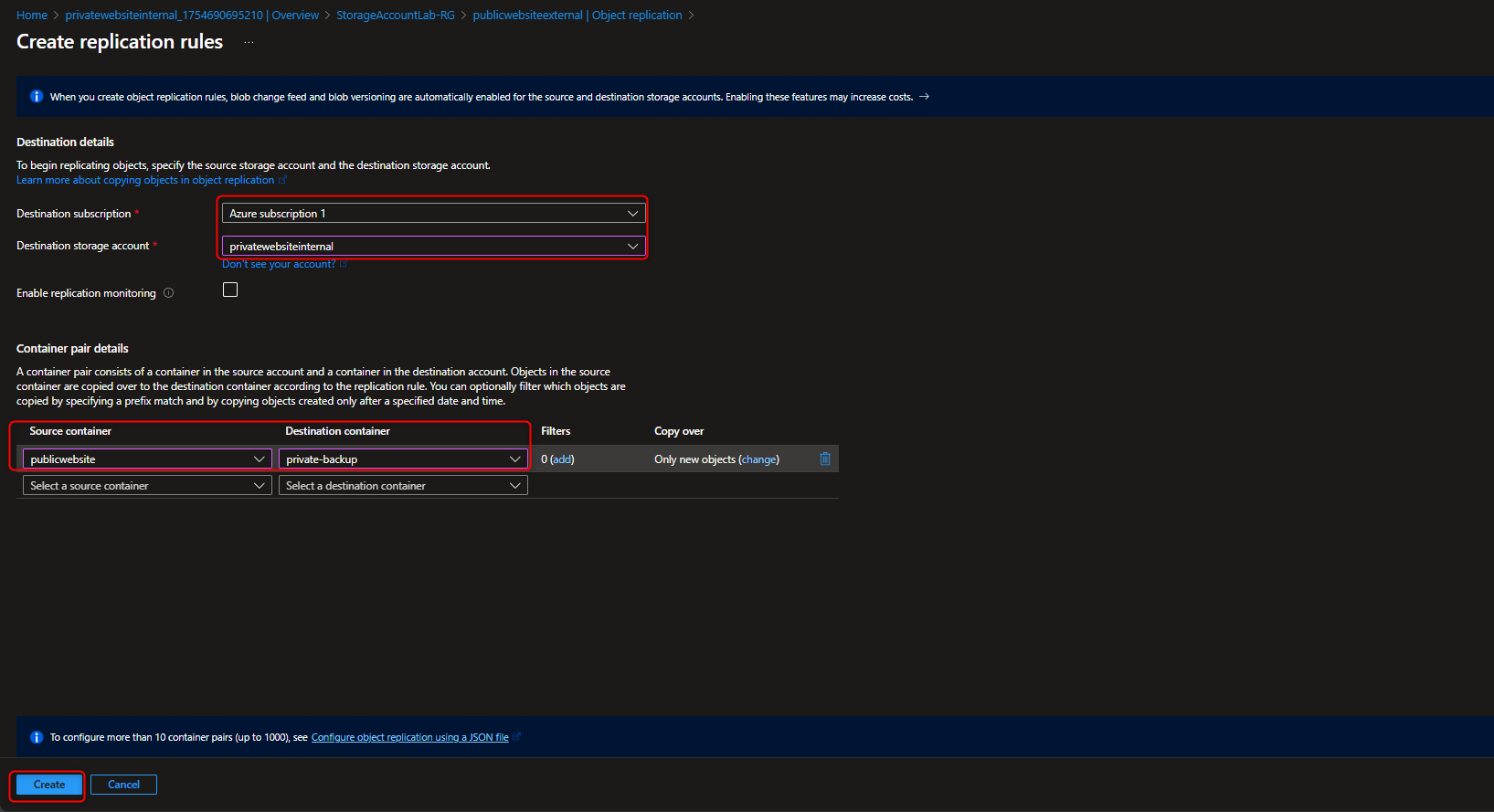
- Add Replication rule with Destination Storage Account(Private) Source container (public) to Destination container (private)
- Review replication rule
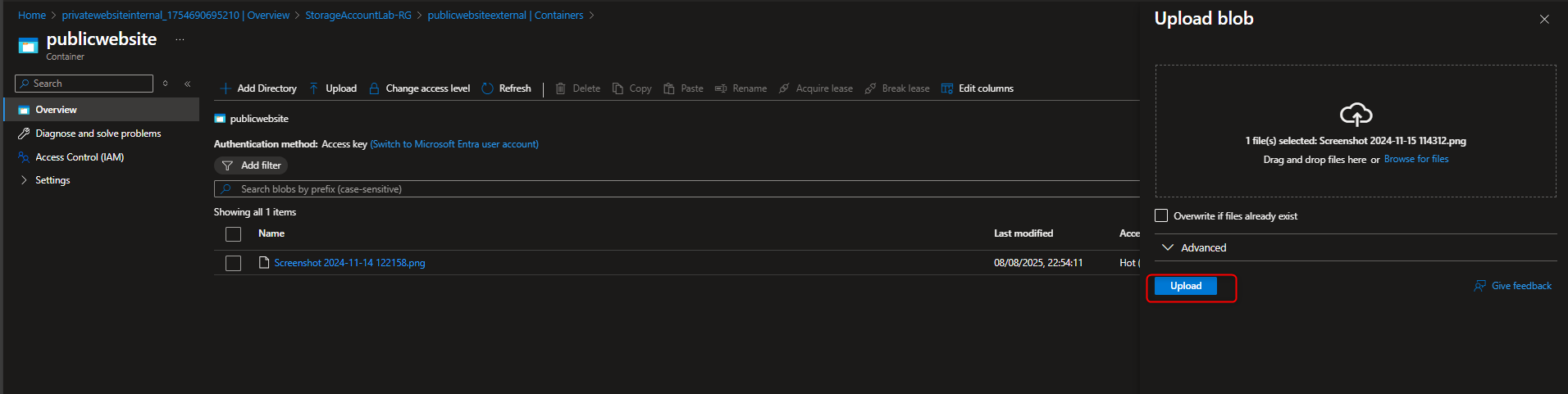
- Upload a file into the public container
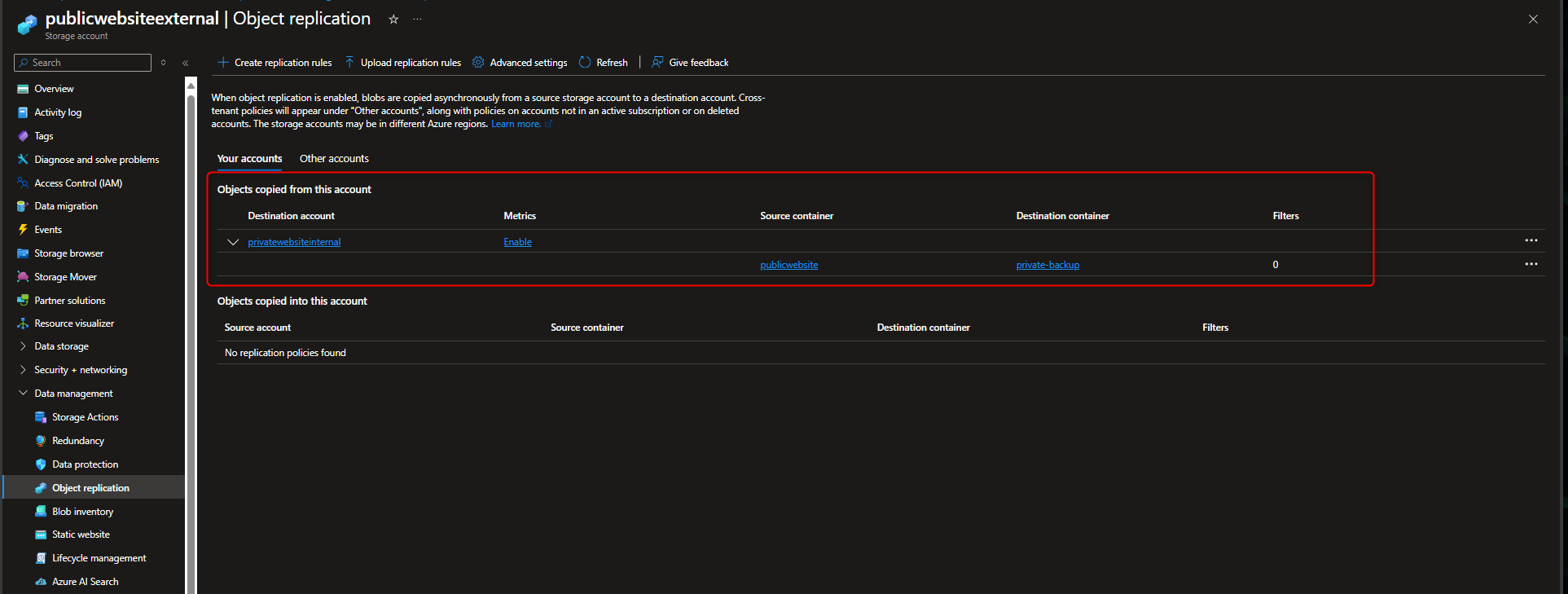
- Check the private container to check object was replicated, This can take up to 2-5mins, so you might need to refresh a couple of times.
🗂️ Secure Shared File Storage for Finance Department Using Azure Files
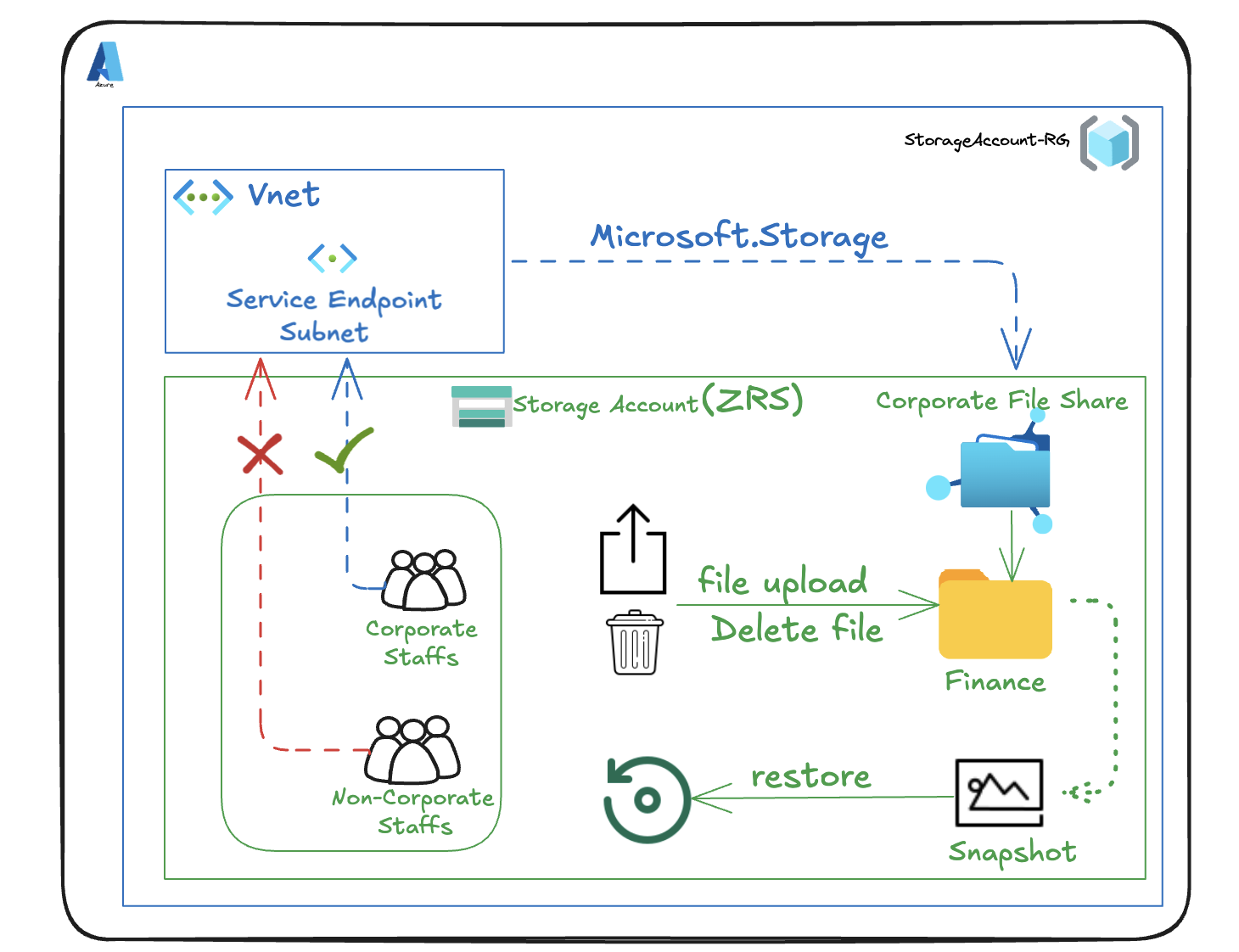
We’ll configure Azure Files to support shared file storage for the company’s finance department. The solution uses a Premium-tier storage account with ZRS redundancy to ensure performance and availability across zones. We’ll create a dedicated file share and directory for corporate use, enable snapshot protection to guard against accidental deletions, and test restore functionality. To secure access, we’ll restrict connectivity to a specific virtual network using service endpoints, and switch the storage account from public to selected network access only, ensuring that file access is tightly controlled and compliant with internal policies.
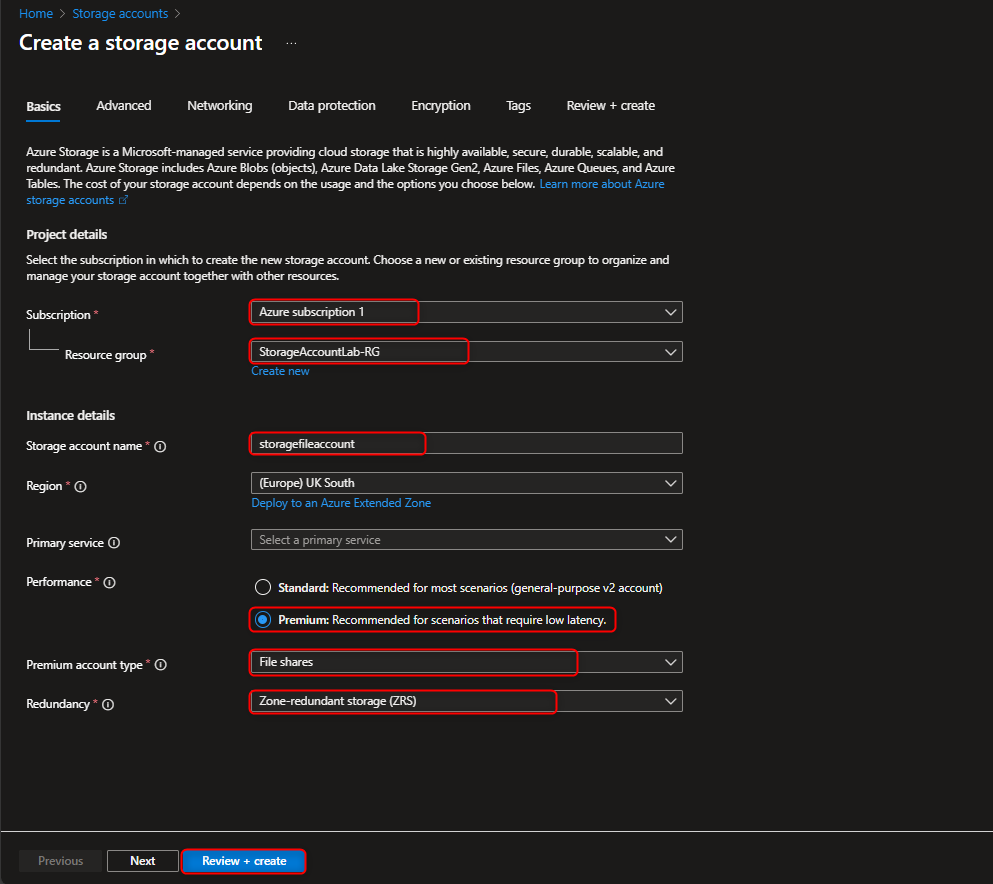
- Create a Zone Redundant storage account for the finance department’s shared files in the Resource Group **StorageAccountLab-RG".
Storage accounts -> + Create -> Resource group -> Create new -> [enter name] -> OK -> Storage account name -> [enter name] -> Performance -> Premium -> Premium account type -> File shares -> Redundancy -> Zone-redundant storage -> Review -> Create -> Go to resource
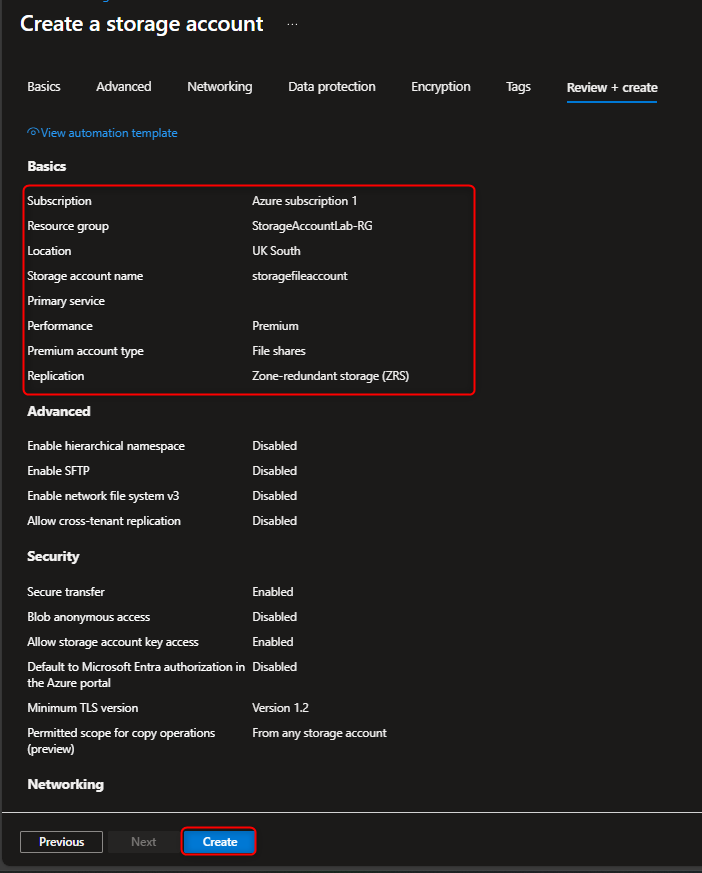
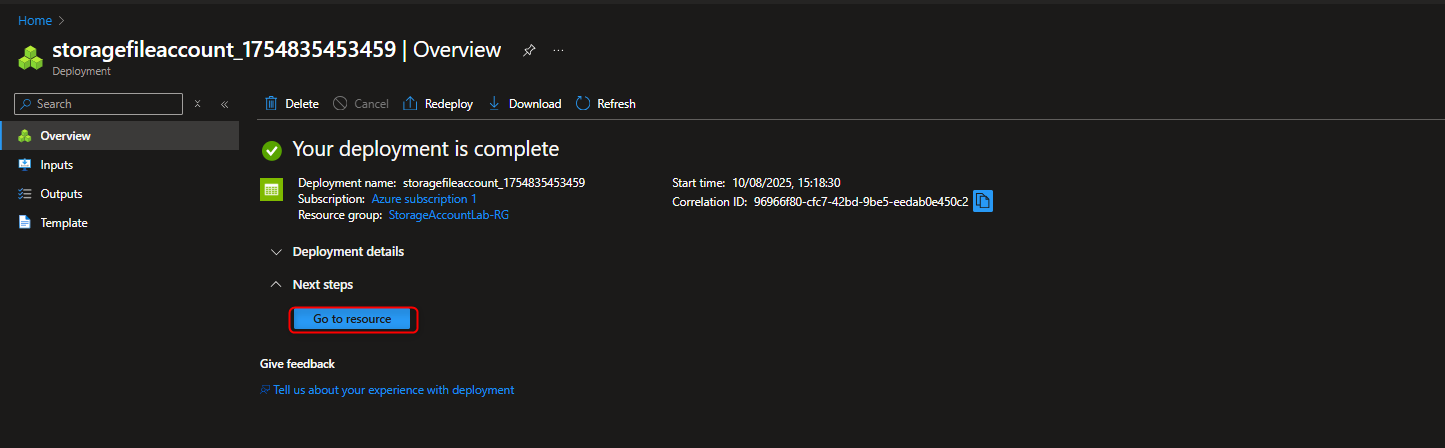
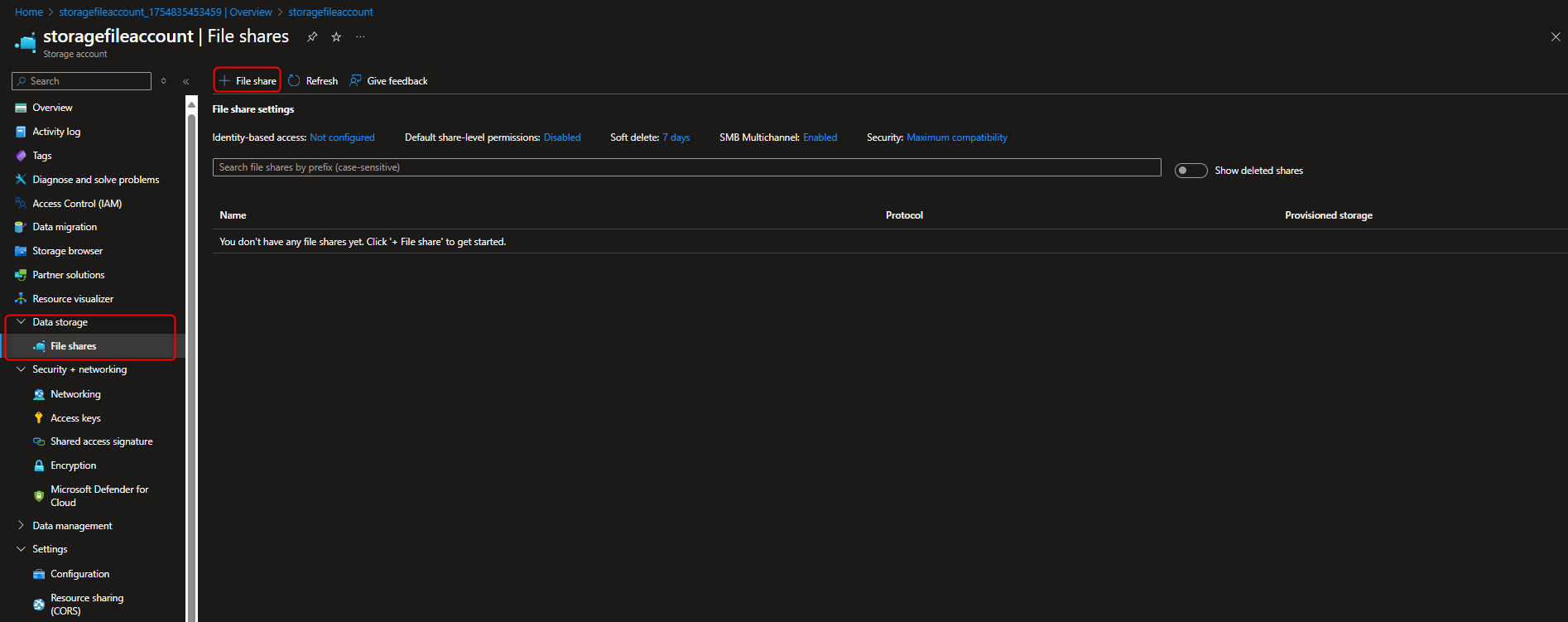
- Create file share for the corporate office
File shares -> + File share -> Name -> [enter a name] -> Go to back up tab to disable backup -> Create
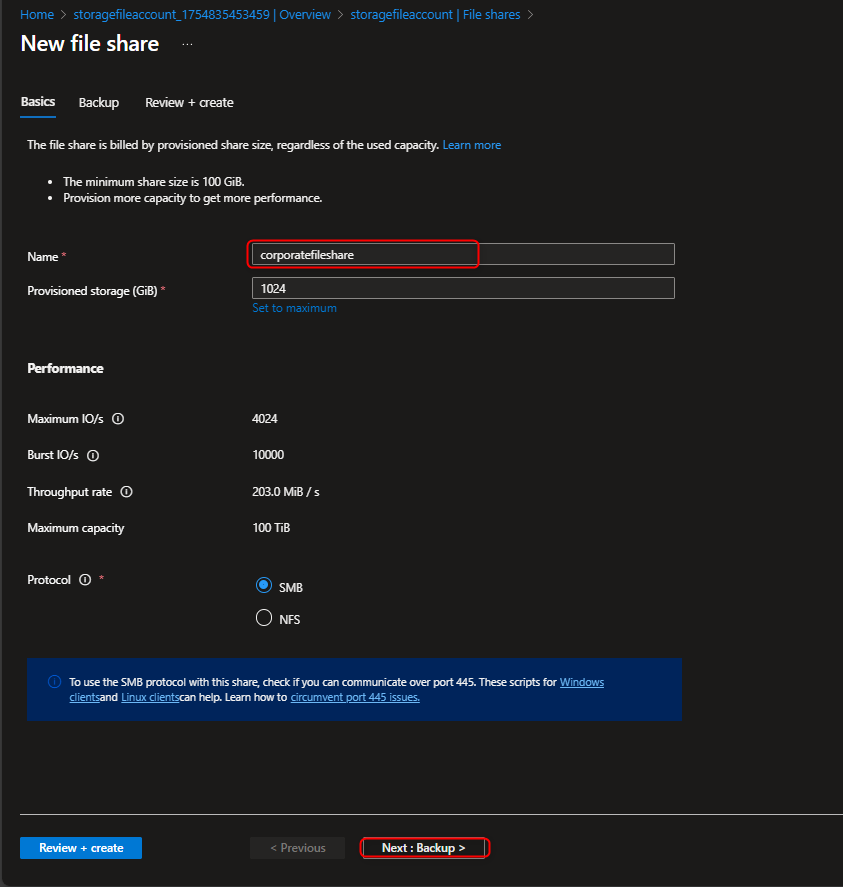
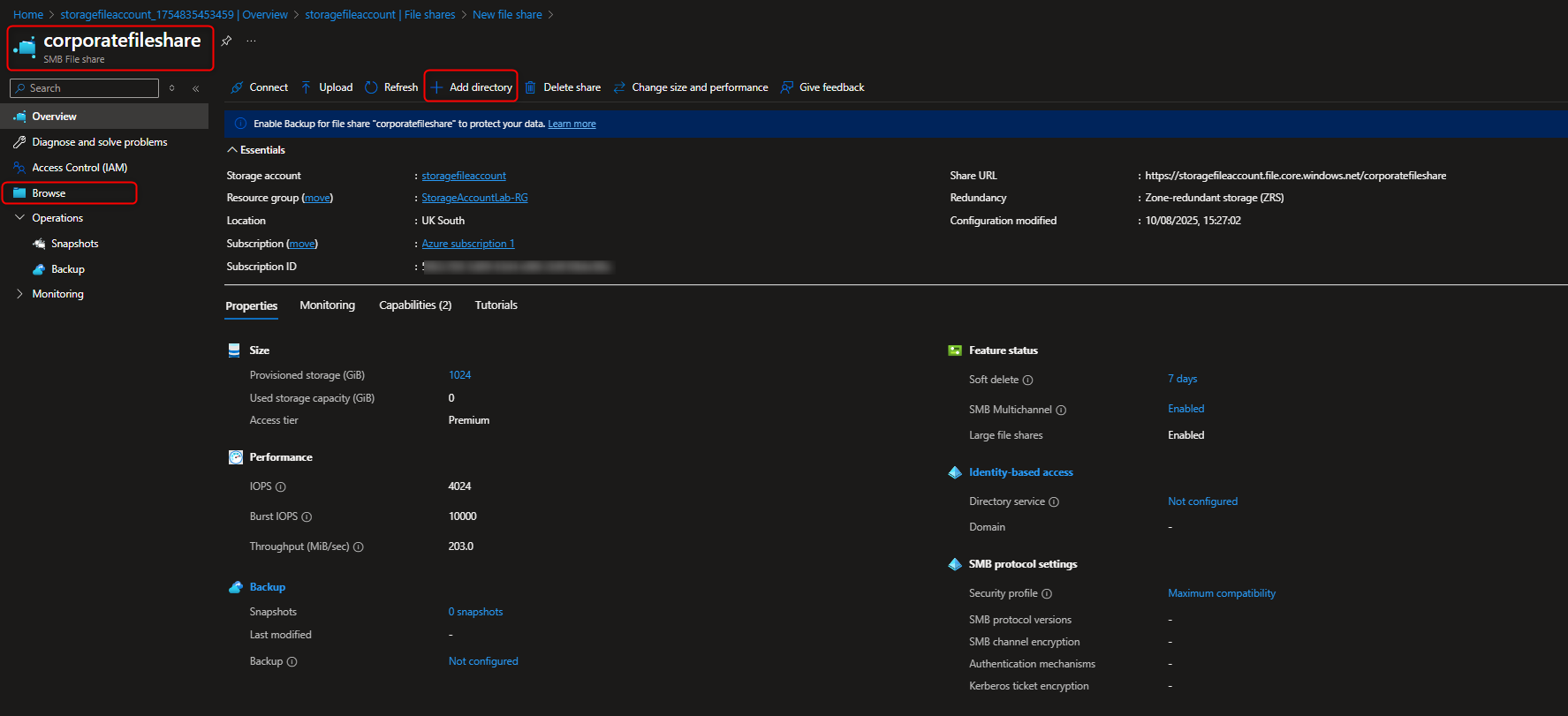
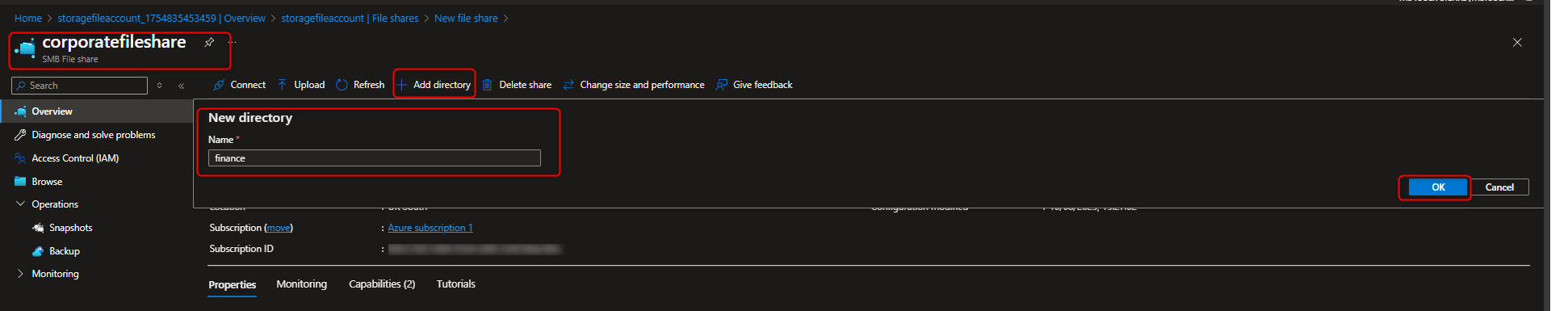
- Configure a directory for the finance department
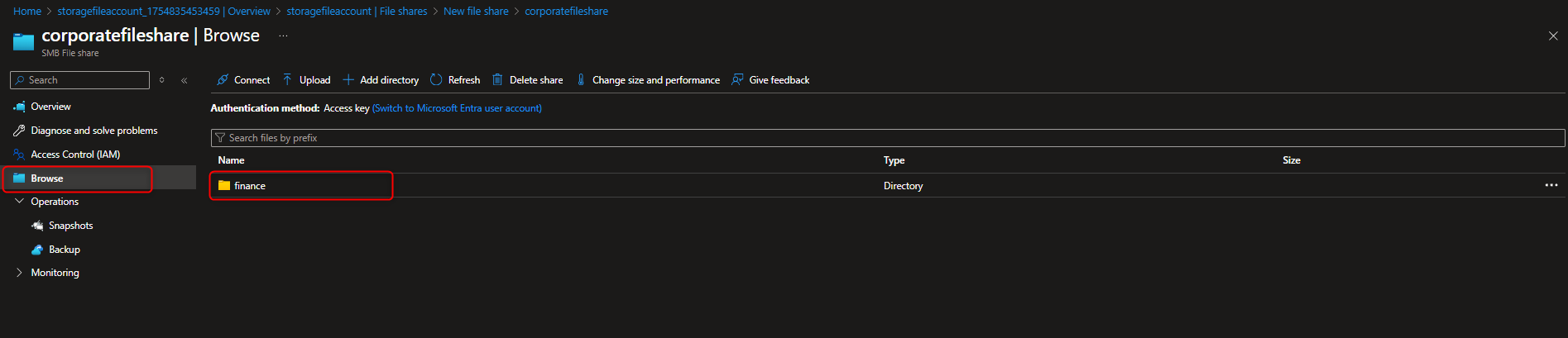
Select your file share -> + Add directory -> Name -> finance -> Browse -> [select finance directory] -> Upload -> [select a file]
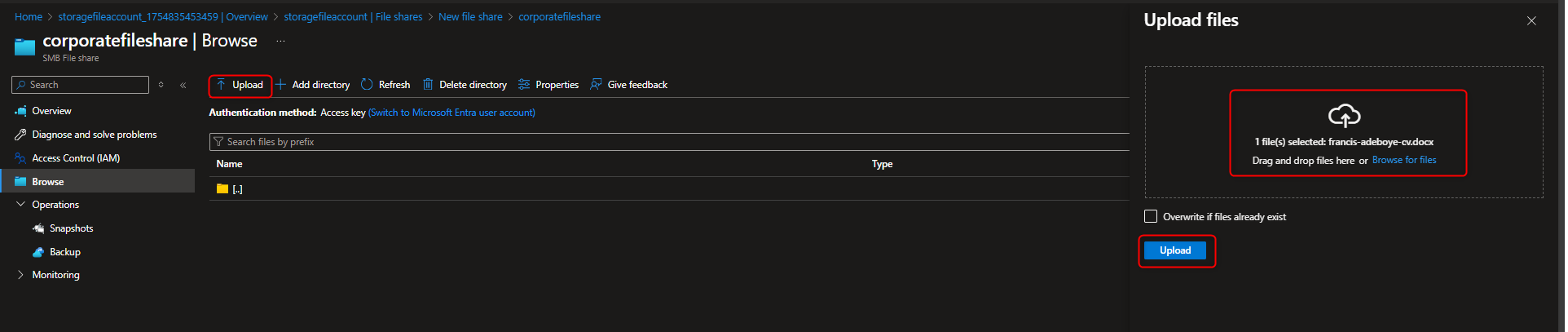
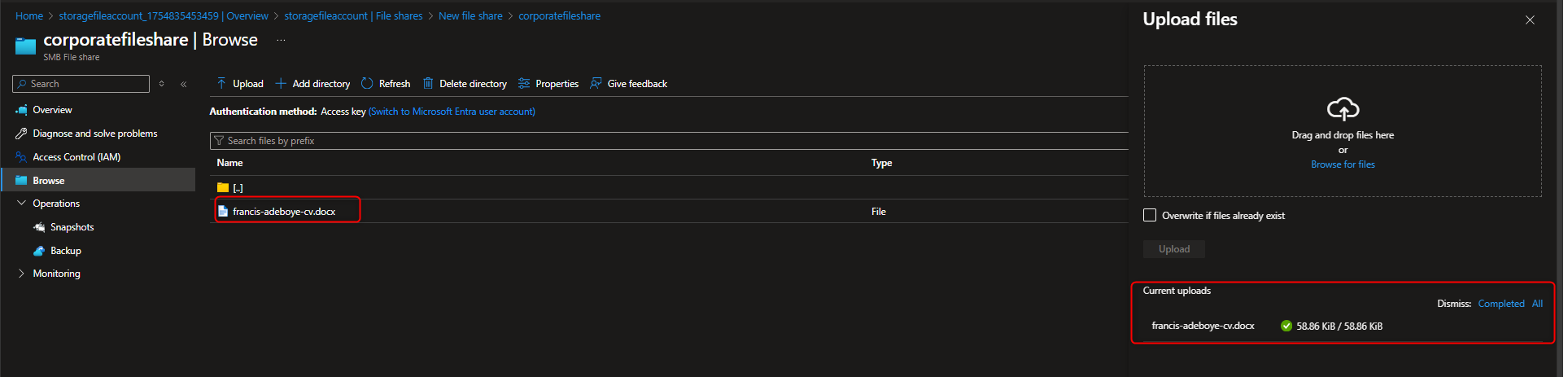
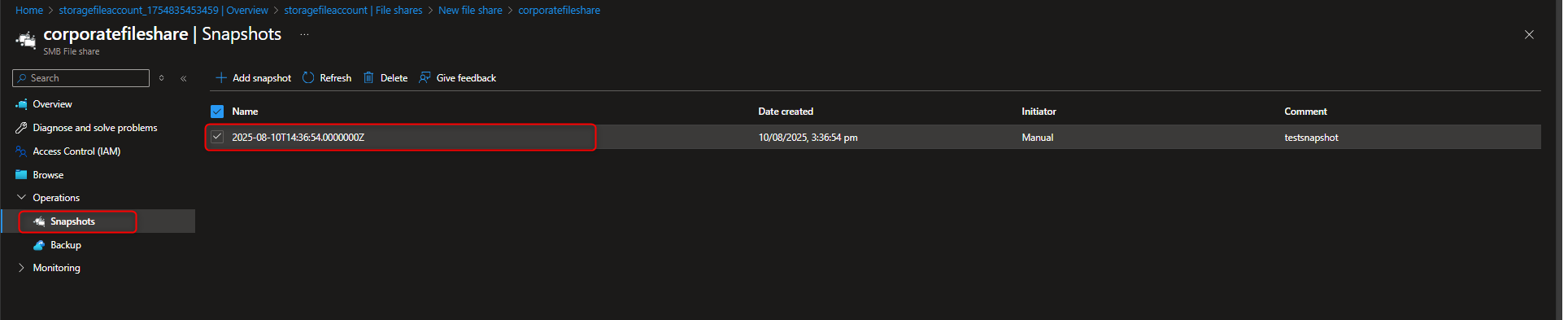
- Create Snapshot of the file share to protect against accidental deletion
Select your file share -> Operations -> Snapshots -> + Add snapshot -> OK -> Select your snapshot -> [verify file directory]
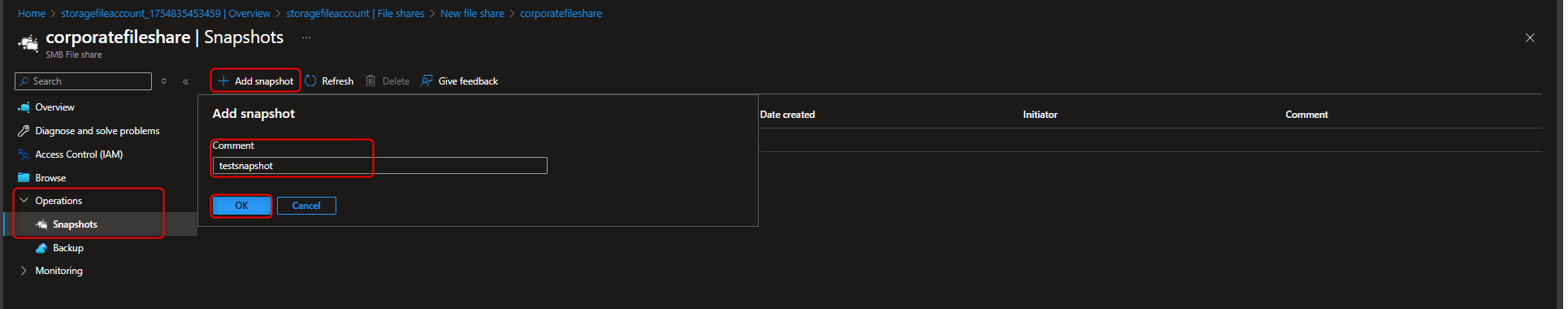
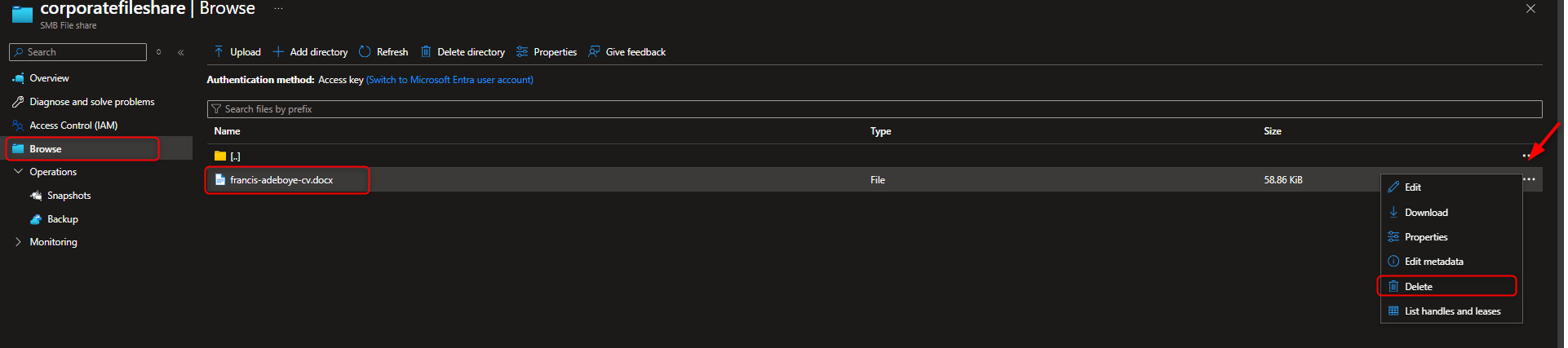
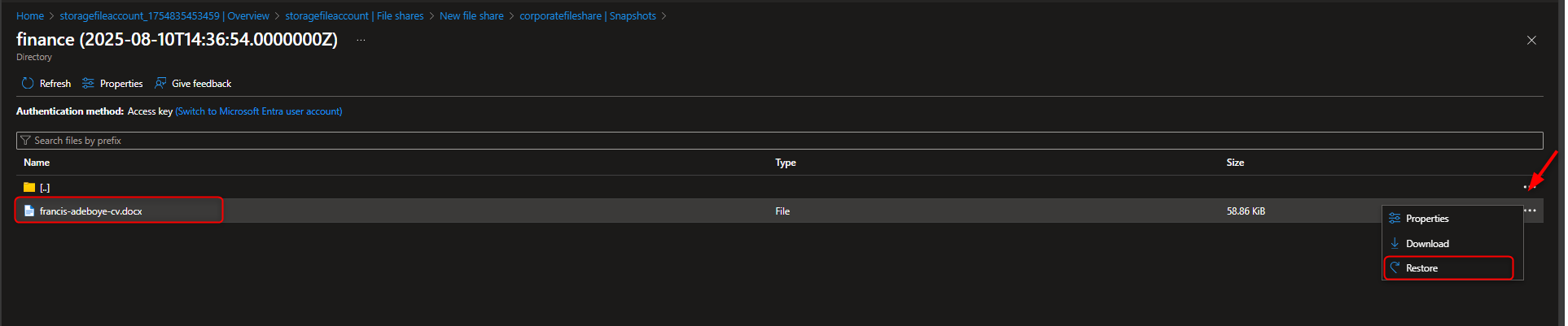
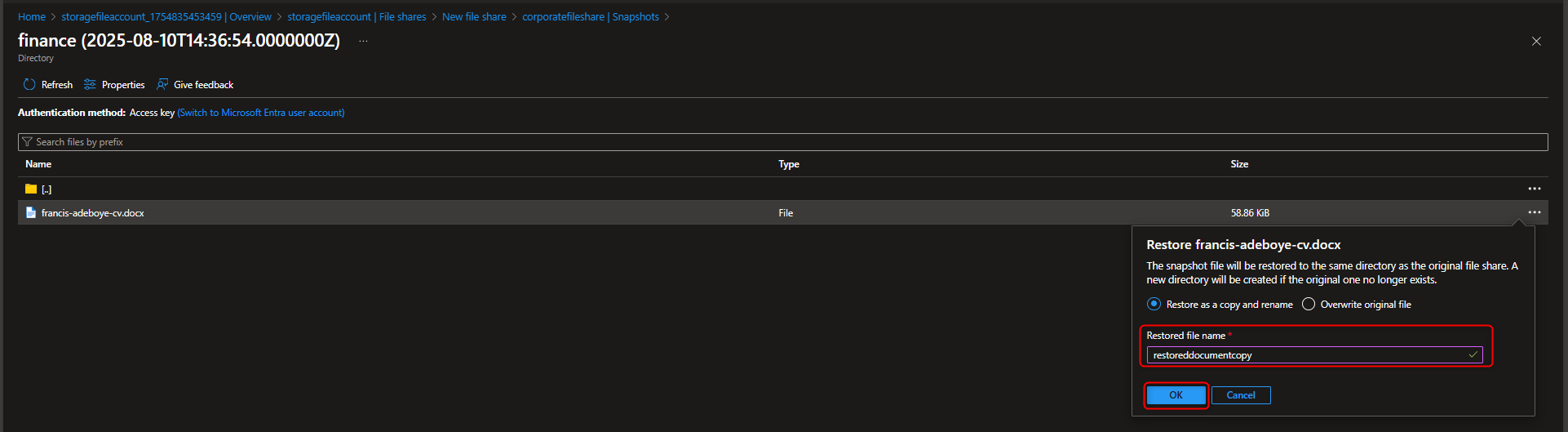
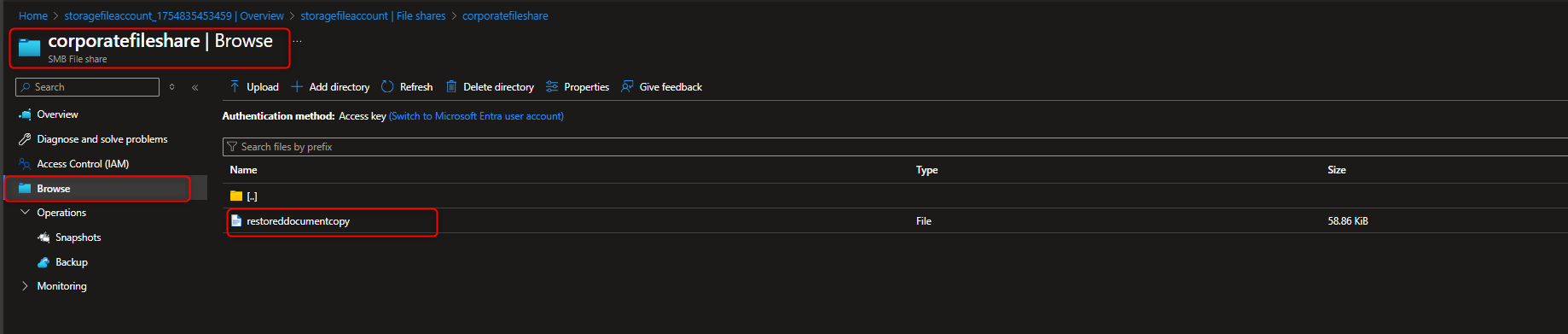
- Restore a File from a Snapshot
Return to file share -> Browse -> [locate and select file] -> Properties -> Delete -> Yes -> Snapshots -> [select snapshot] -> [navigate to file] -> Restore -> [enter new file name] -> Verify
- Configure storage access restriction to selected Virtual Network & Subnet
Virtual networks -> Create -> [select resource group] -> [name virtual network] -> Review + create -> Create -> Go to resource -> Settings -> Subnets -> default -> Service endpoints -> Services -> Microsoft.Storage -> Save
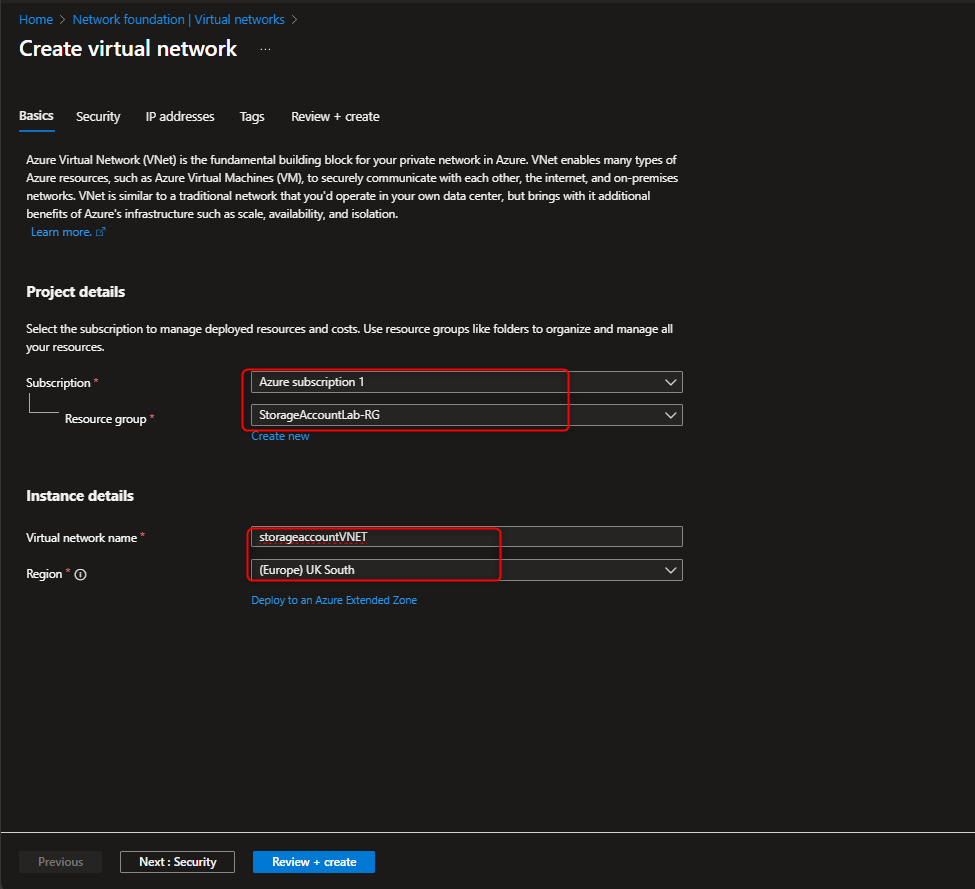
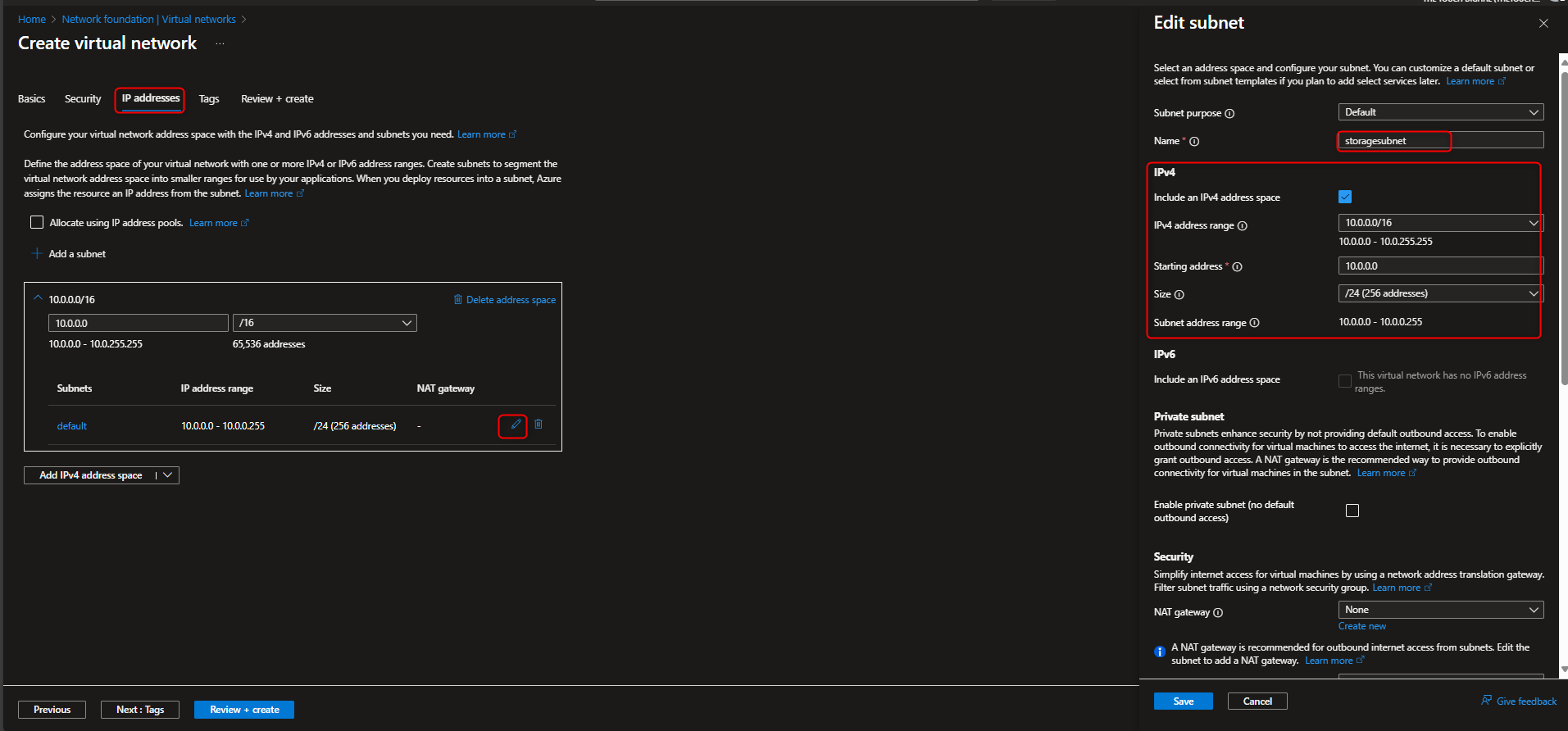
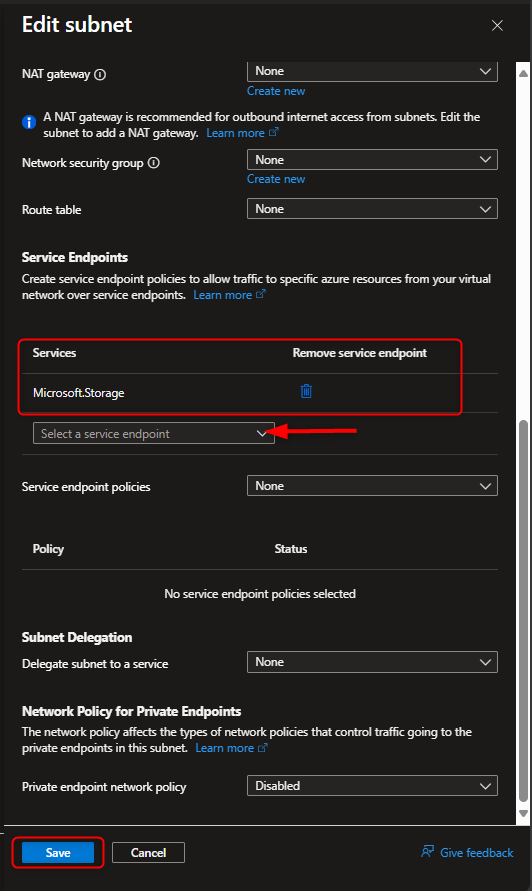
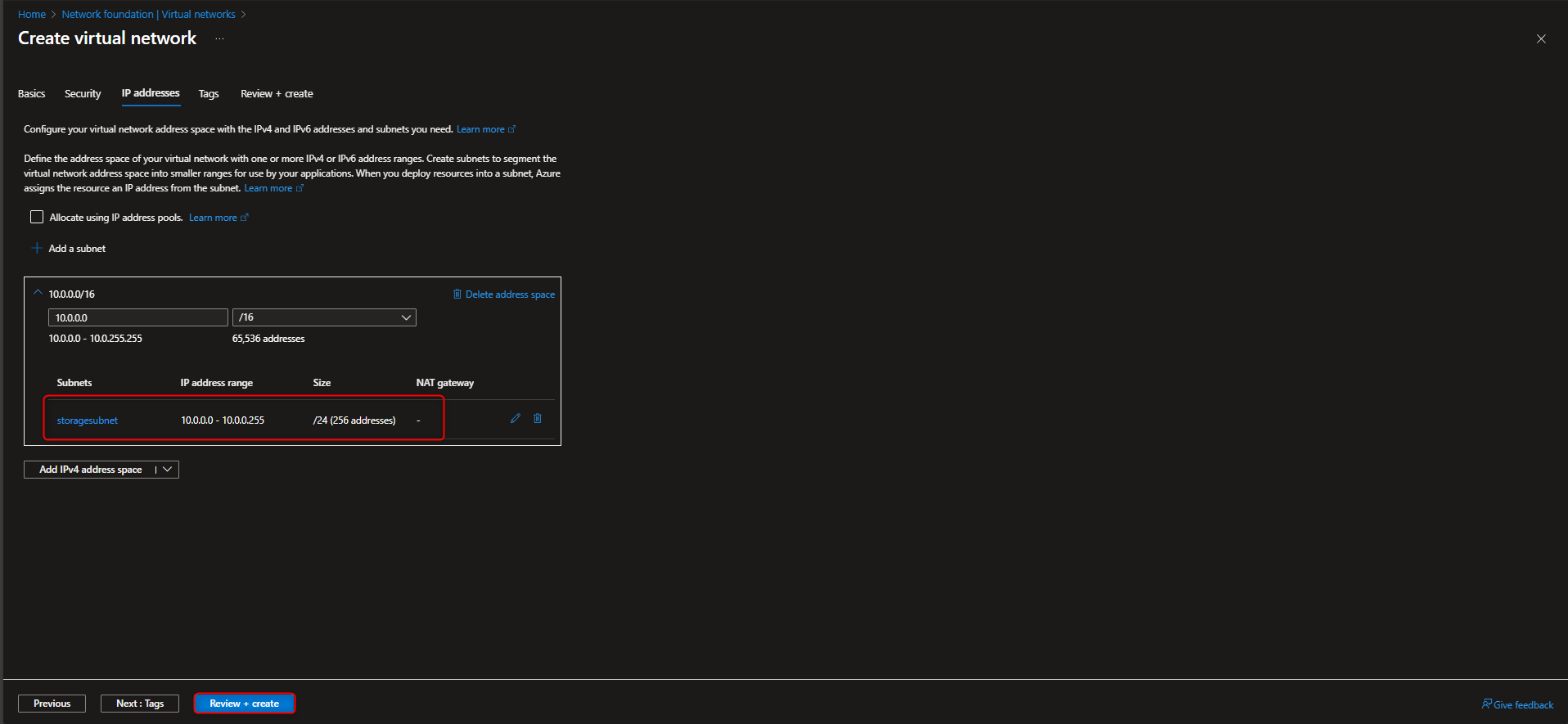
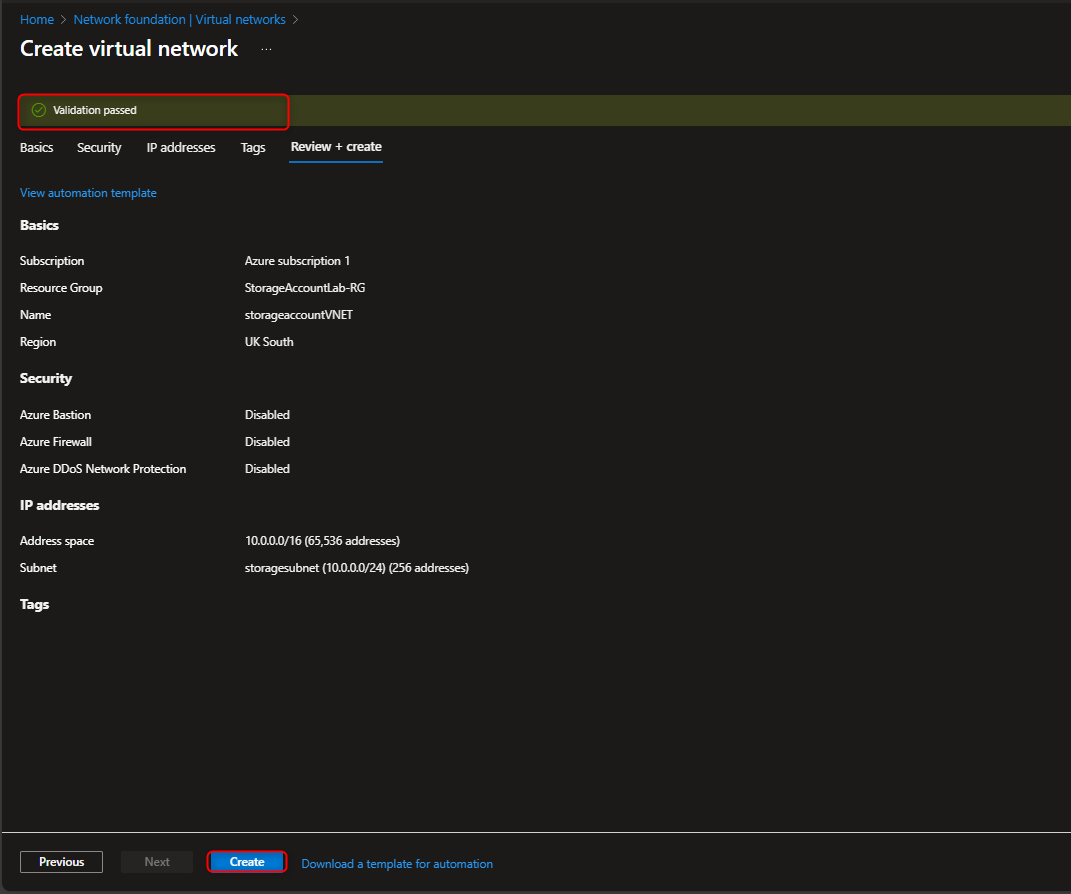
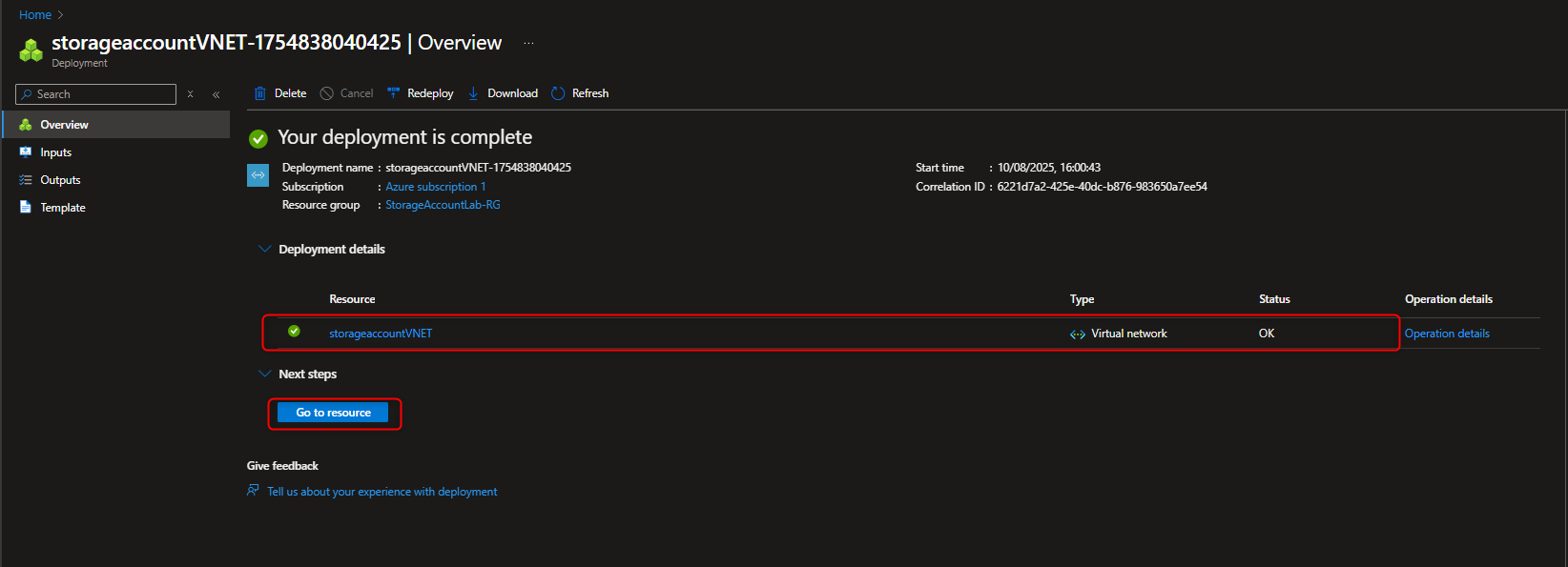
- Restrict storage account to only access from selected Virtual Network
Return to files storage account -> Security + networking -> Networking -> Public network access -> Enabled from selected virtual networks and IP addresses -> Virtual networks -> Add existing virtual network -> [select virtual network and subnet] -> Add -> Save
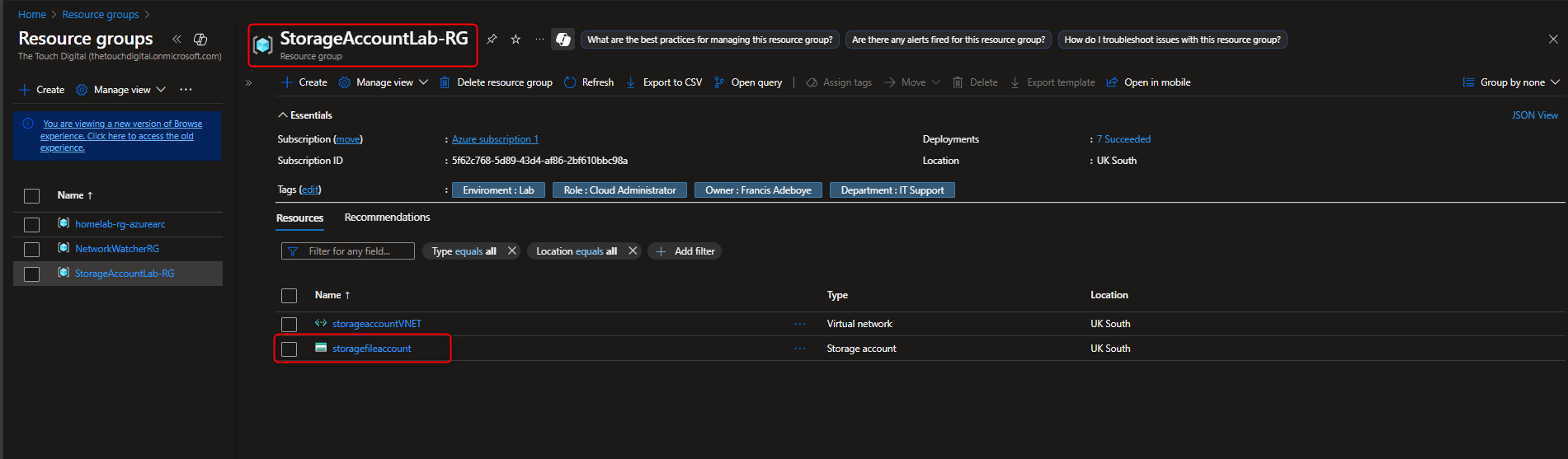
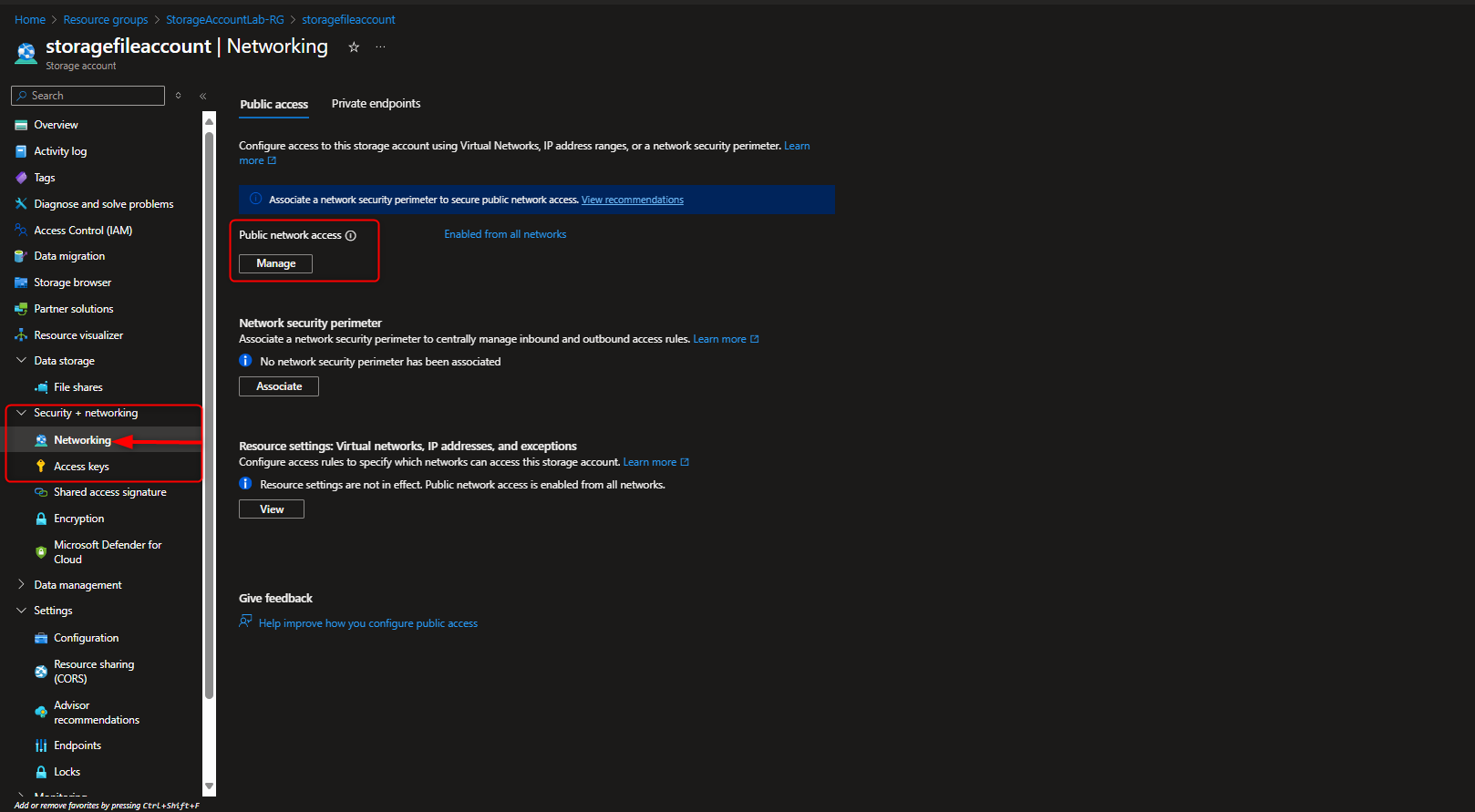
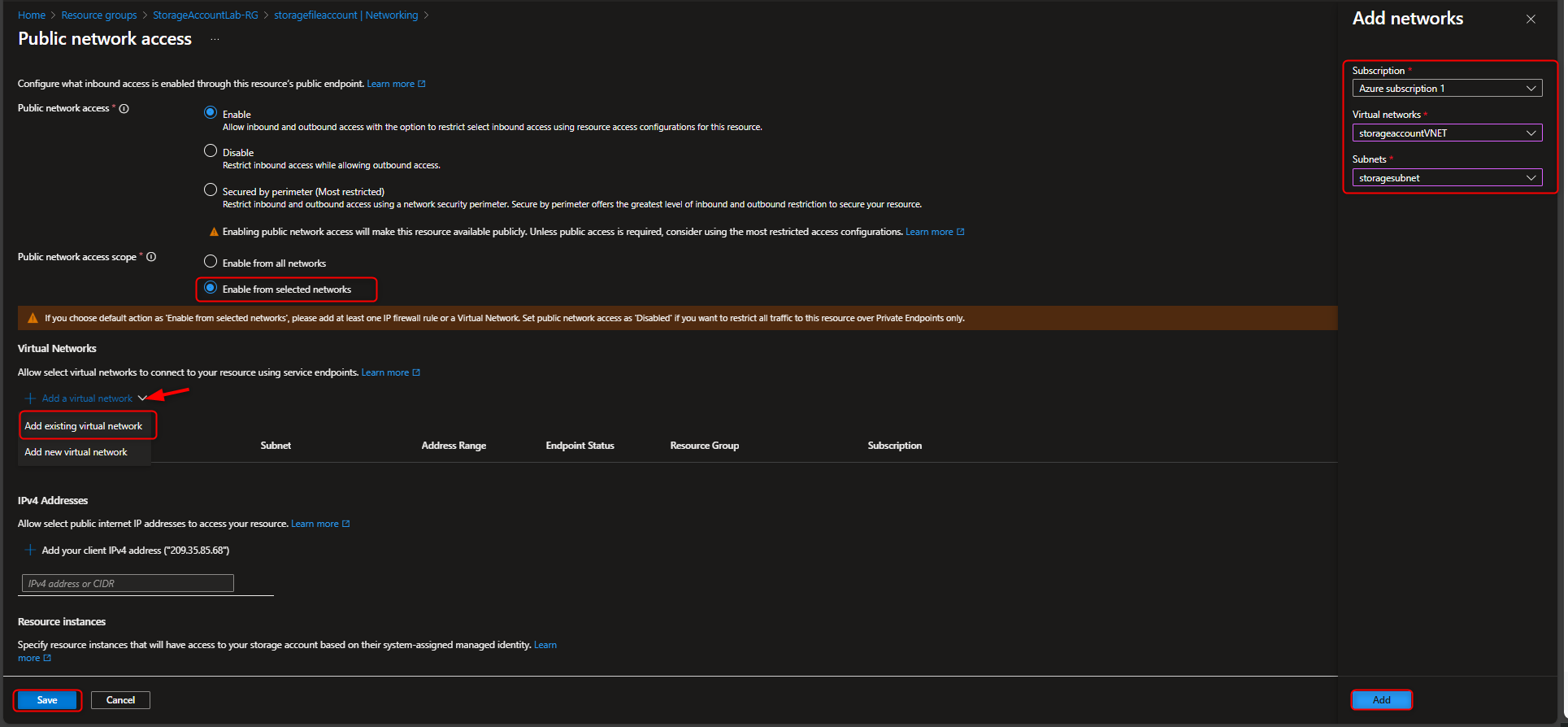
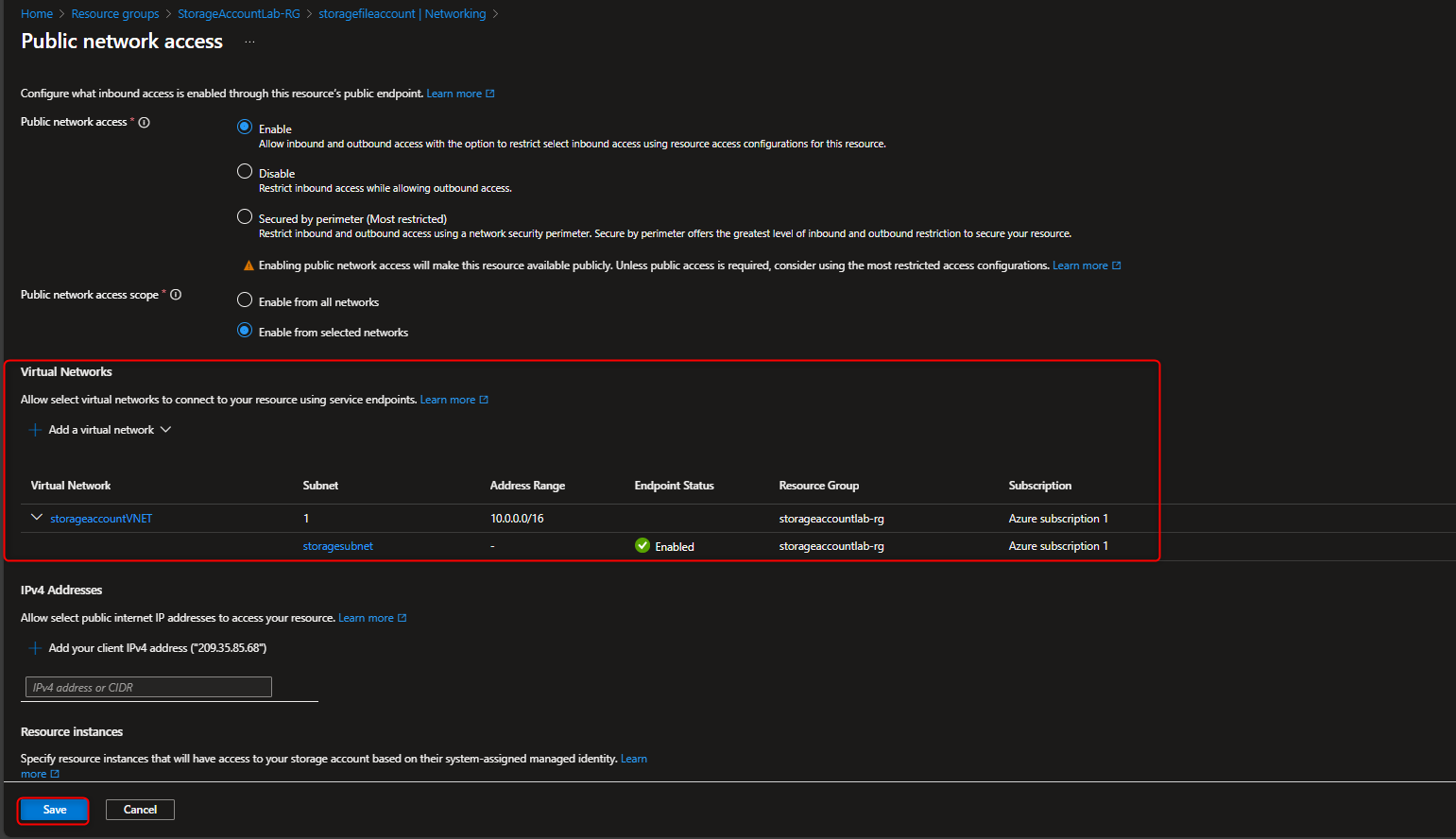
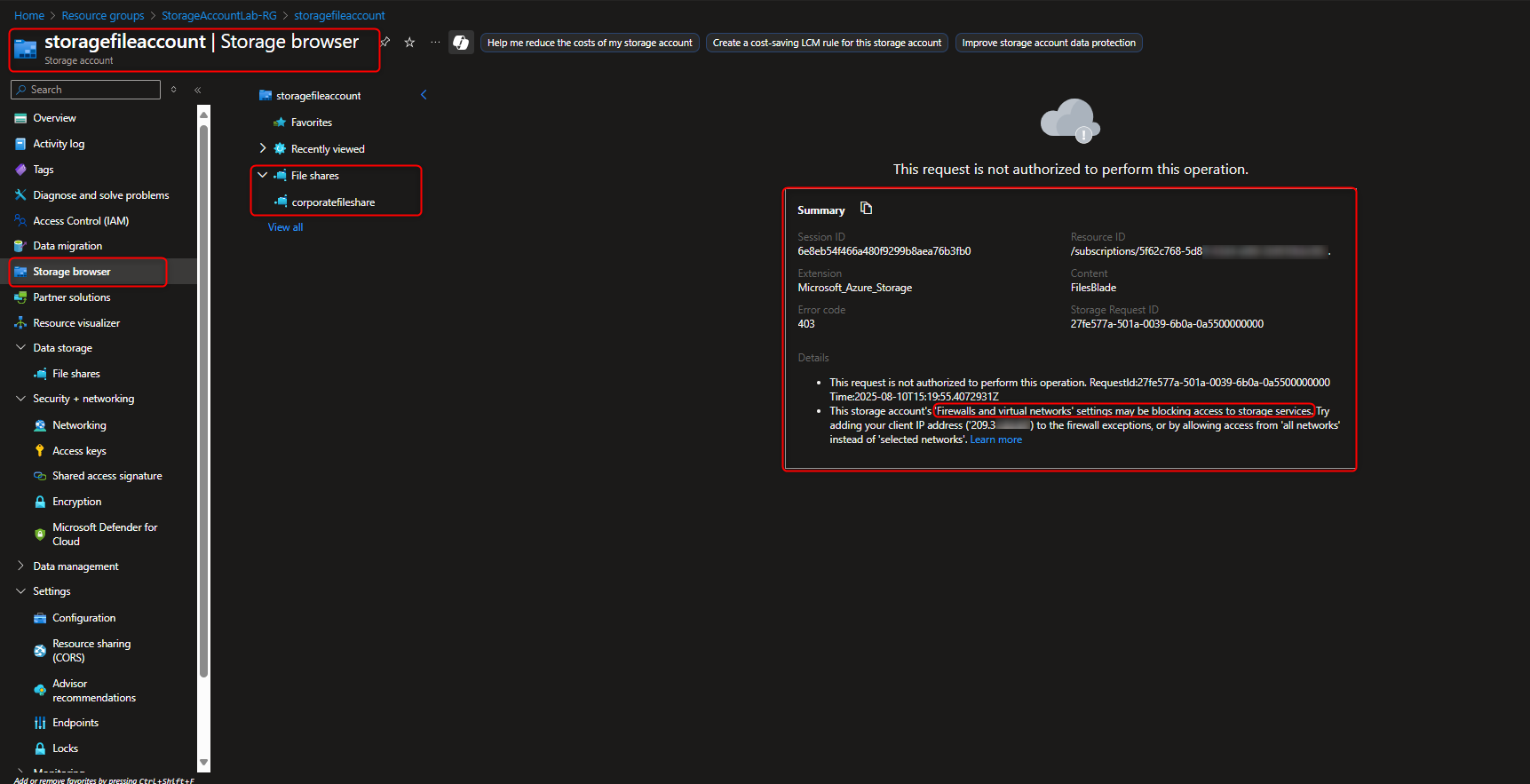
- Verify Access Restriction
Storage browser -> [navigate to file share] -> Verify message (“not authorized to perform this operation”)
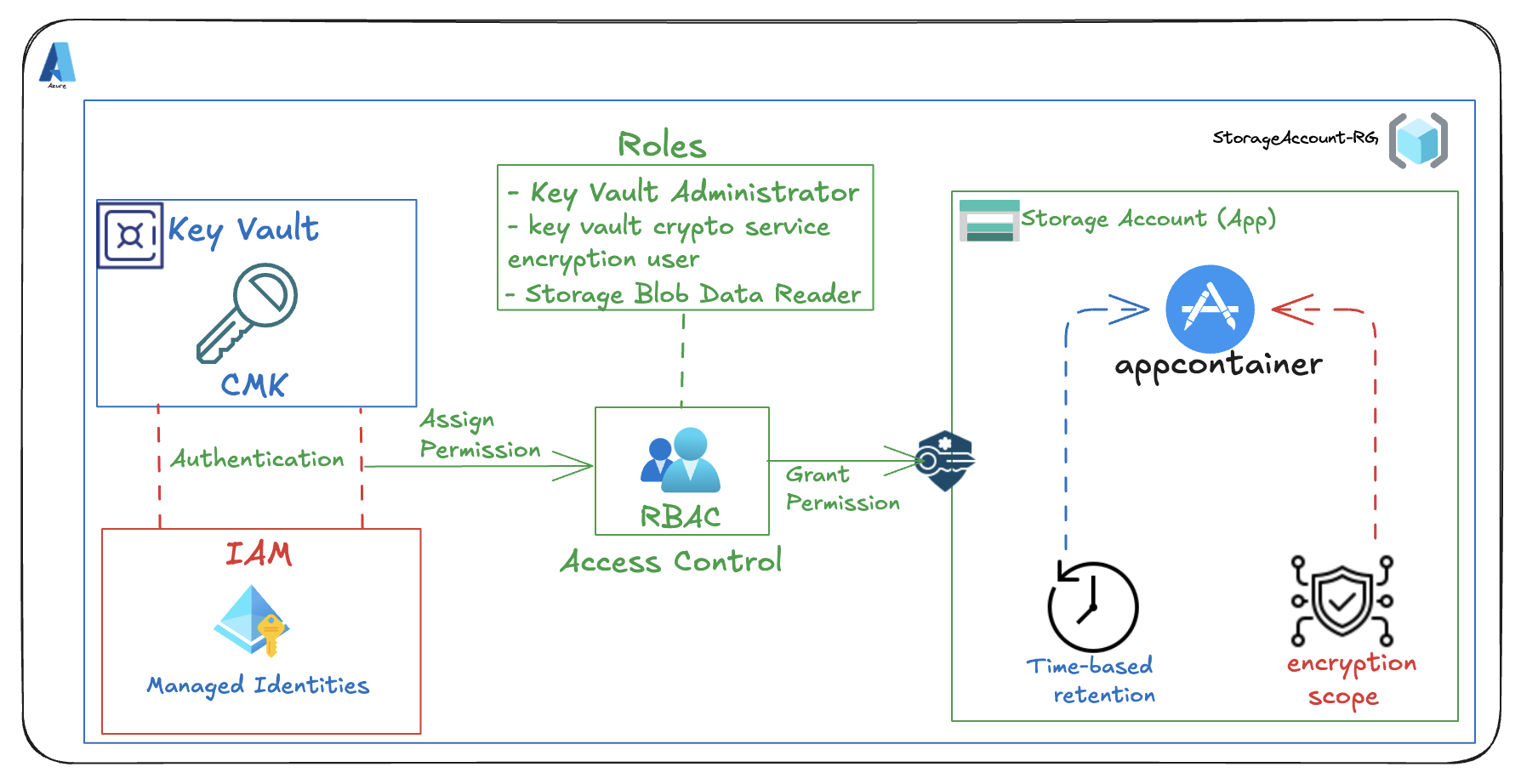
🔐 Securing Azure Blob Storage for App Development Using Key Vault, Encryption, Managed Identities & Immutable Protection
In this task, we’re configuring a Secure Azure Blob Storage solution to support the development of a new internal application. The focus is on enforcing strict access controls using managed identities and access keys, while applying role-based access control (RBAC) to streamline permissions across development and testing environments. To safeguard critical test data, we’ll enable immutable blob protection, ensuring that once written, data cannot be altered or deleted during retention. This setup supports secure automation, identity-driven access, and robust data integrity—ideal for modern app development workflows that demand both agility and compliance.
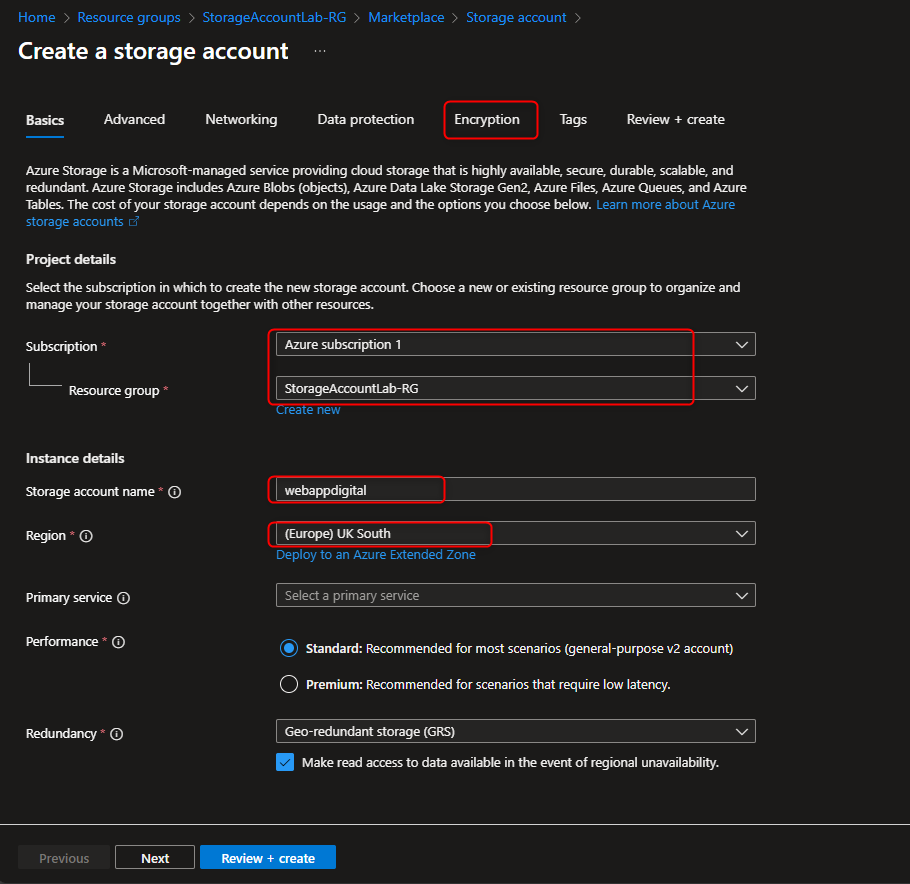
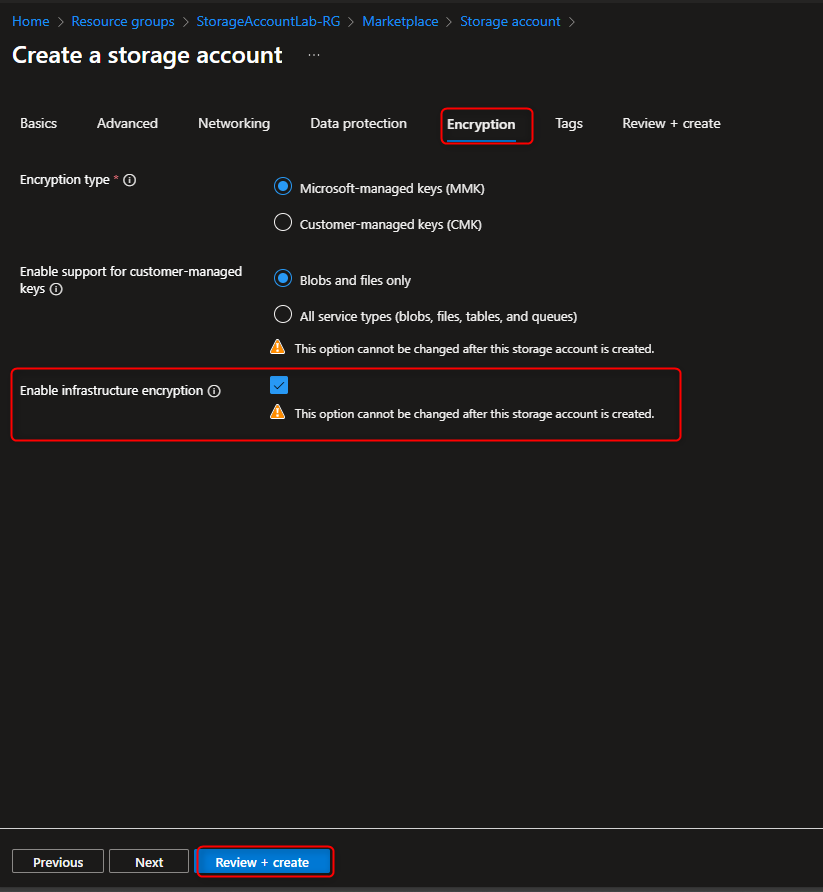
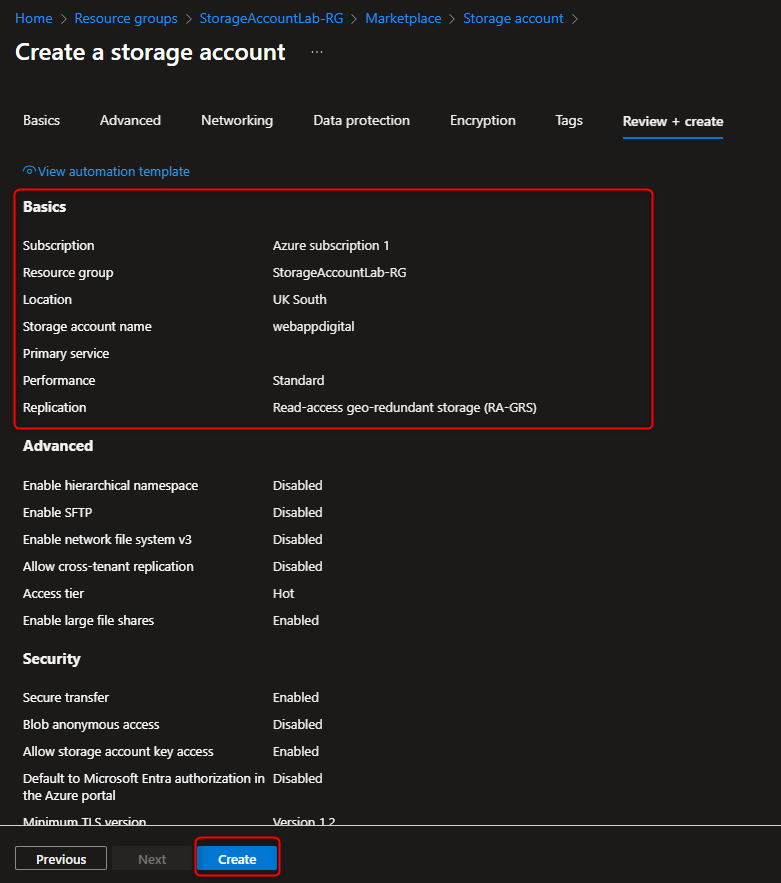
- Create Storage Account with Infrastructure Encryption Enabled
Storage accounts -> + Create -> Resource group -> Create new -> [name your resource group] -> OK -> Storage account name -> [enter a name] -> Encryption Tab -> Enable infrastructure encryption -> Review + Create -> Create
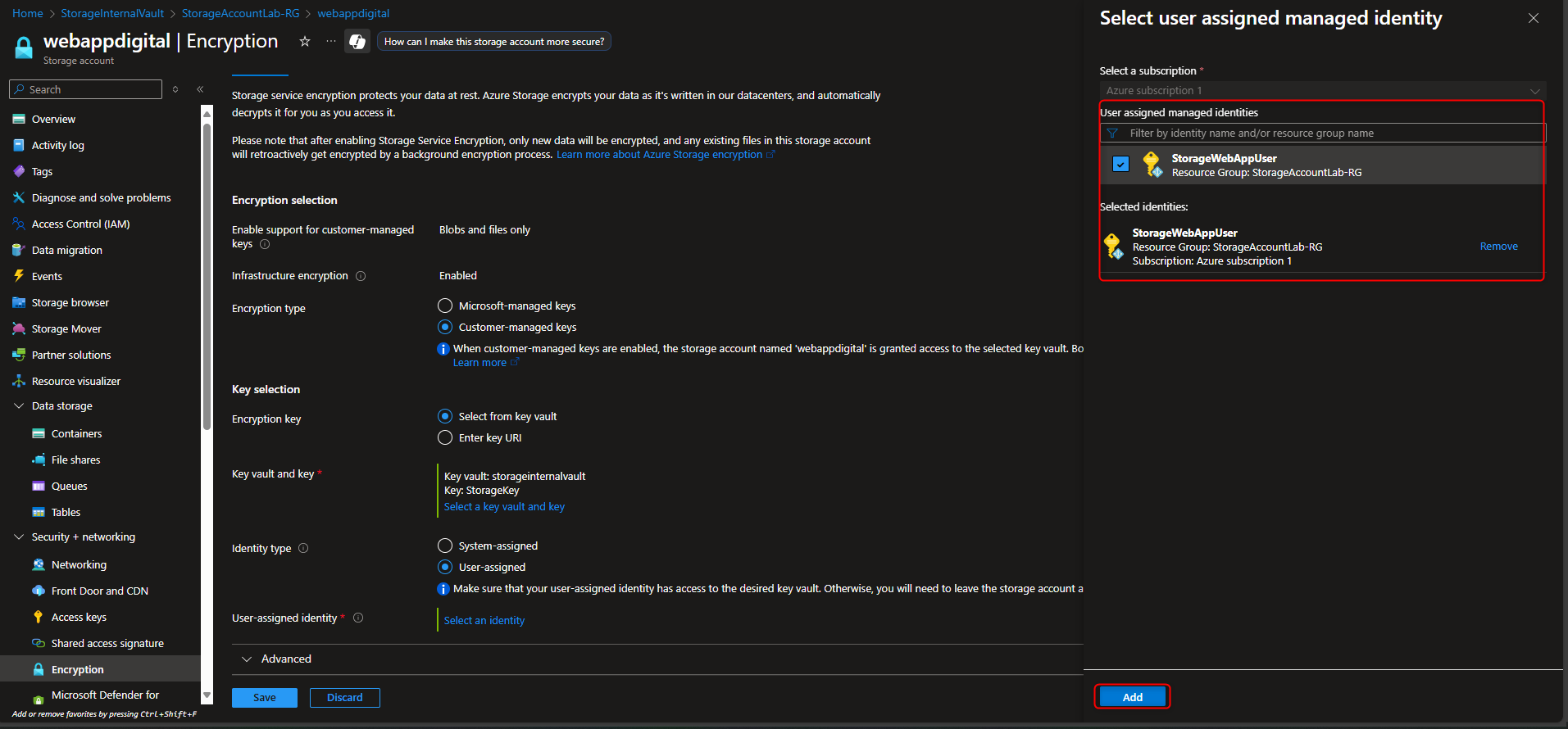
- Create User-Assigned Managed Identity
Managed identities -> Create -> [select your resource group] -> Name -> [give it a name] -> Review and create -> Create
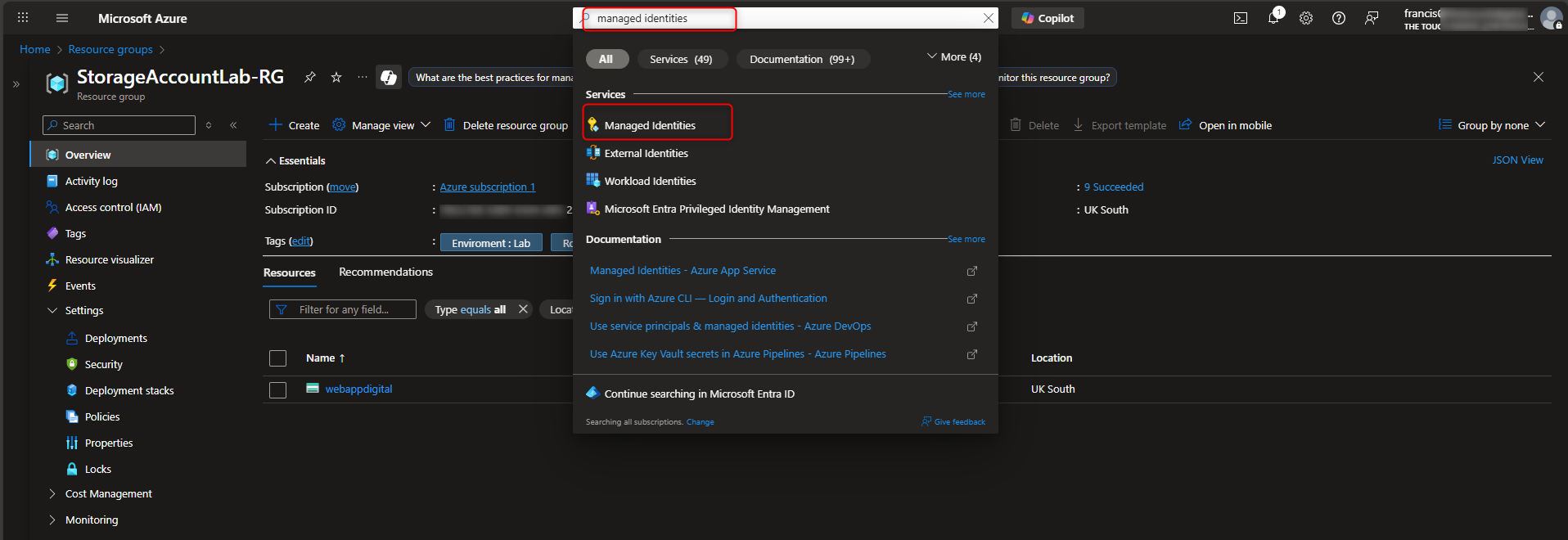
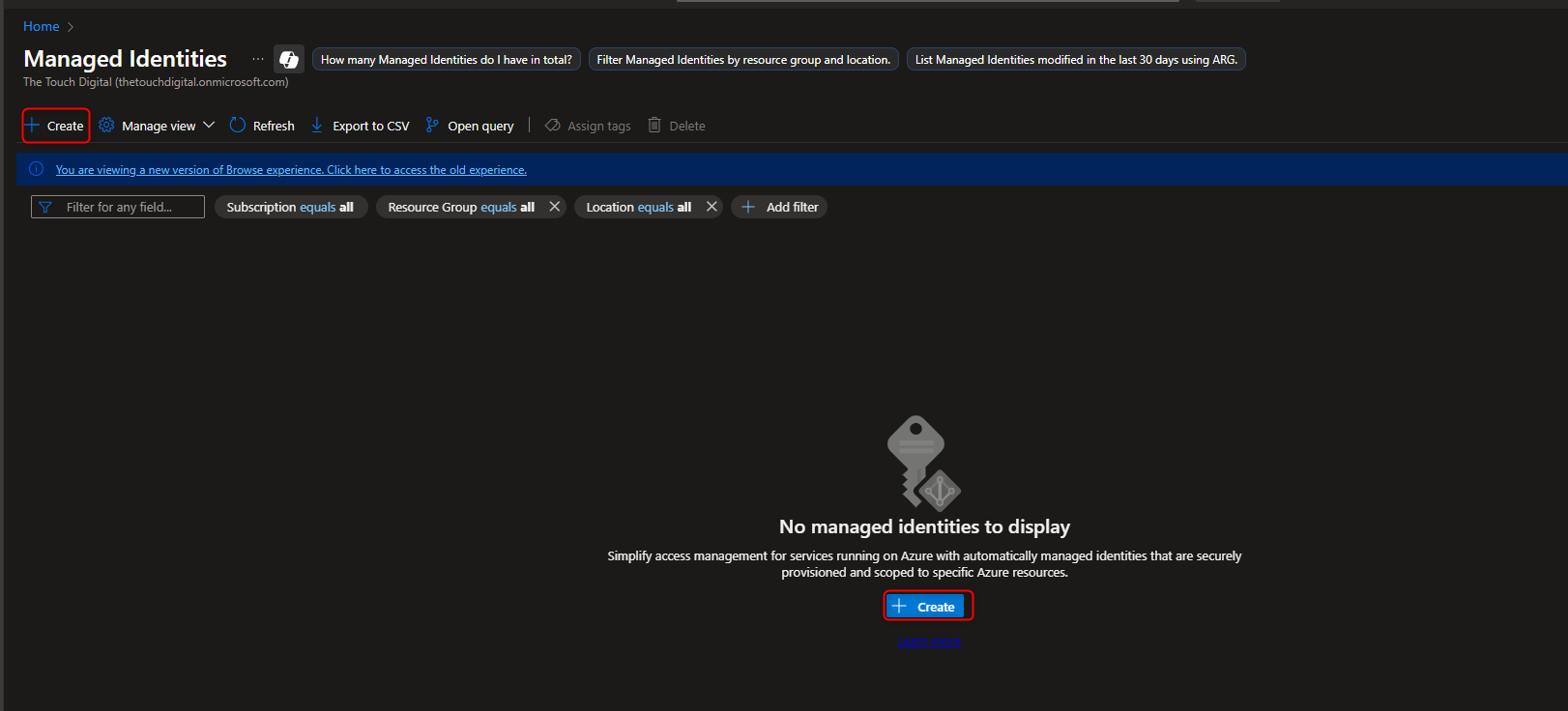
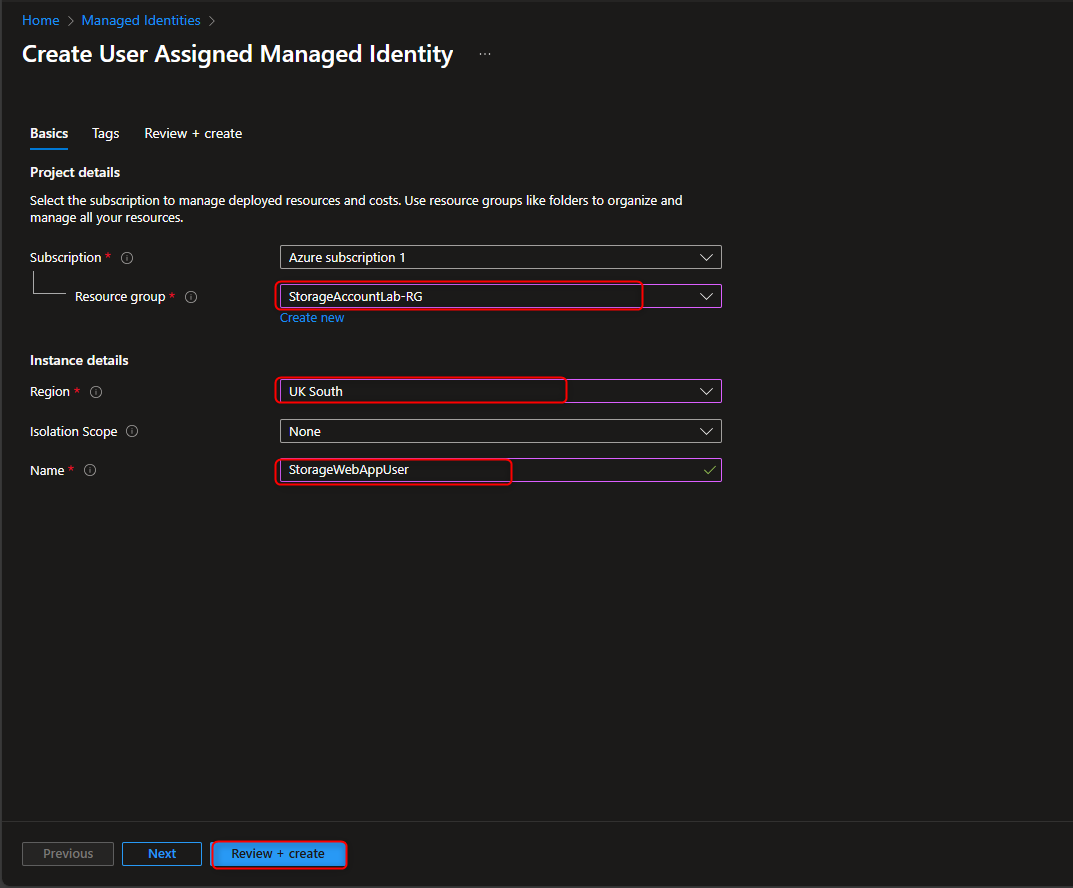
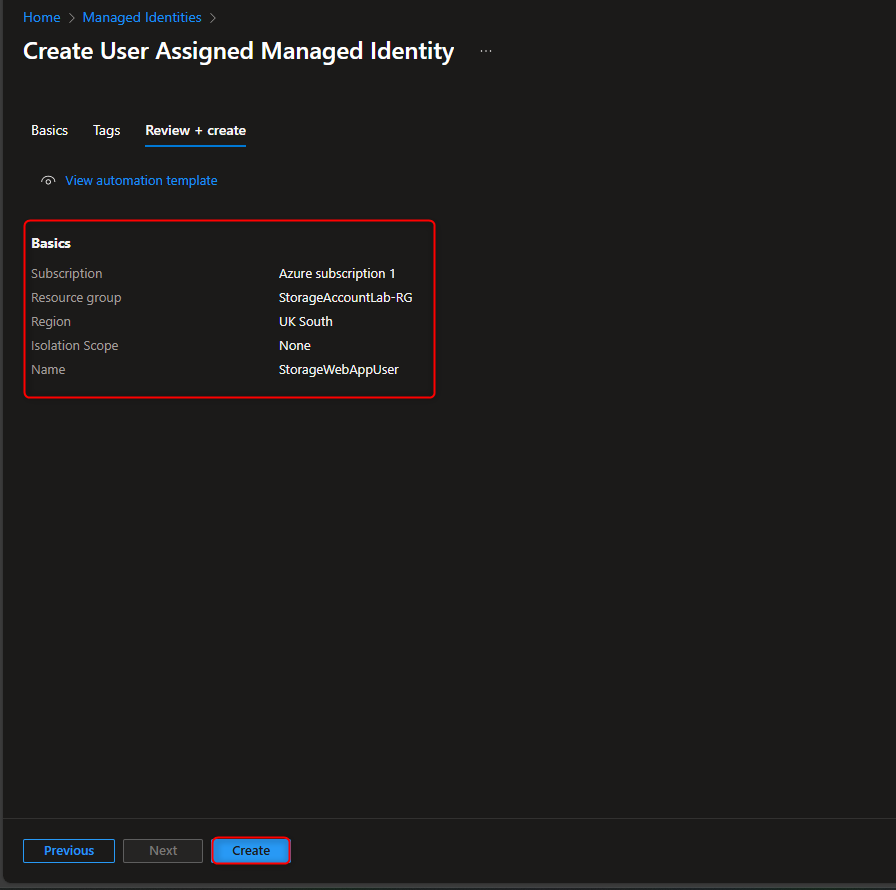
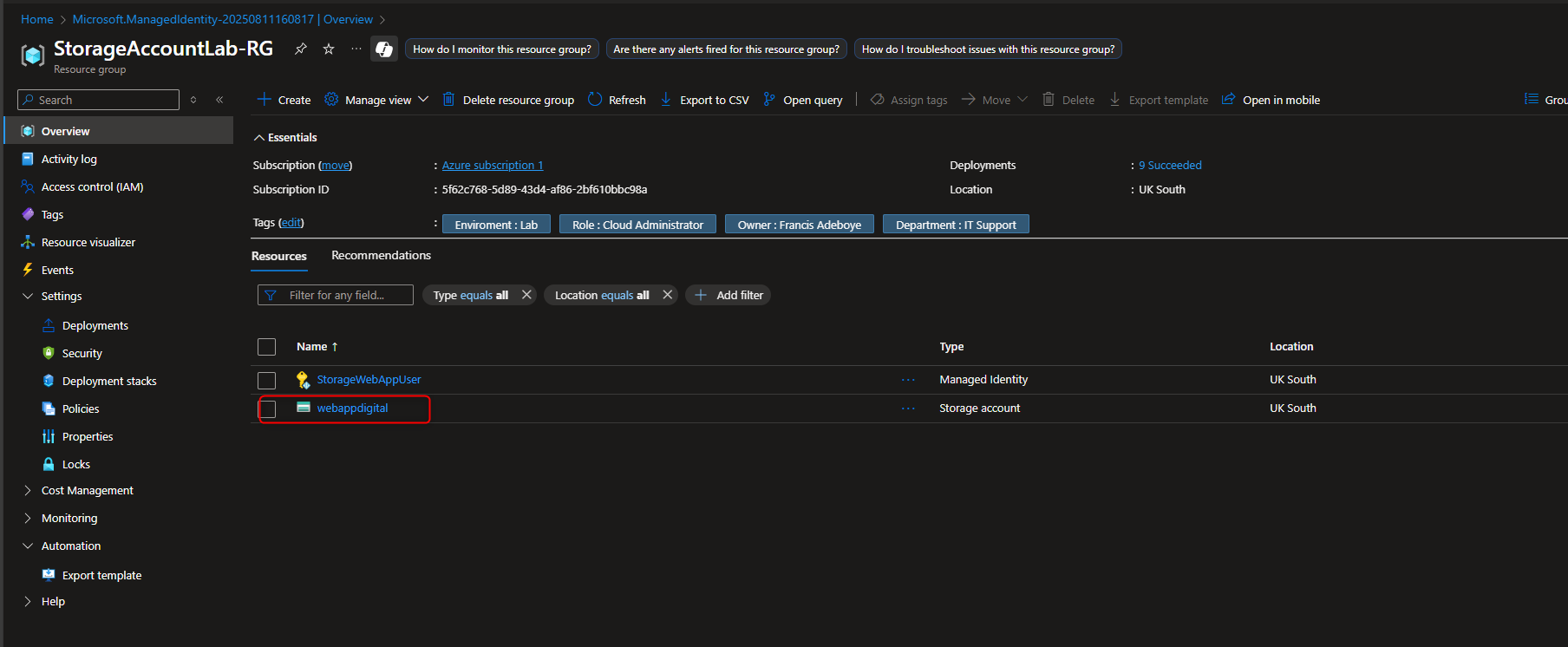
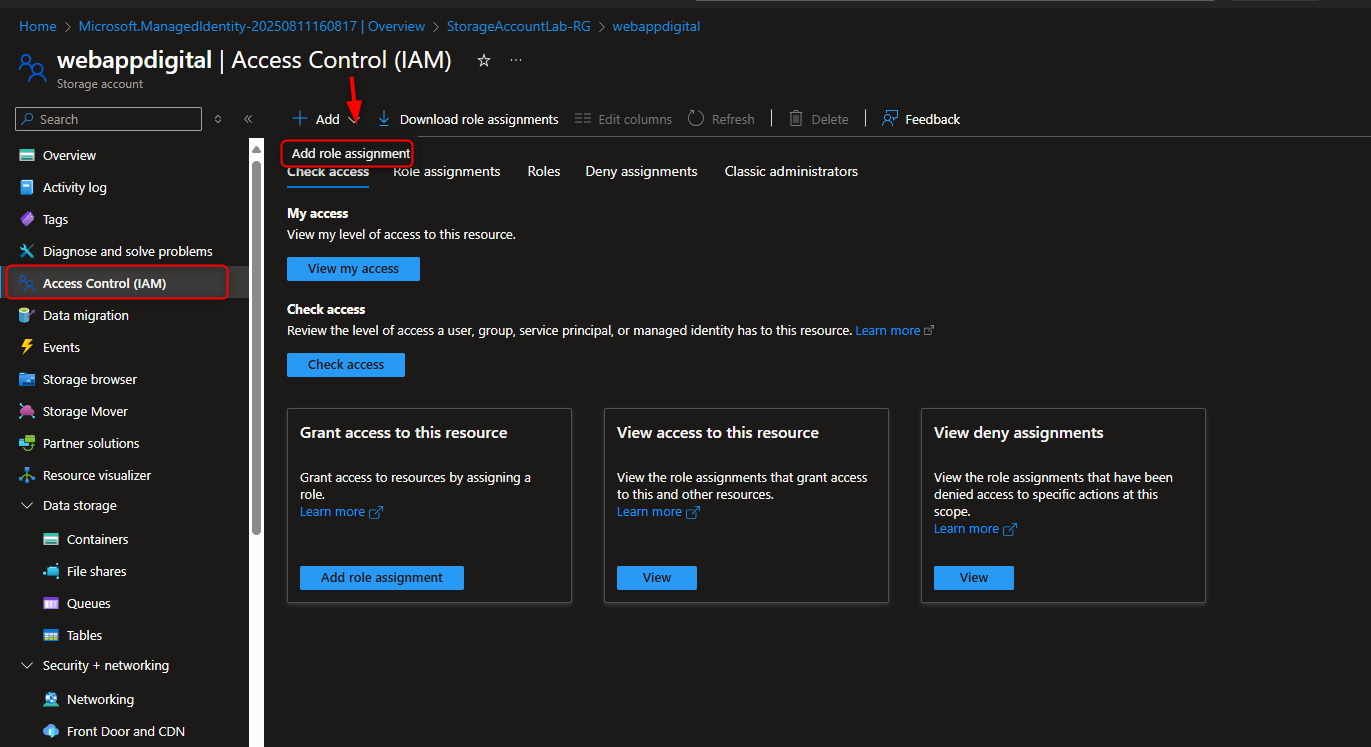
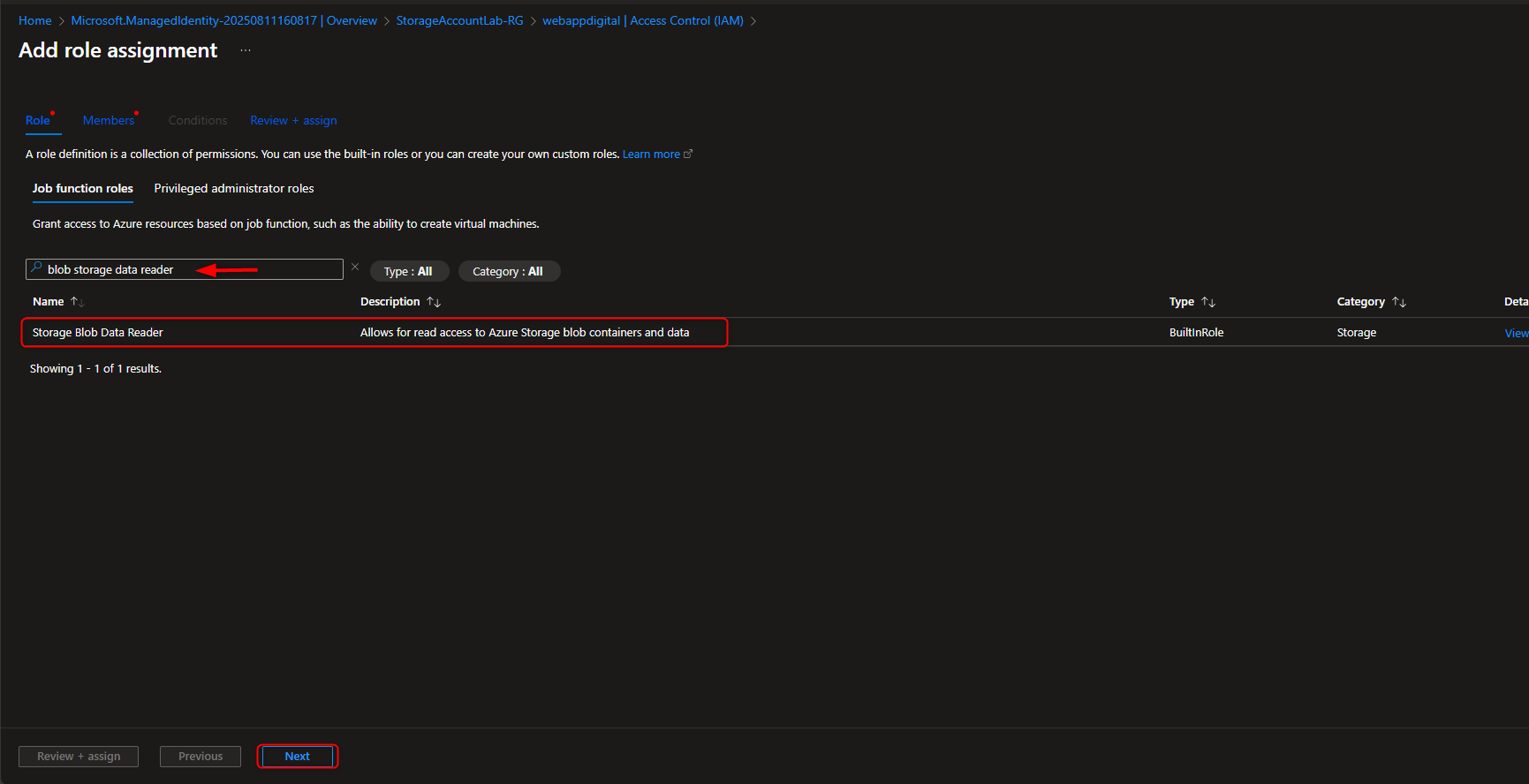
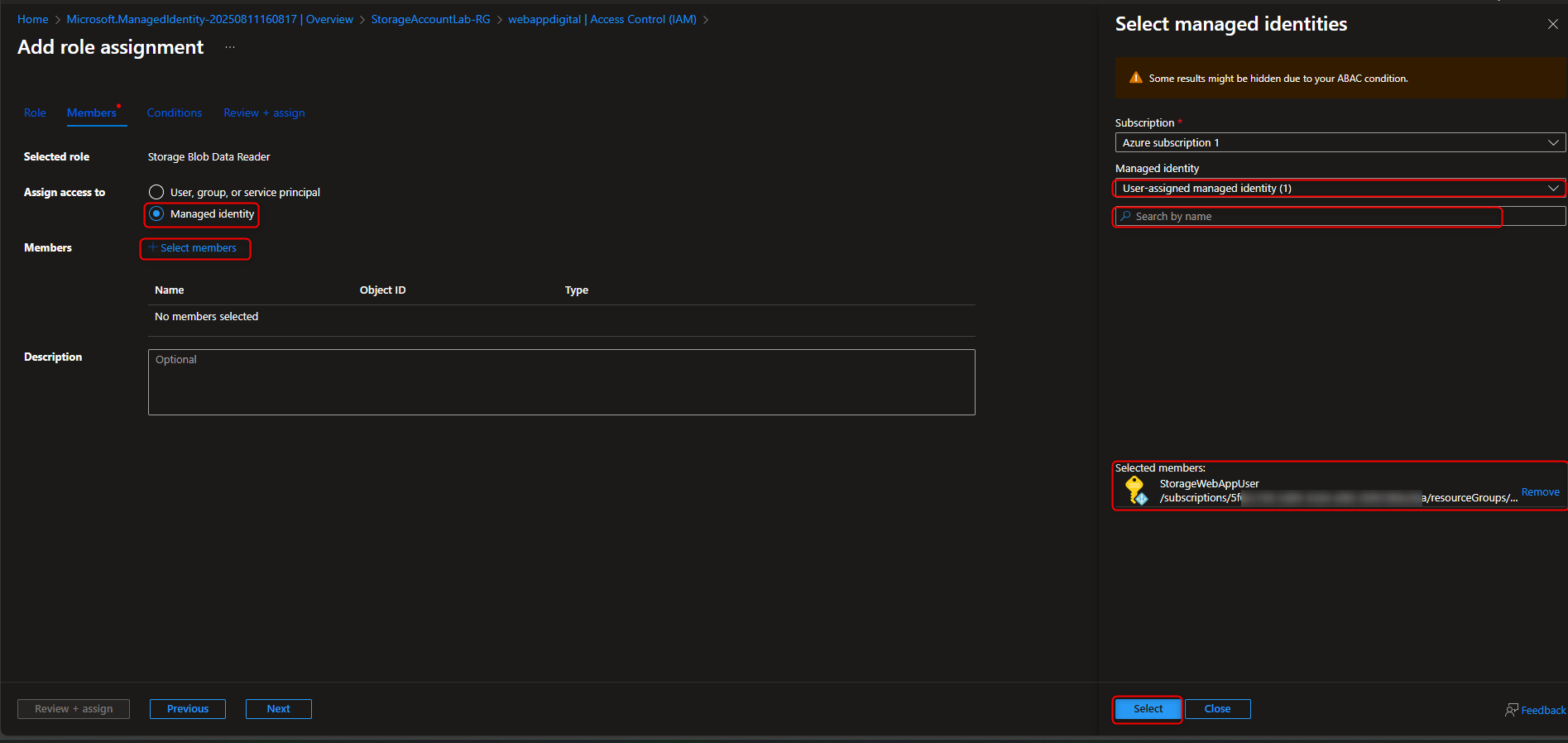
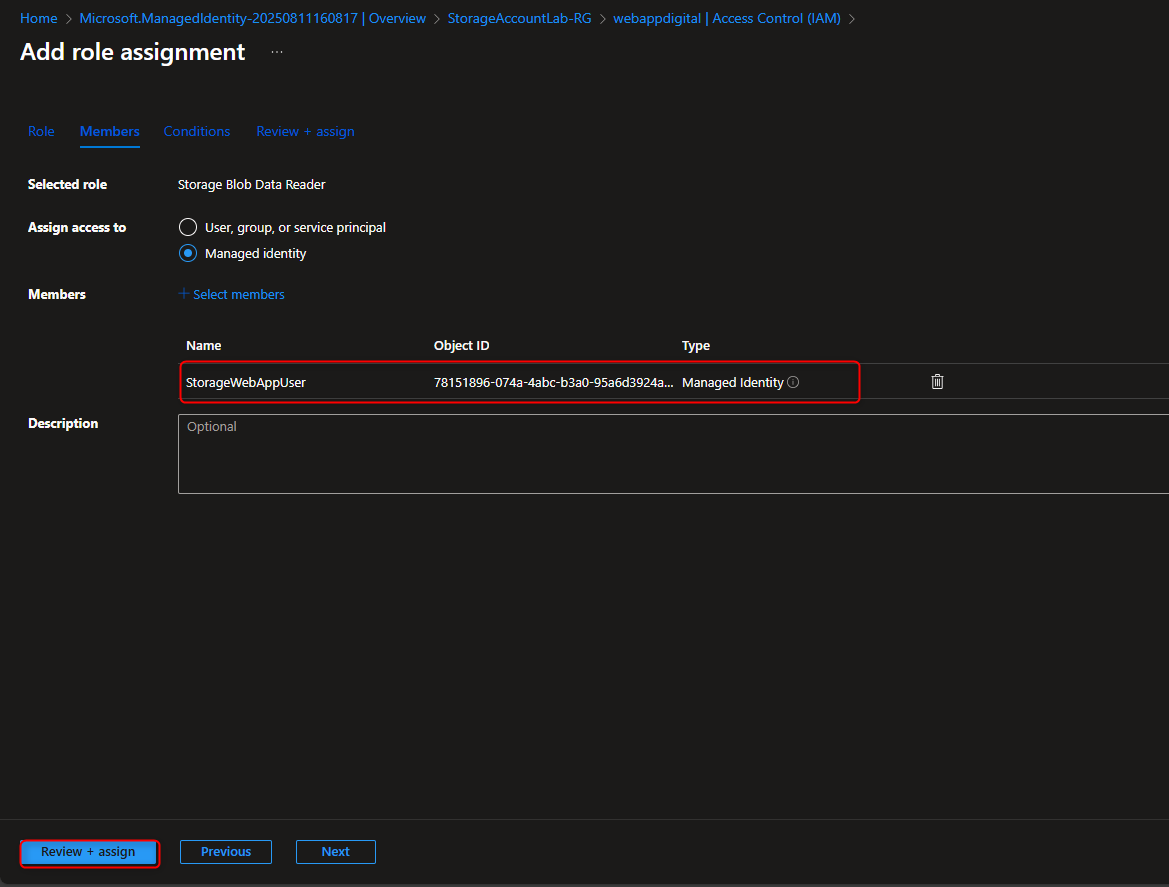
- Add Role Assignment to Managed Identity
Storage account -> Access Control (IAM) -> Add role assignment -> Storage Blob Data Reader -> Members -> Managed identity -> Select members -> [select your managed identity] -> Select -> Review + assign -> Review + assign
- Assign Key Vault Administrator Role to User
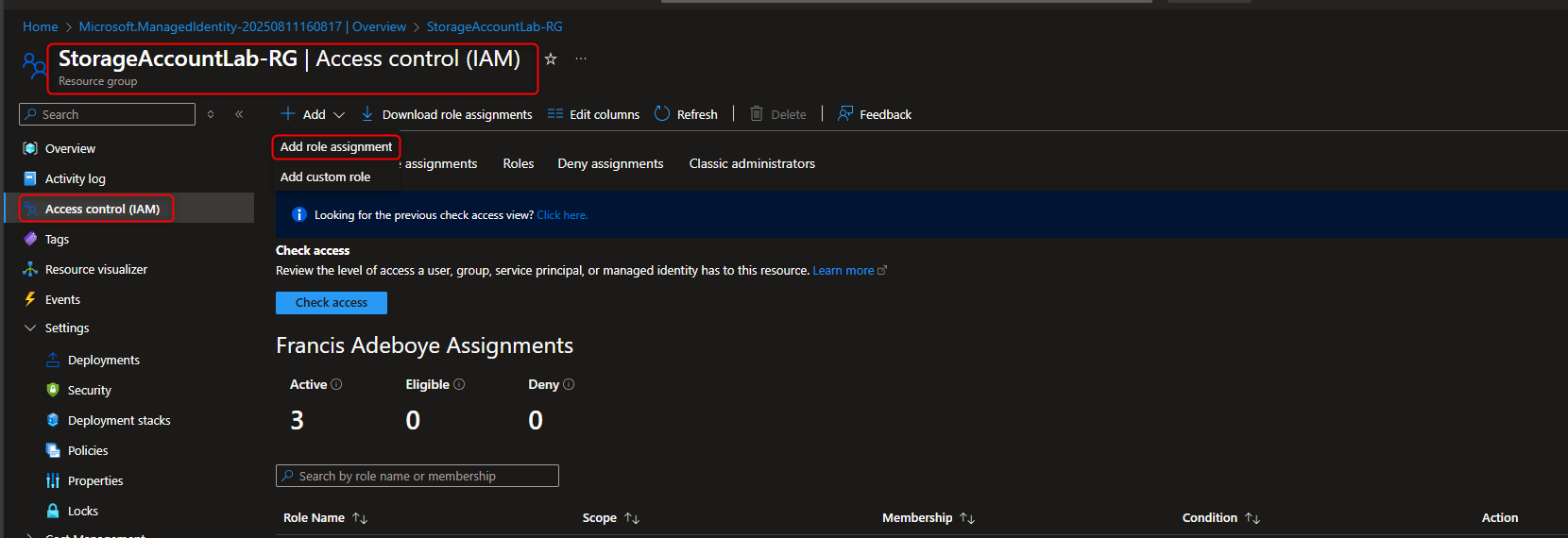
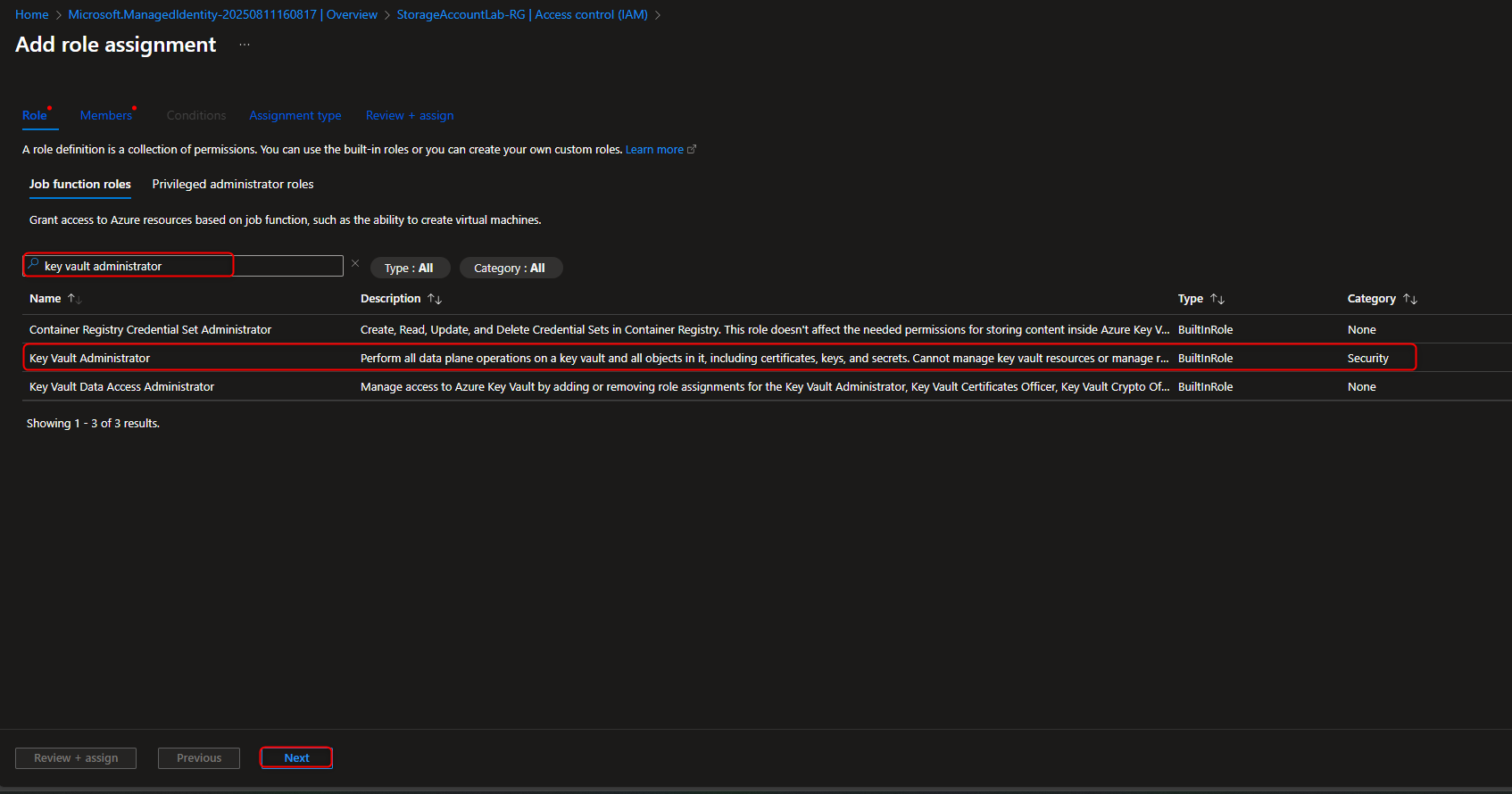
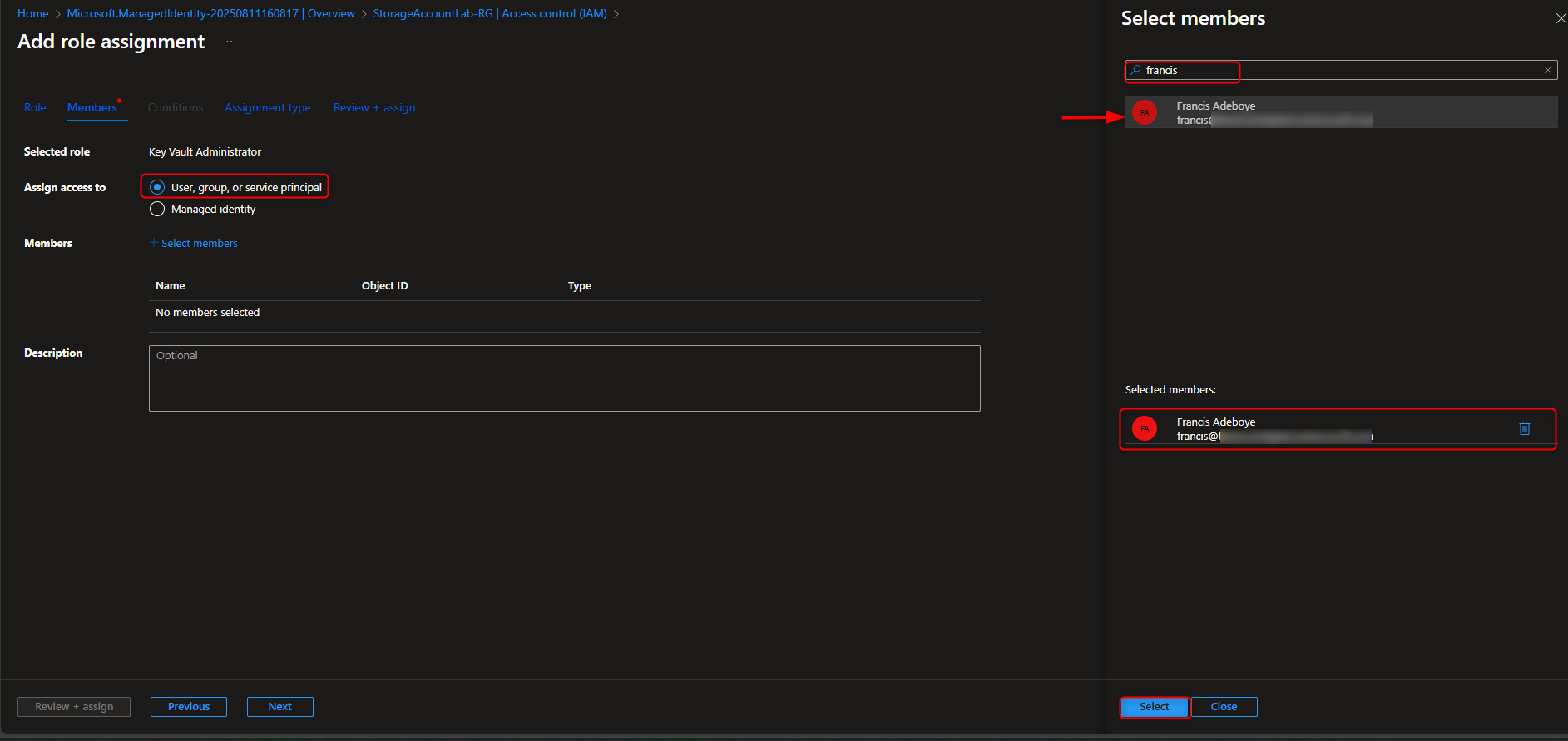
Resource groups -> [select your resource group] -> Access Control (IAM) -> Add role assignment -> Key Vault Administrator -> Members -> User, group, or service principal -> Select members -> [select your user account] -> Select -> Review + assign -> Review + assign (Activate Role)
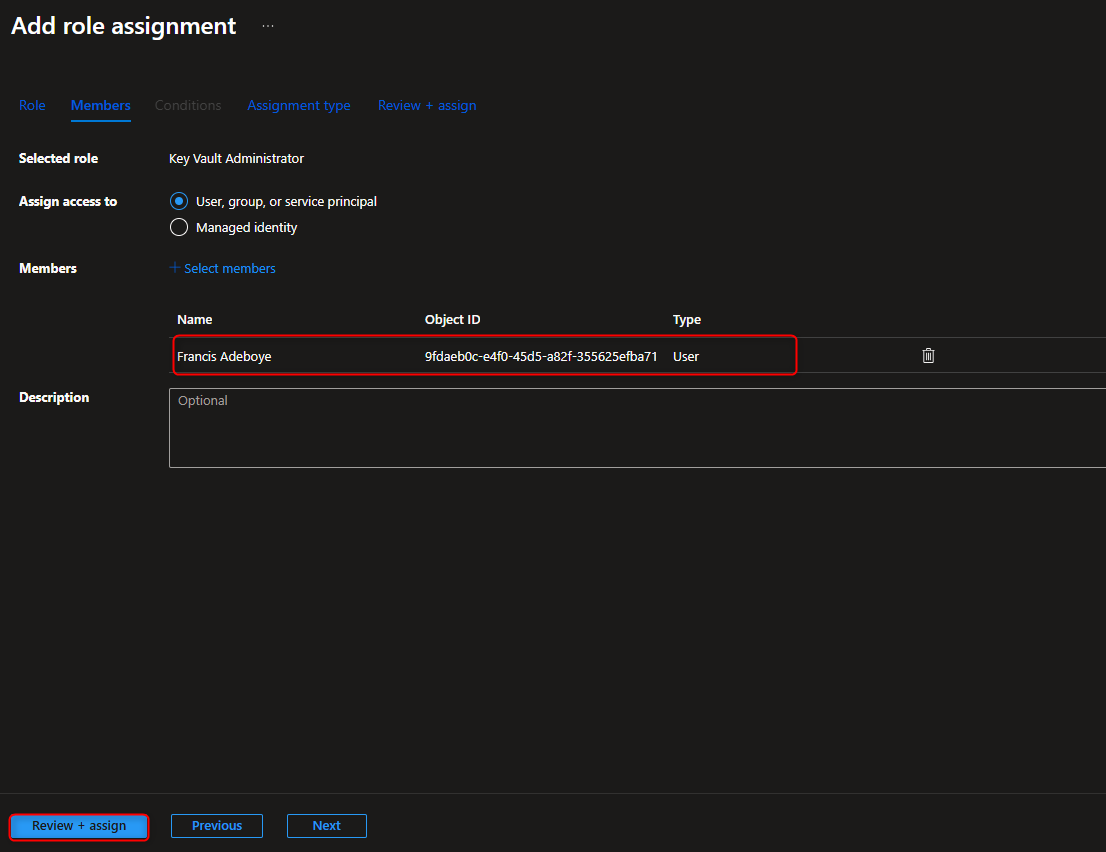
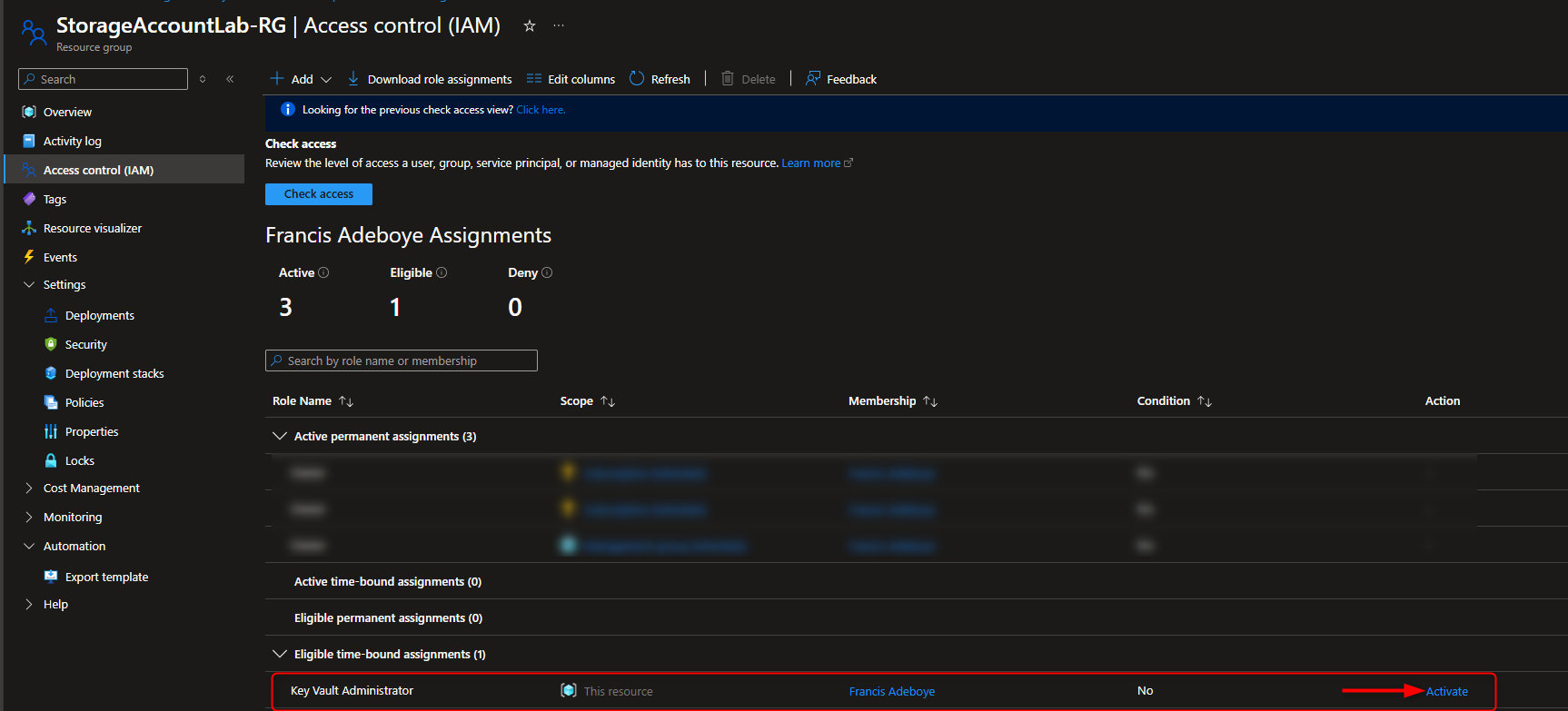
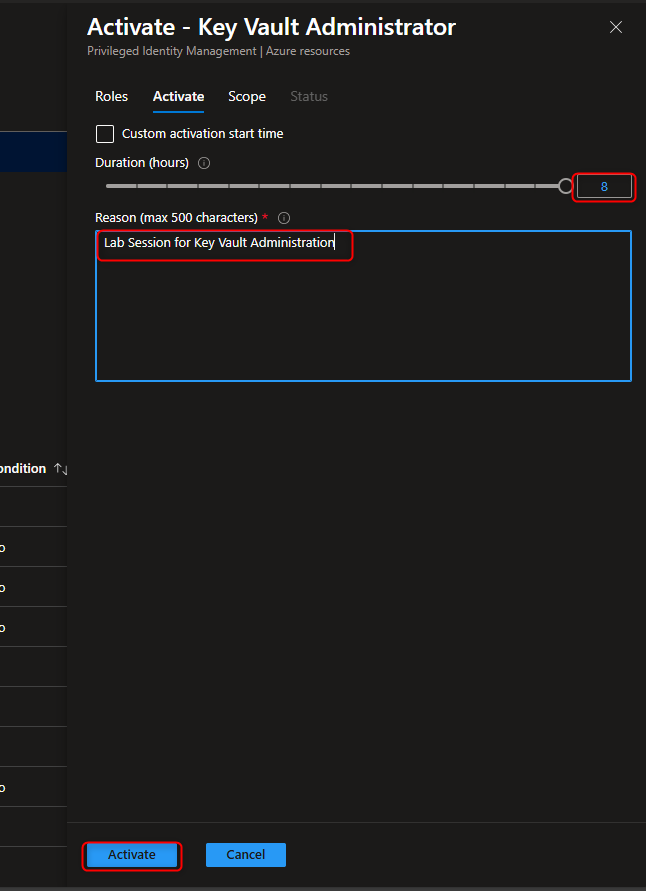
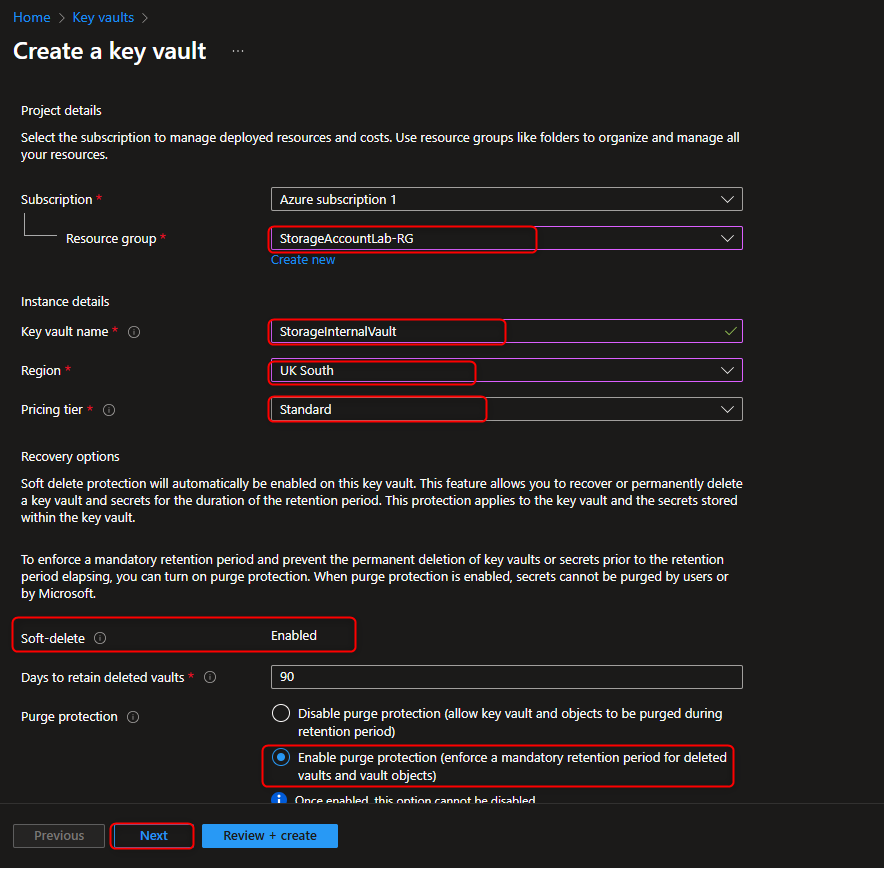
- Create Key Vault to Store Access Keys
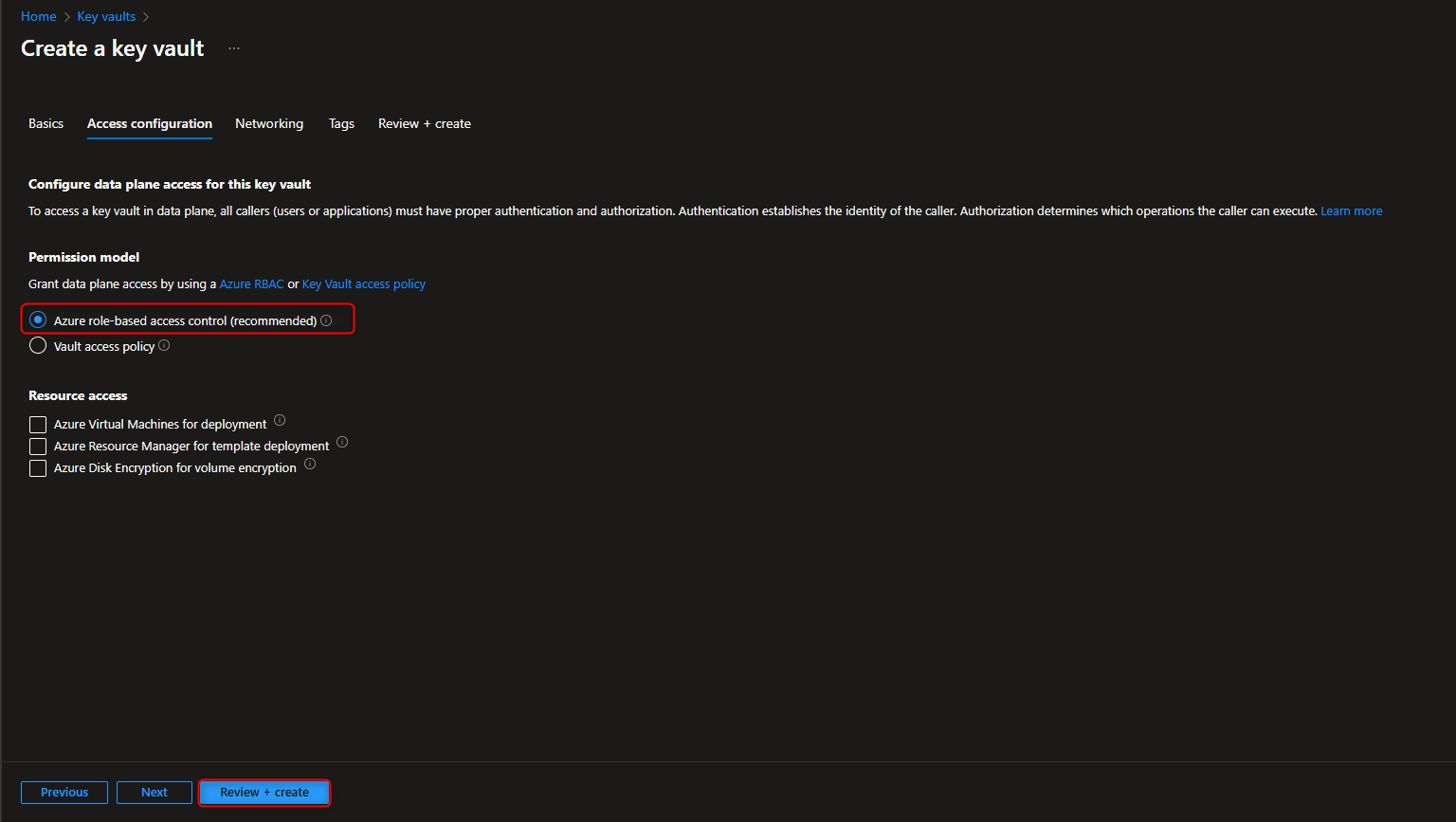
Key vaults -> Create -> [select your resource group] -> Name -> [provide a name] -> Access configuration -> Azure role-based access control (recommended) -> Review + create -> Create -> Go to resource -> Overview -> [verify soft-delete and purge protection are enabled]
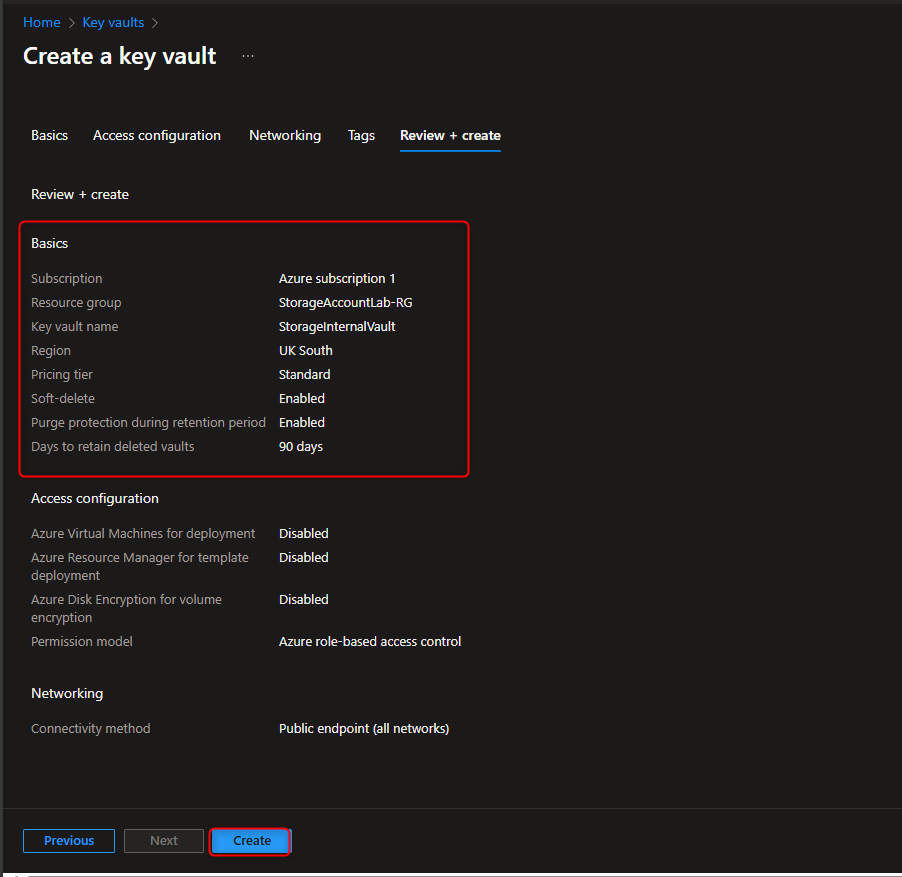
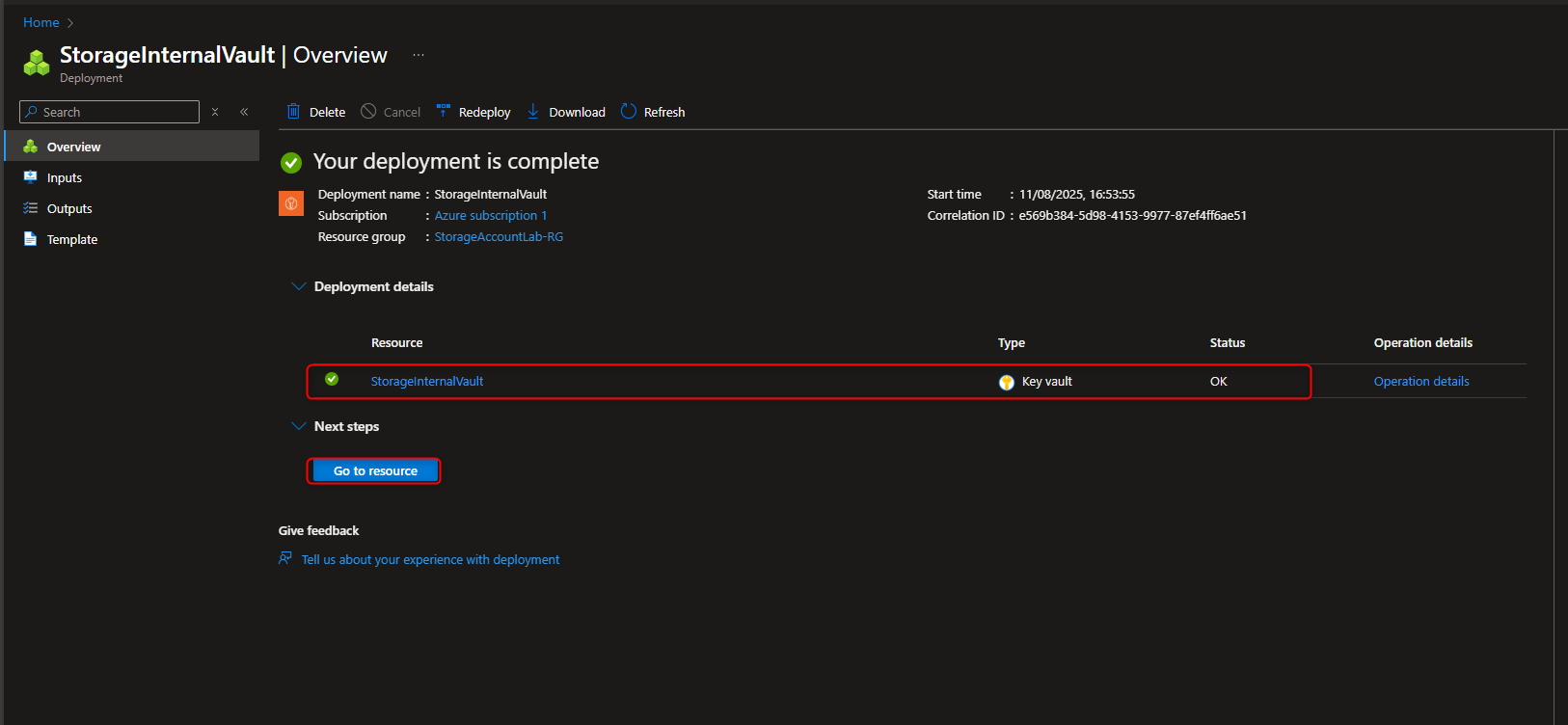
- Create a Customer Managed Key (CMK)
Key vault -> Objects -> Keys -> Generate/Import -> Name -> [name the key] -> Create
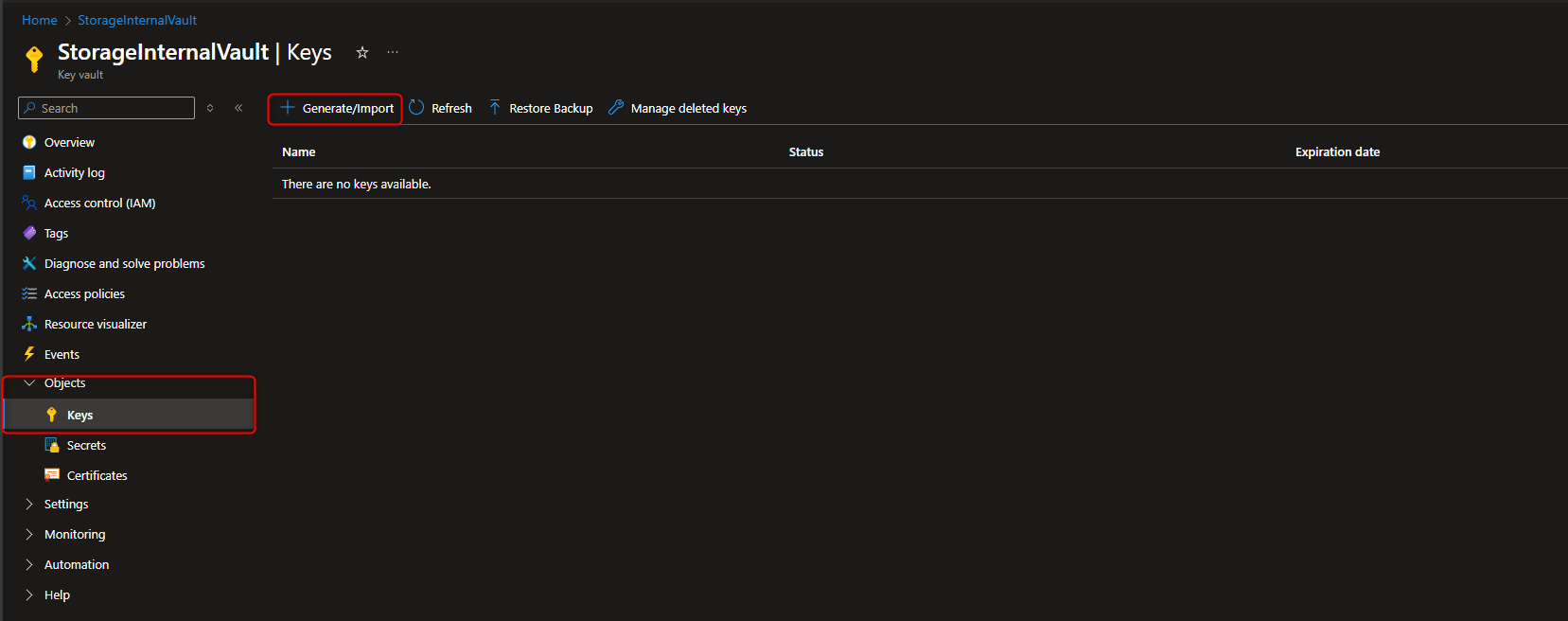
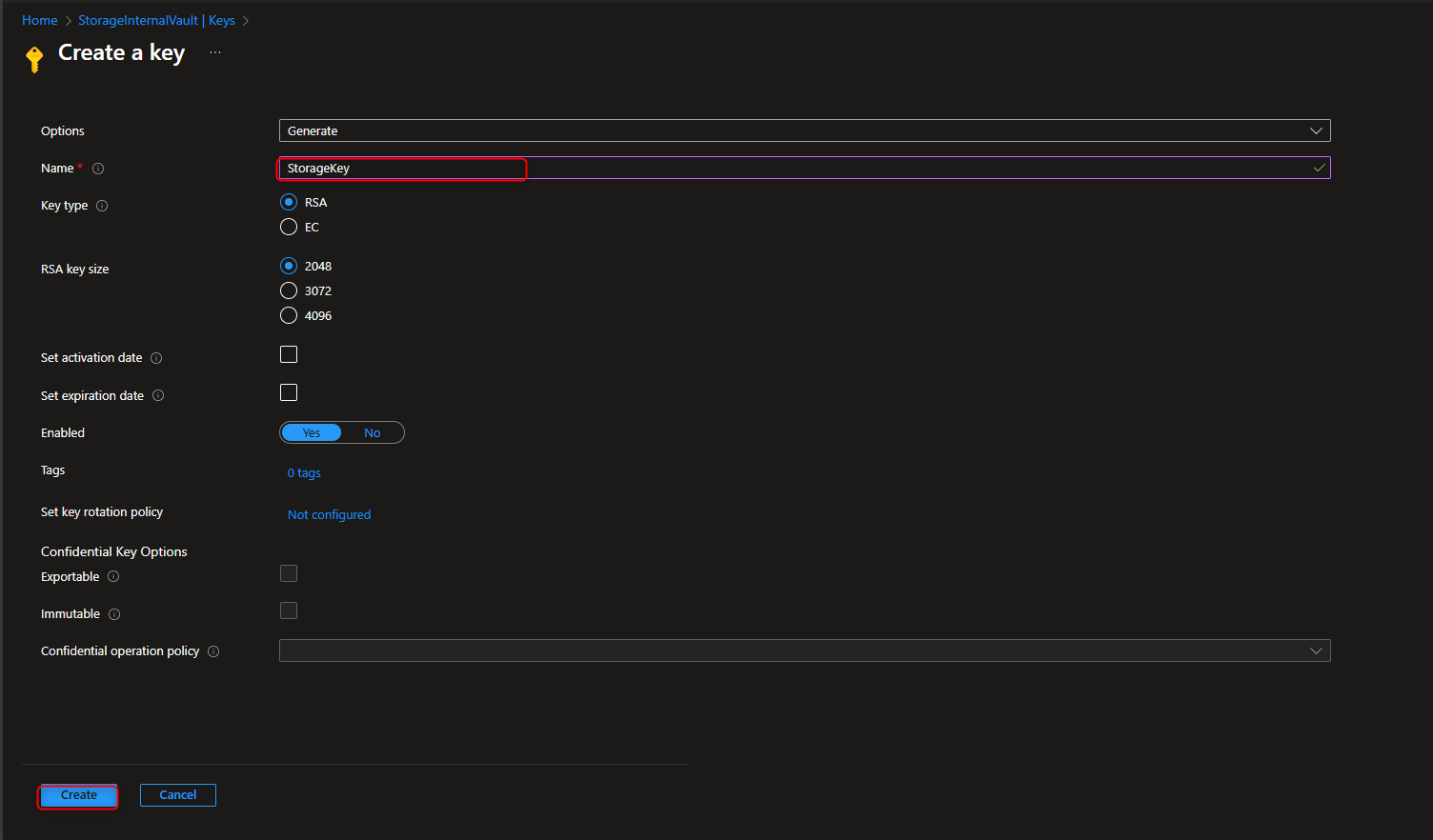
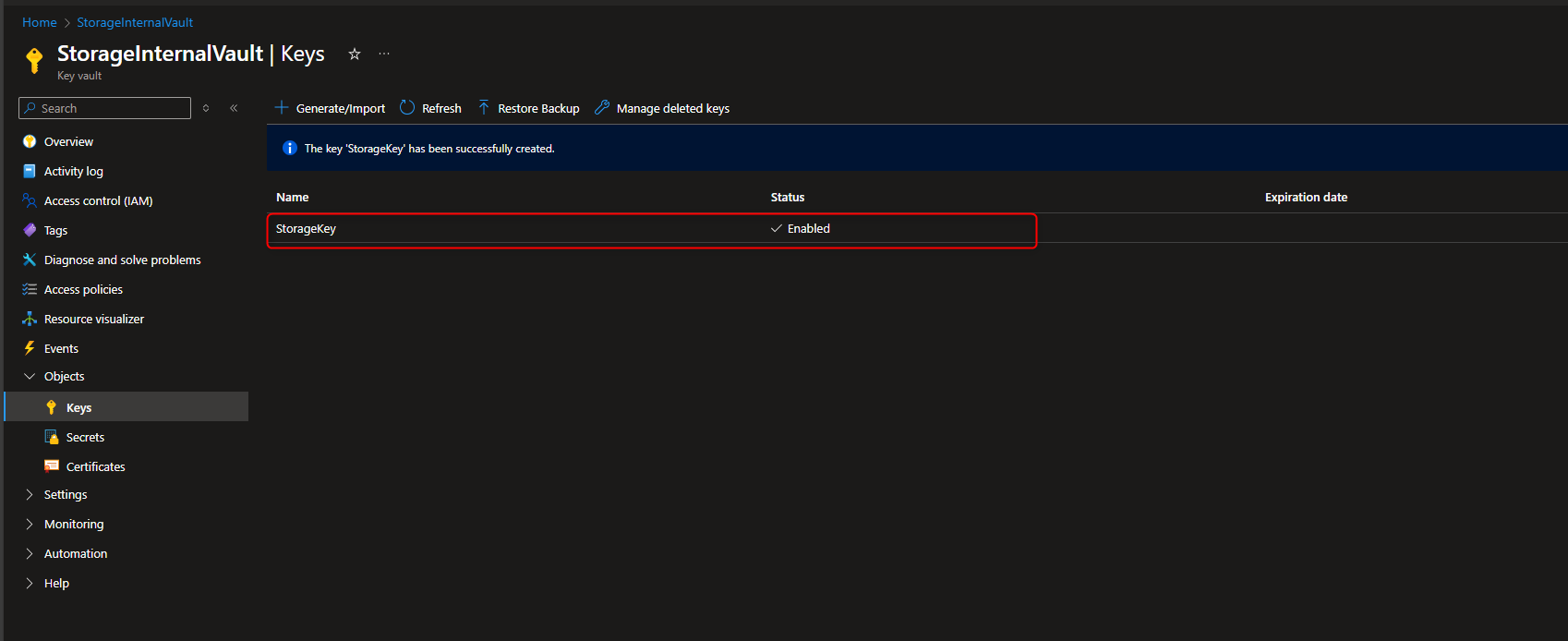
- Assign Key Vault Crypto Service Encryption User Role to Managed Identity
Resource groups -> [select your resource group] -> Access Control (IAM) -> Add role assignment -> Key Vault Crypto Service Encryption User -> Members -> Managed identity -> Select members -> [select your managed identity] -> Select -> Review + assign -> Review + assign
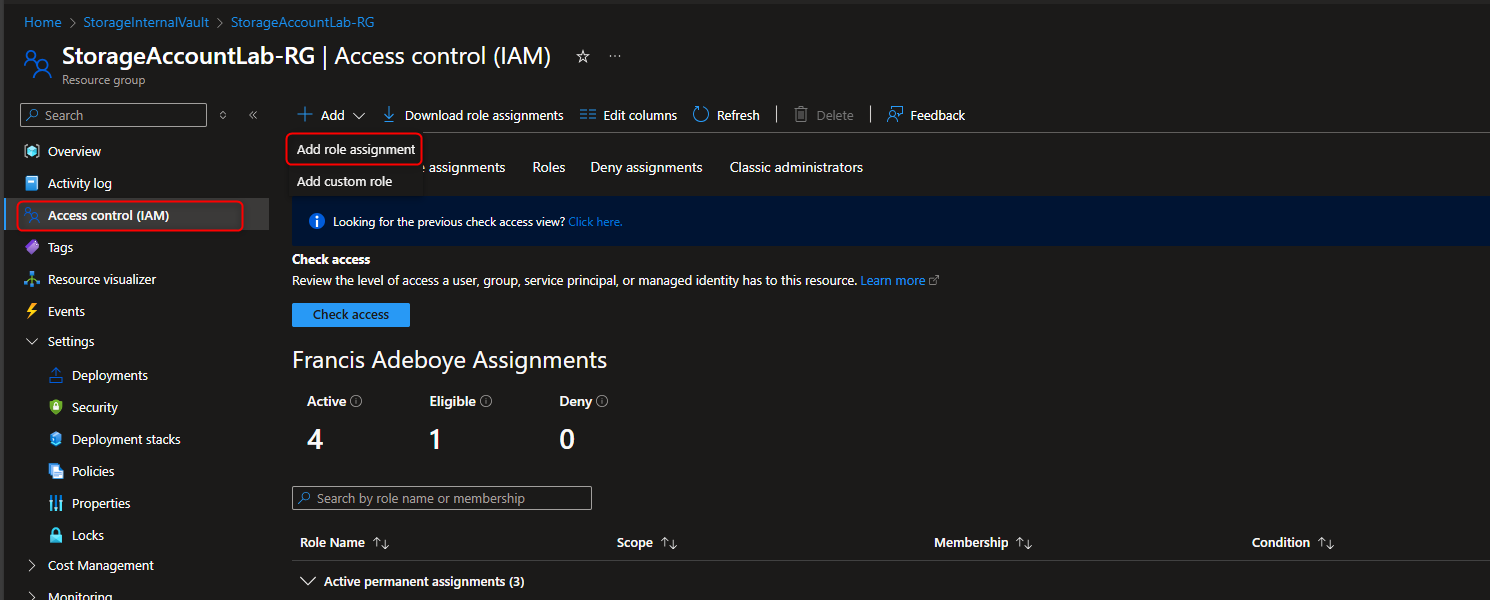
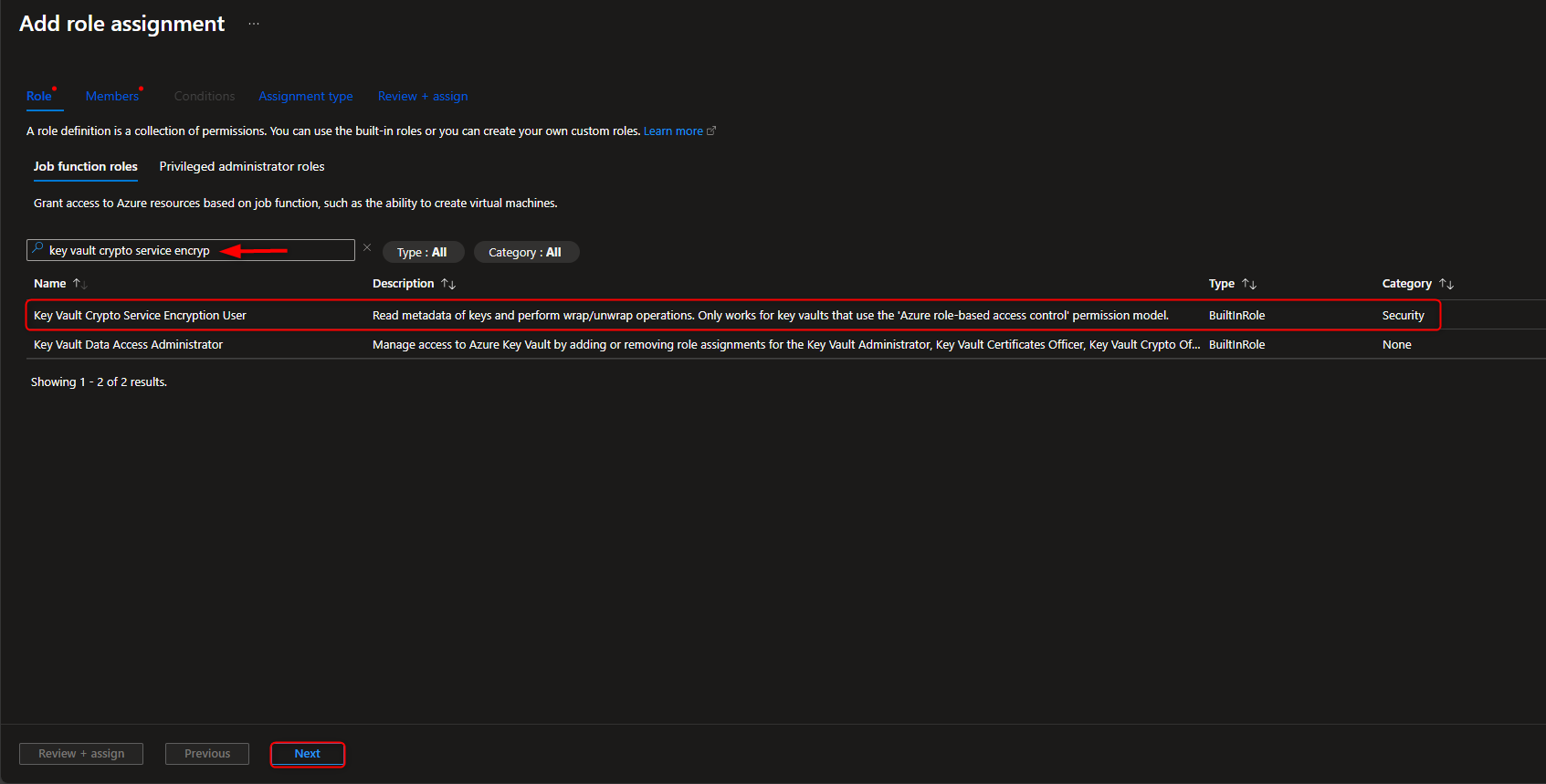
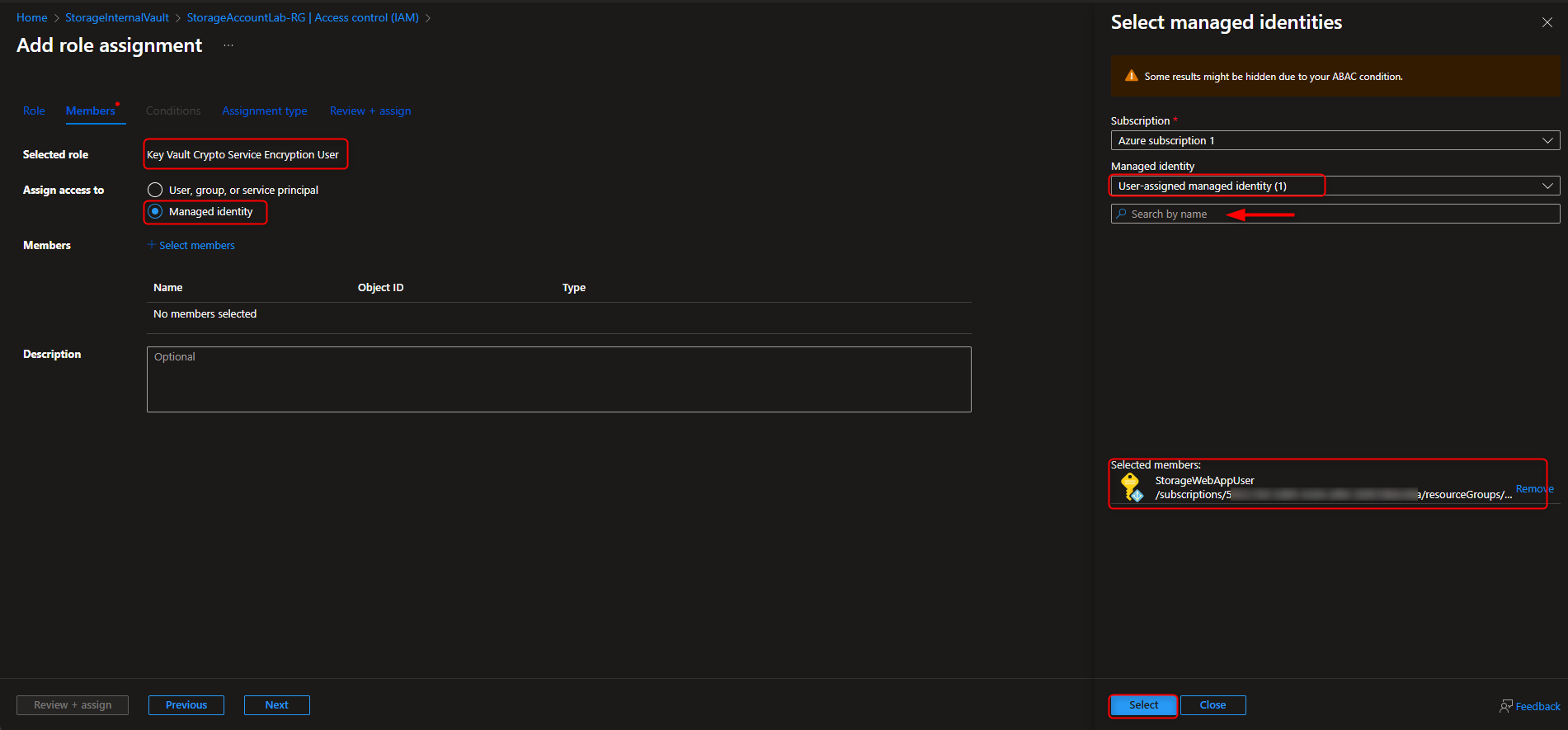
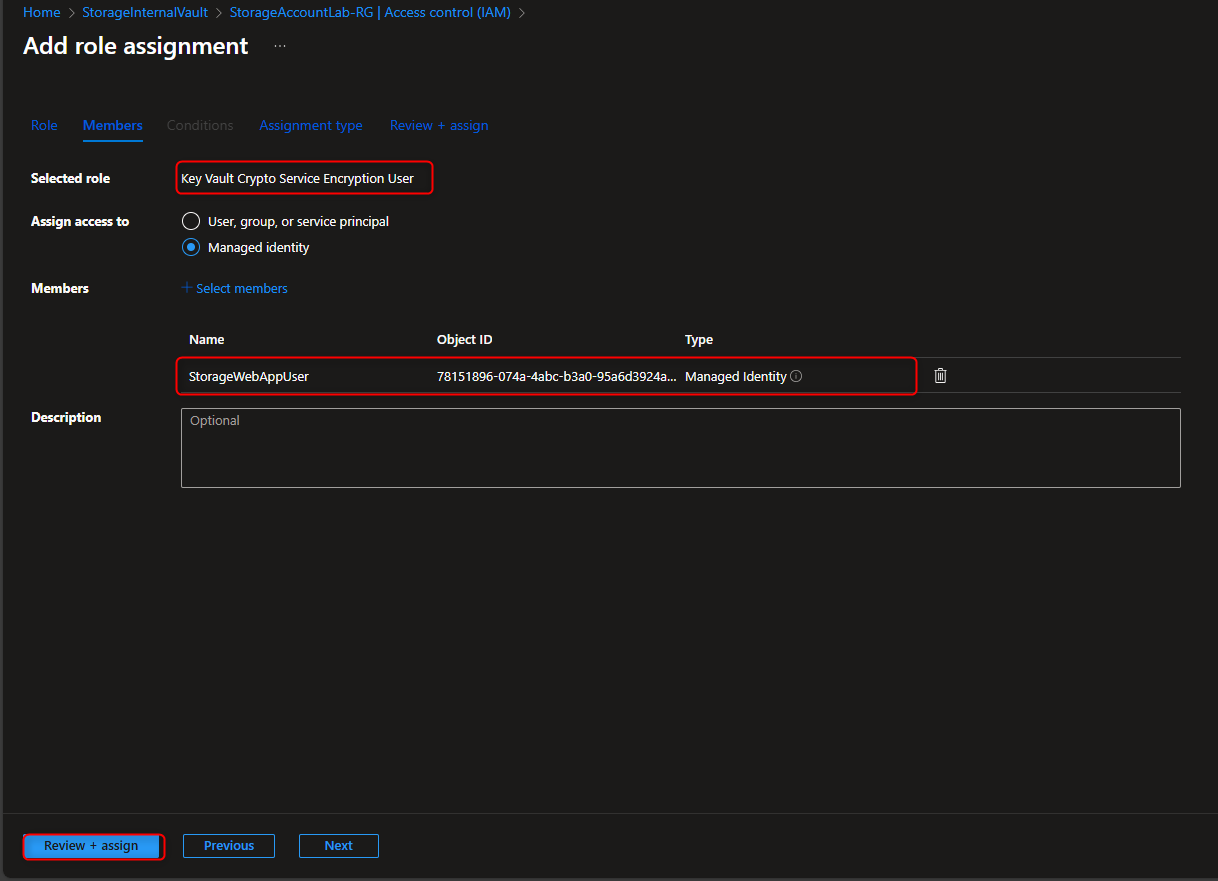
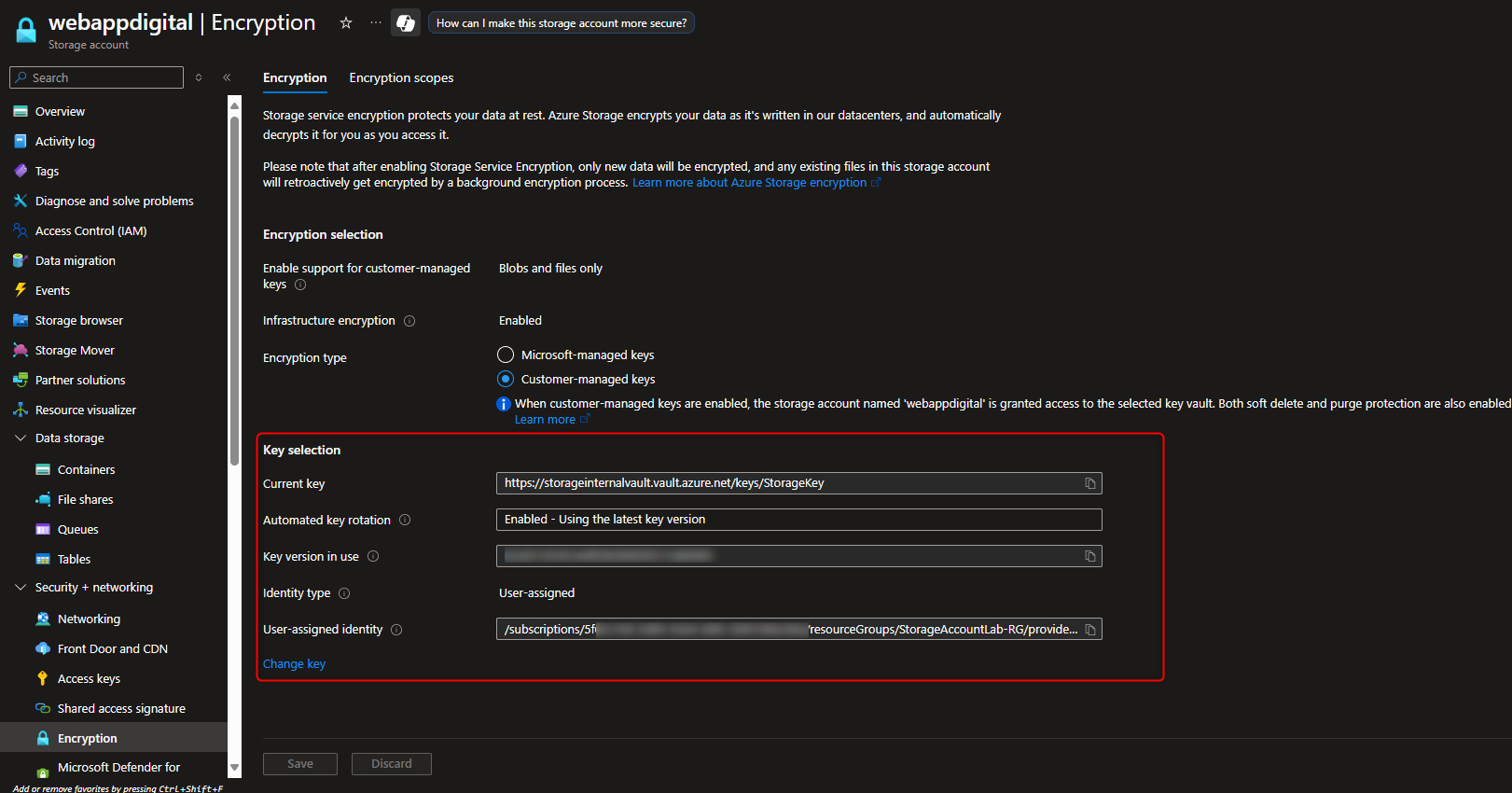
- Configure Encryption for Storage Account to use Customer-Managed Keys (CMK) in the Key Vault
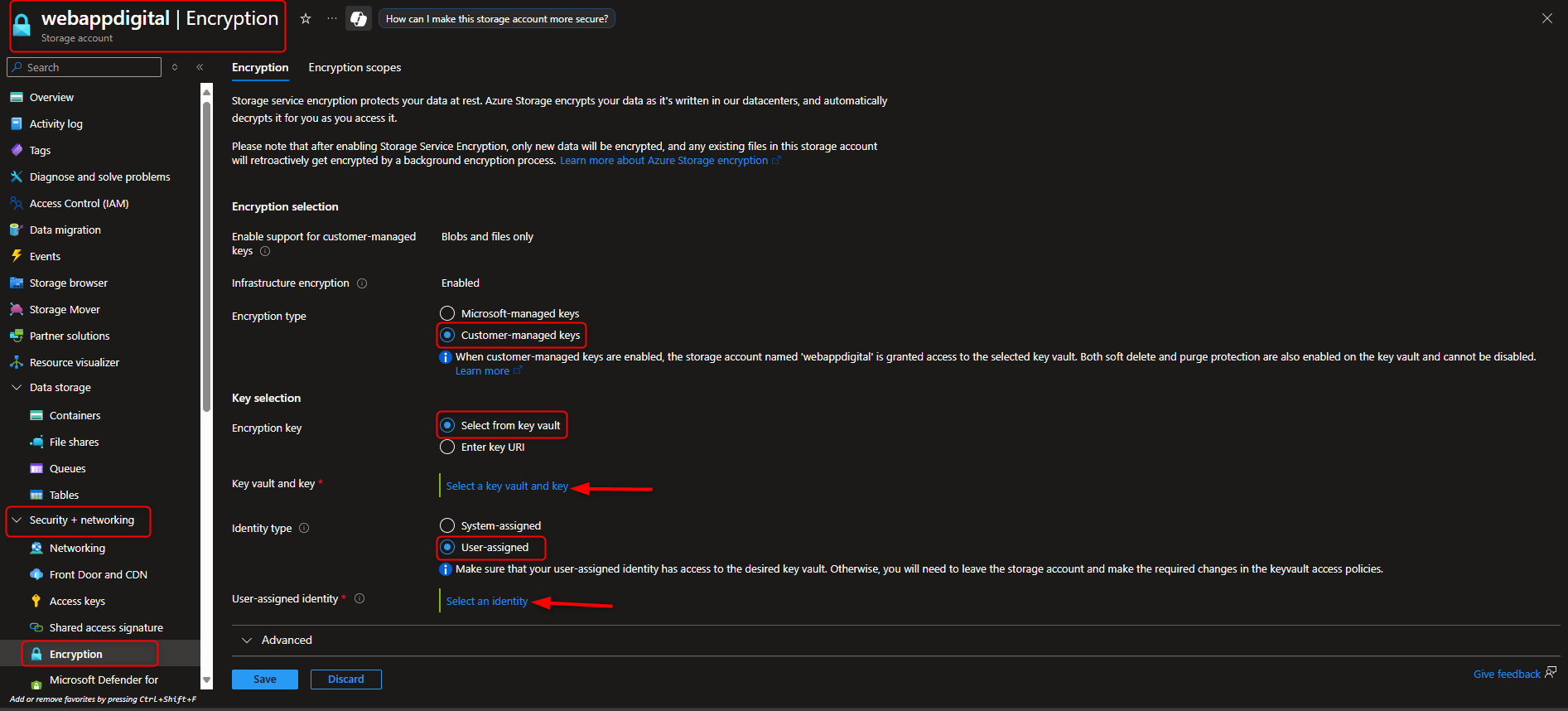
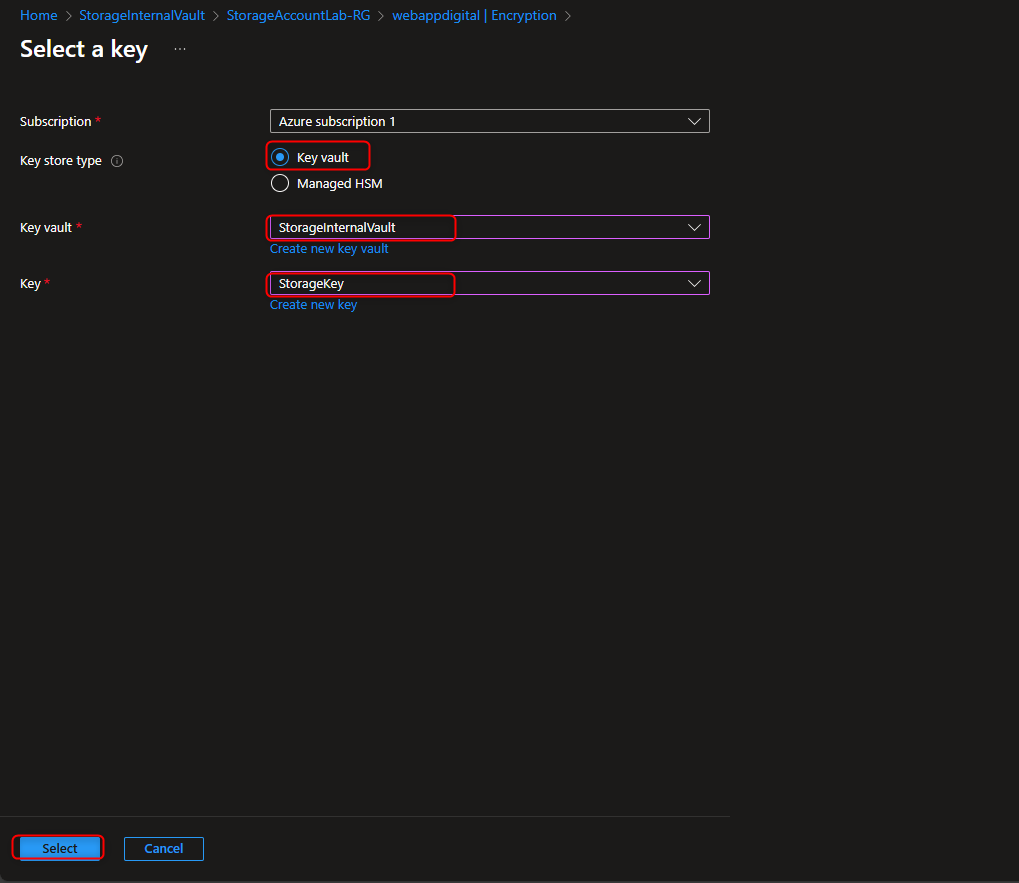
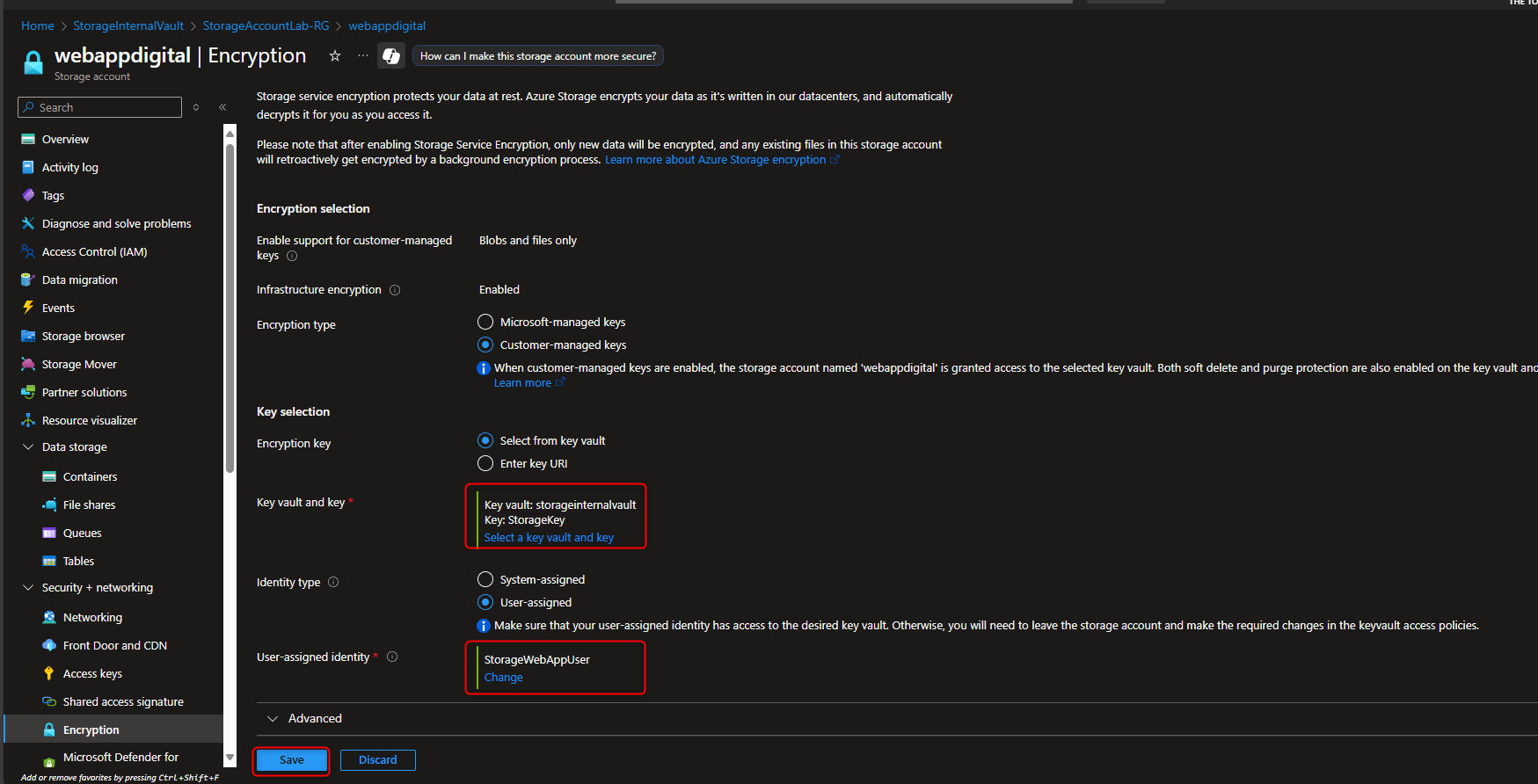
Return to storage account -> Security + networking -> Encryption -> Customer-managed keys -> Select a key vault and key -> [select your key vault and key] -> Identity type -> User-assigned -> Select an identity -> [select your managed identity] -> Add -> Save
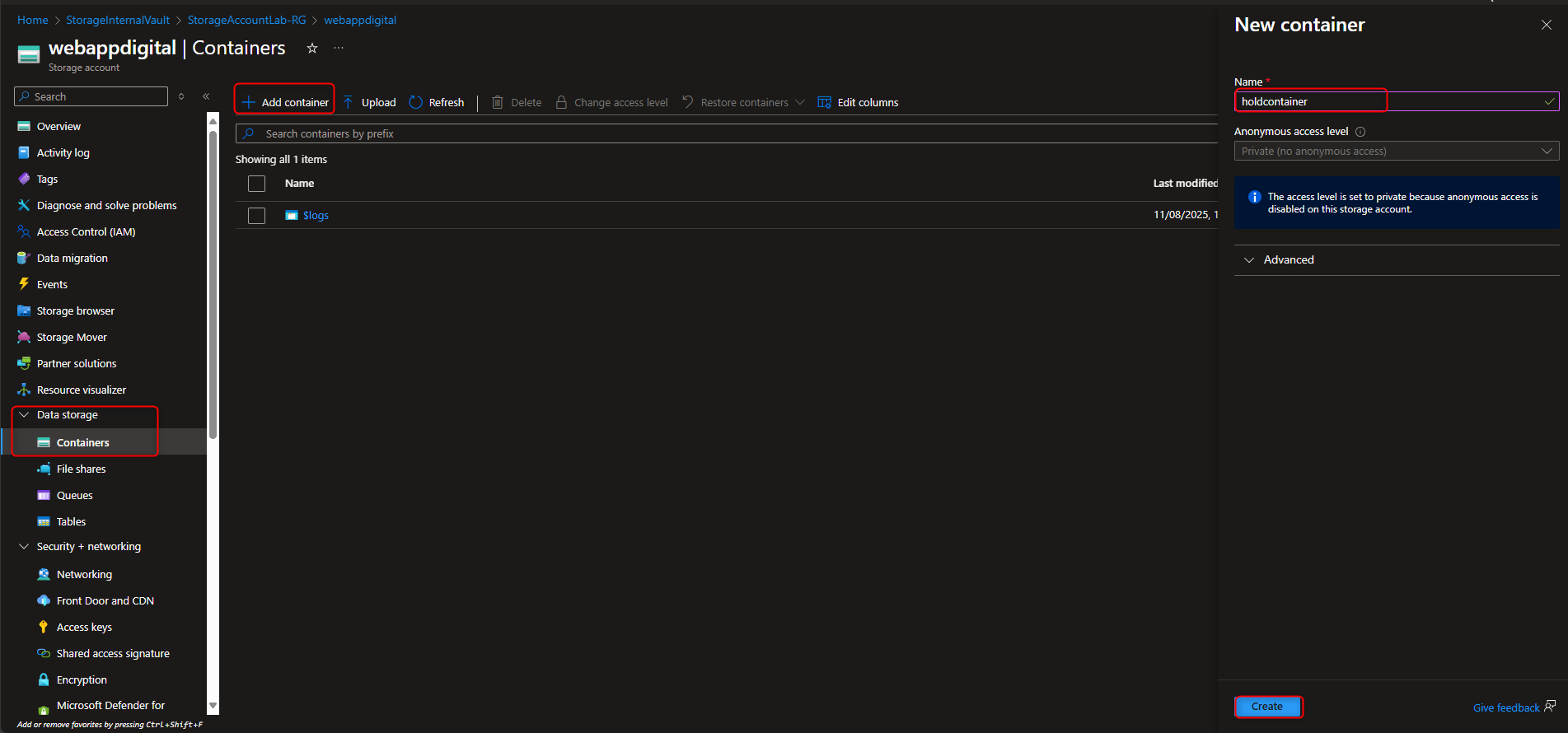
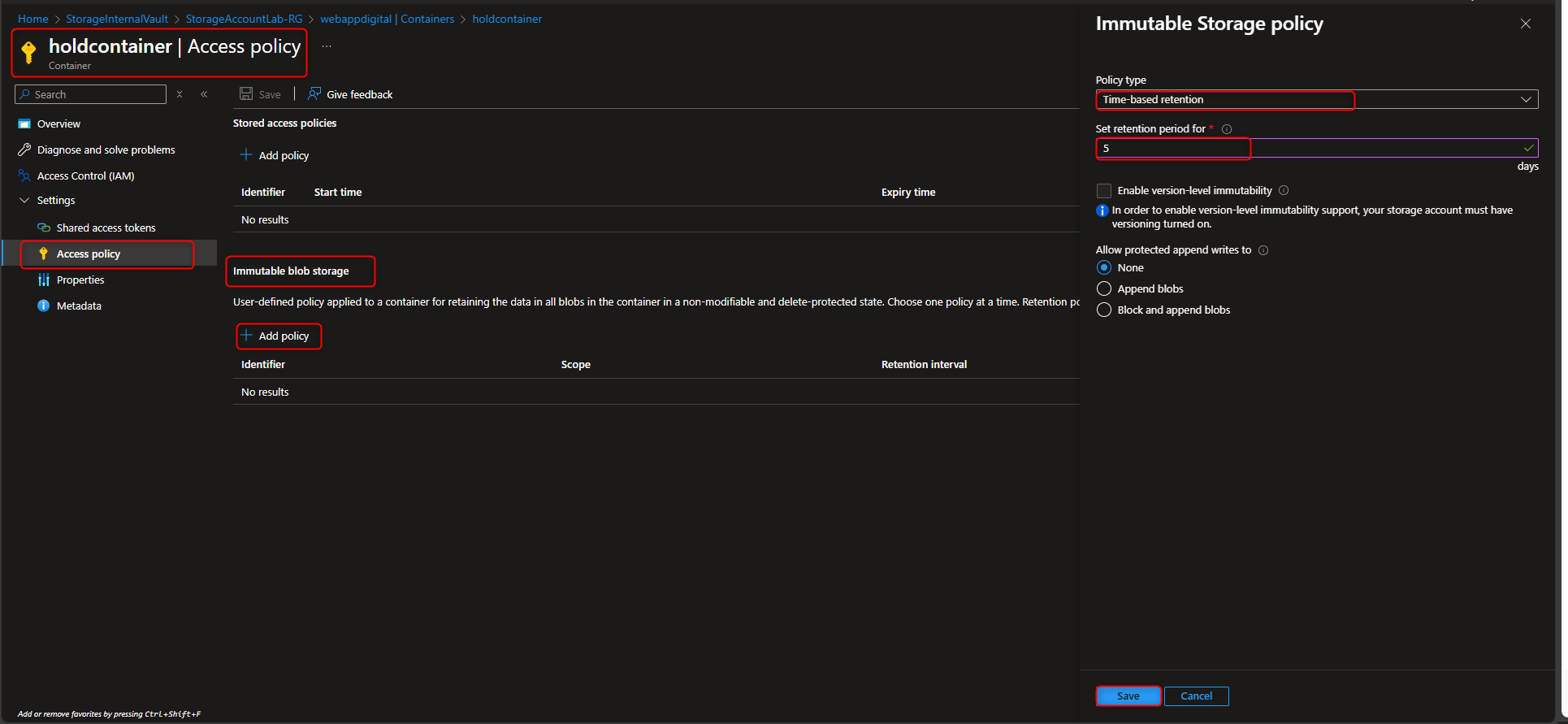
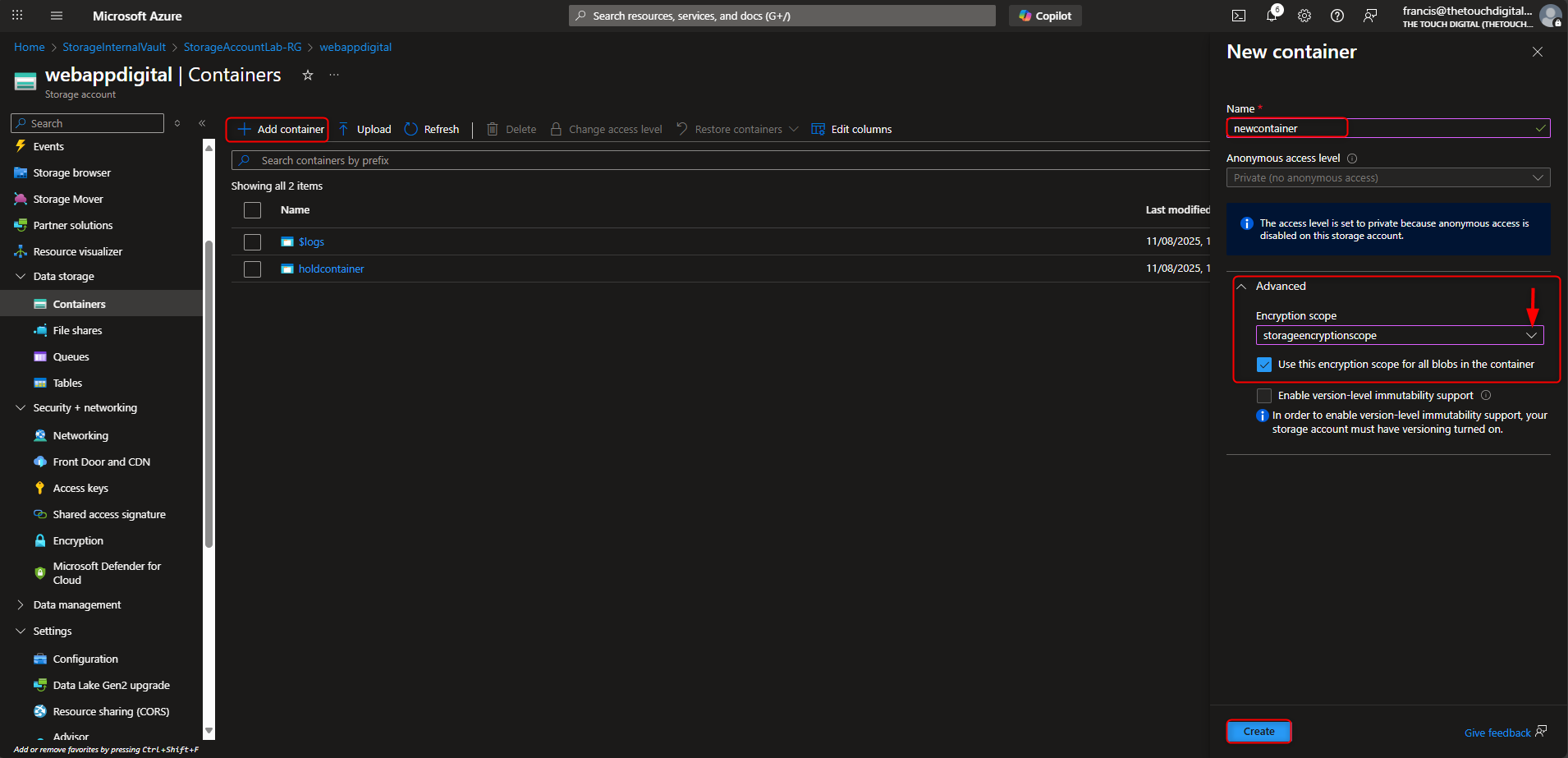
- Configure an Immutable Policy (Time-based Retention) and Encryption Scope
Storage account -> Data storage -> Containers -> Create container -> hold -> Create -> [upload a file] -> Settings -> Access policy -> + Add policy -> Policy type -> time-based retention -> Retention period -> 5 days -> Save -> [try to delete file] -> [verify “failed to delete blobs” message]
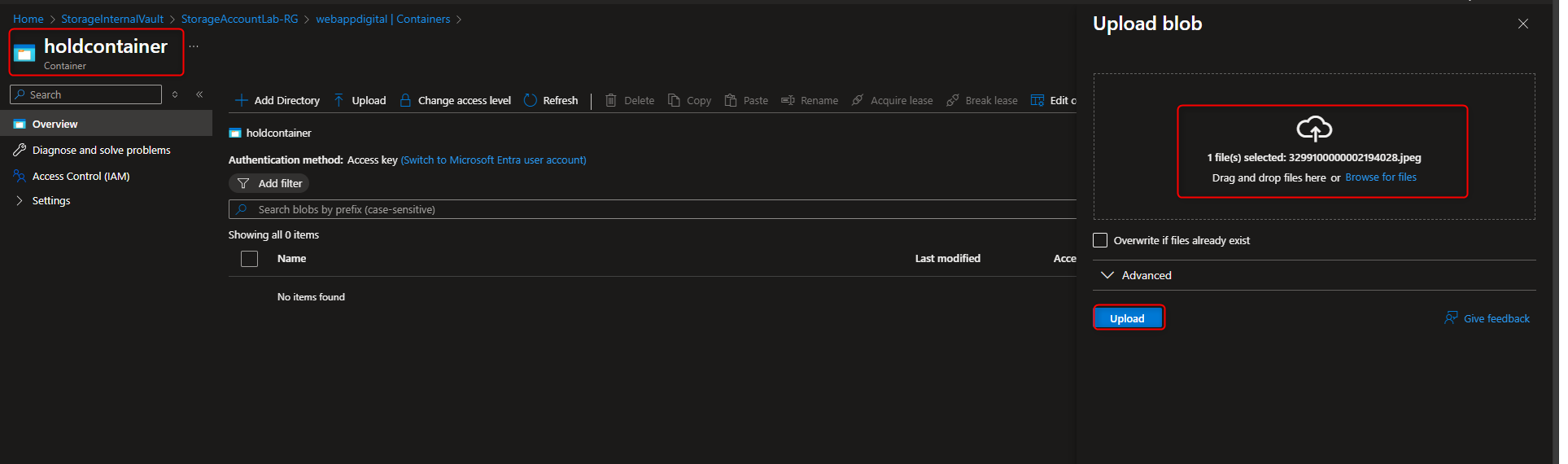
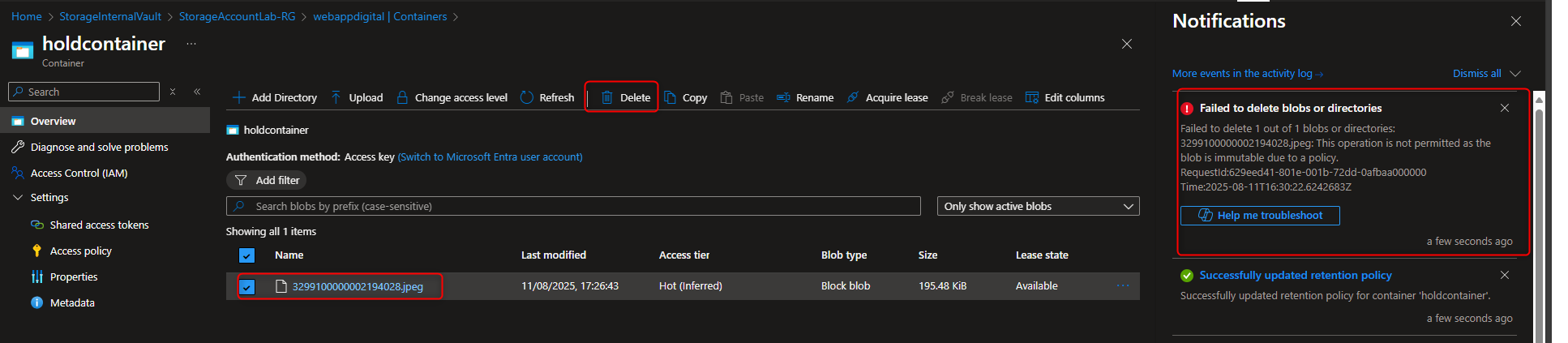
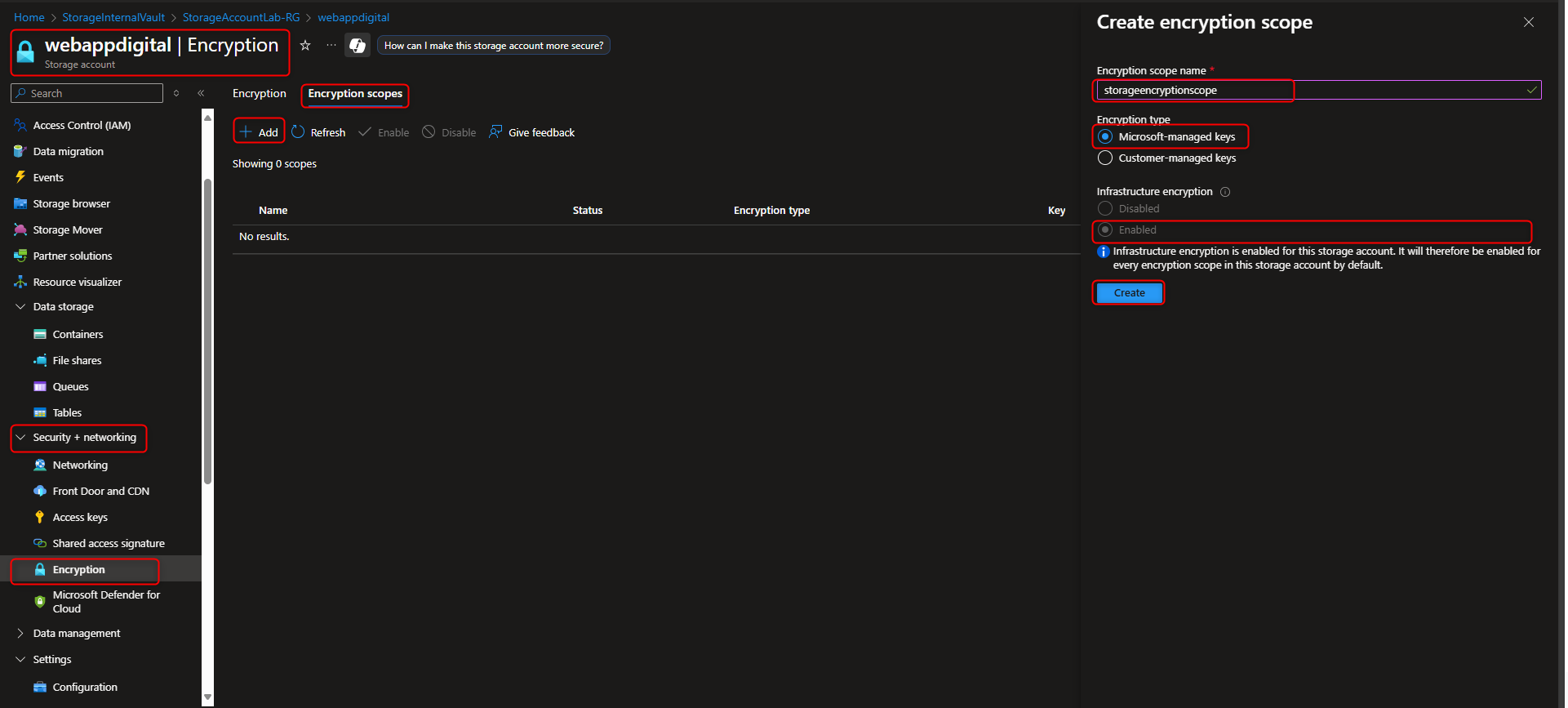
- Create and Apply Encryption Scope that enables infrastructure encryption to storage account
Storage account -> Security + networking -> Encryption -> Encryption scopes -> Add -> Name -> [enter a name] -> Encryption type -> Microsoft-managed key -> Infrastructure encryption -> Enable -> Create -> [return to storage account] -> Create a new container -> Advanced -> Encryption scope -> [select your new scope]
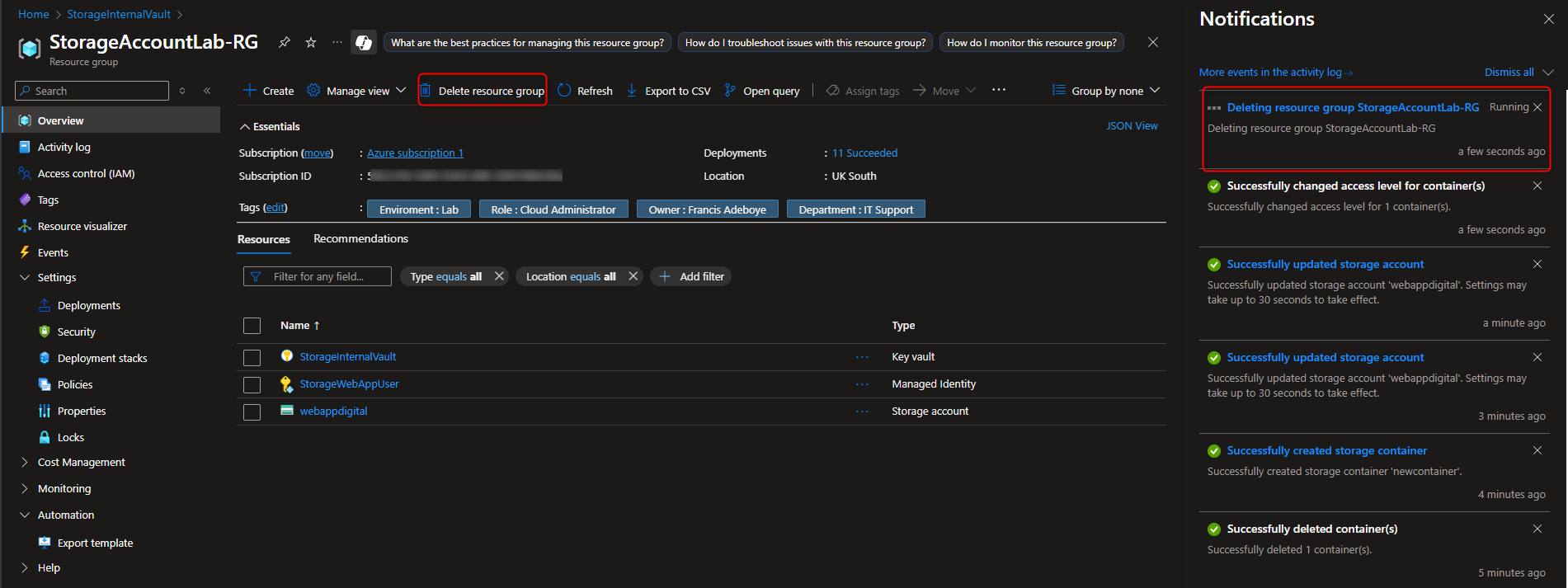
- Clean up resources
Resource groups -> [select your resource group] -> Delete resource group -> [type the resource group name] -> Delete
Conclusion
Across these five tasks, we’ve explored how Azure Storage can be tailored to meet a wide range of enterprise needs—from public content delivery and internal document protection to secure app development and departmental file sharing. Each scenario demonstrates how thoughtful configuration—whether through redundancy models like RA-GRS and ZRS, access control via RBAC and managed identities, or data protection features like snapshots, versioning, and immutability—can transform storage from a passive resource into a strategic asset.
By aligning storage architecture with business goals, security standards, and operational workflows, we not only meet technical requirements—we build solutions that scale, adapt, and protect. Whether you’re designing for global reach or internal governance, Azure provides the flexibility and control to do it right.